In my previous post “Pentestit Lab v10 - Captcha Token (7/13)”, we pivoted further into the internal network via an SSL Tunnel to access the Captcha Machine, exploited a Command Injection vulnerability, established a VPN connection via SSH to gain a foothold on the internal network, and found our seventh token. Today we will continue our pivot into the internal network and attack the News Machine - which will include the following:
- Fingerprinting the News Web App
- Exploiting Old Login Functionality
- Finding the News Token
Fingerprinting the News Web App:
Alright, our first step would be to fingerprint the machine. So let’s look back at our Nmap scans - which you should have already done after gaining initial access to the gw machine - and see what the machine is running.
Nmap scan report for 192.168.0.5
Host is up (0.0016s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u6 (protocol 2.0)
80/tcp open http nginx
Service Info: OS: Linux; CPE: cpe:/o:linux:kernel
Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.62 seconds
Okay so another Nginx HTTPD Server is running on TCP/80 - we can already assume with confidence that there is a website running locally.
So as we have done before, let’s establish an SSH Tunnel to access the website.
root@kali:~# ssh -L 8080:192.168.0.5:80 e.lindsey@192.168.101.9
e.lindsey@192.168.101.9's password:
Linux tl10-ssh 3.2.0-4-amd64 #1 SMP Debian 3.2.82-1 x86_64
Last login: Thu Jan 26 01:37:14 2017 from 10.10.197.130
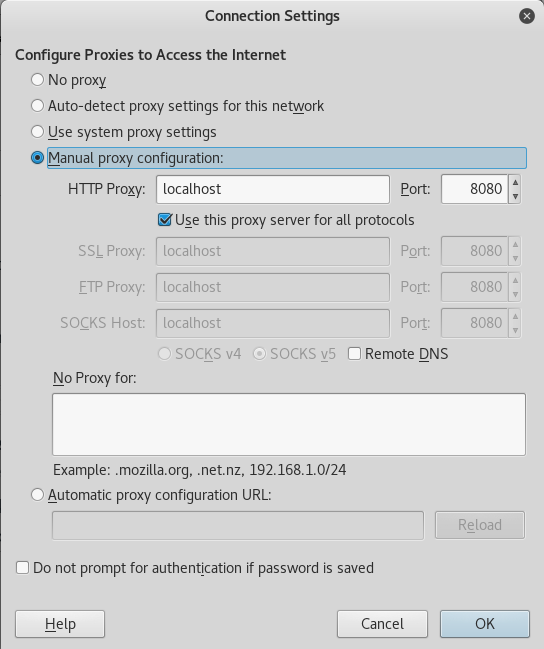
Also make sure you have the proxy configured properly!
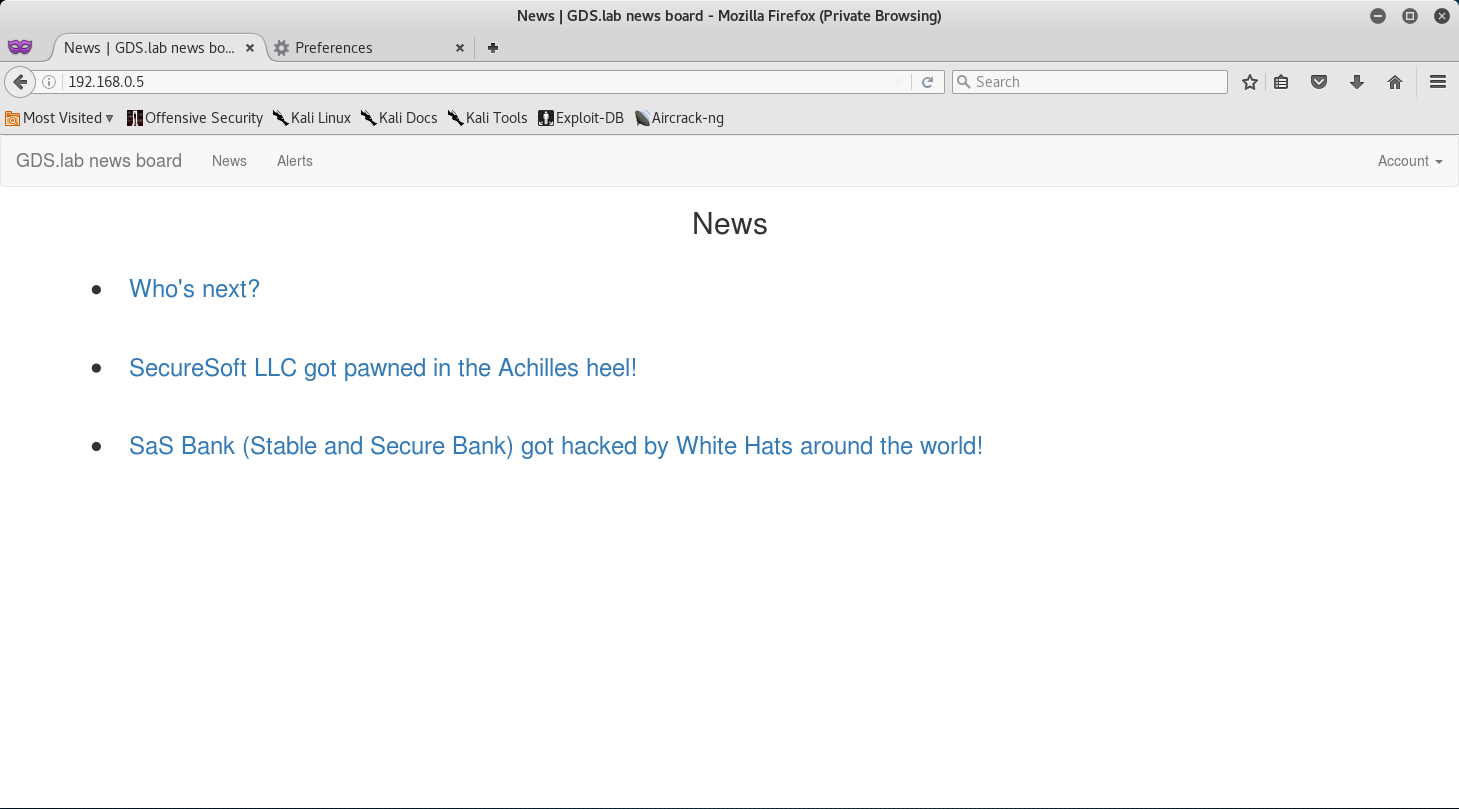
Once you have verified that the SSH Tunnel is up and running, and that the proxy is configured properly, we can go ahead and browse to the News Machine via the IP of 192.168.0.5.
Since we now have access to the site let’s do some initial reconnaissance to find anything of interest.
I saw that there is an Account drop down with a login. So I decided to follow that and see where it leads to.
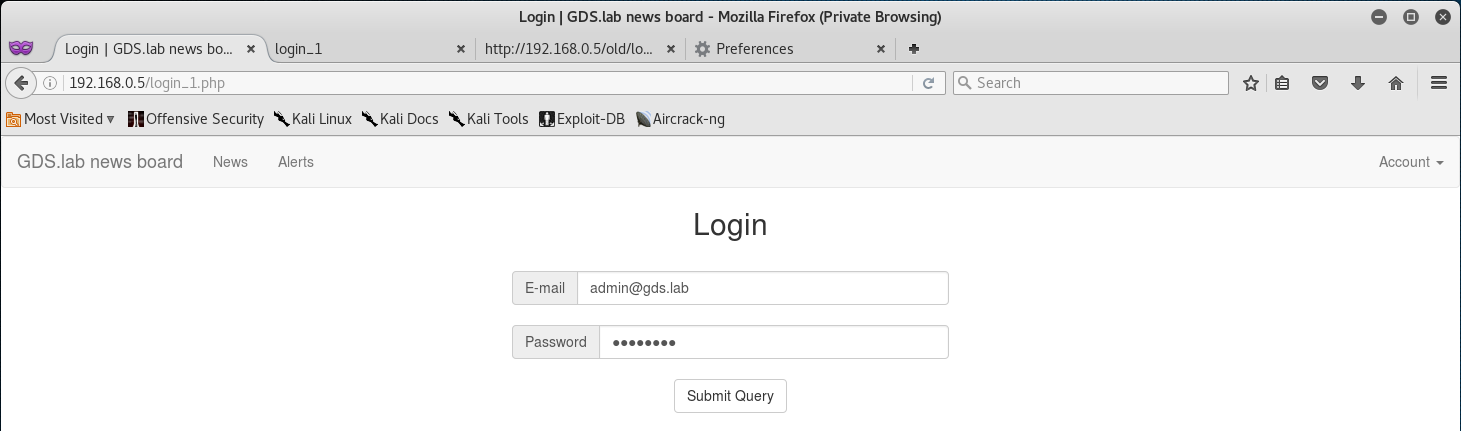
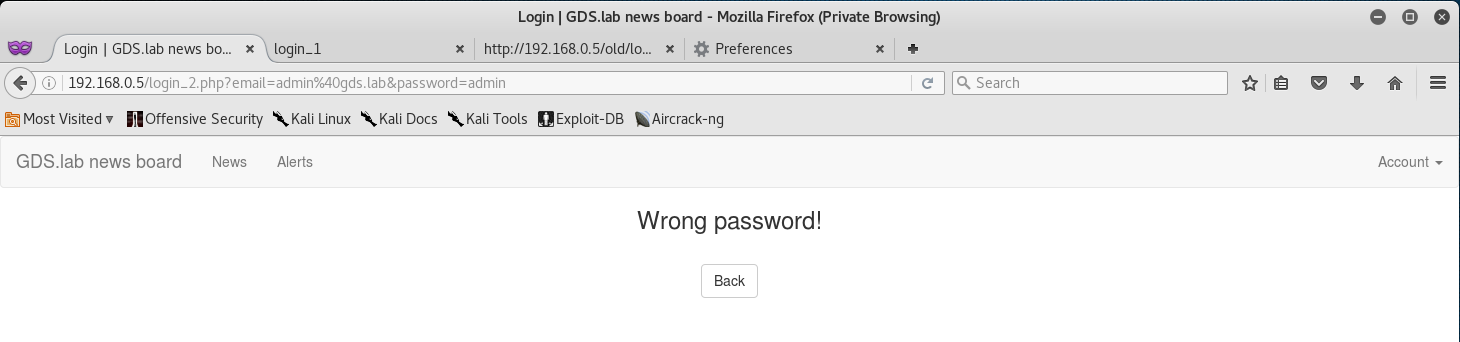
I decided to try and exploit some low hanging fruit and attempted a login with admin@gds.lab:admin.
We can see that the user admin exists, but the password is wrong!
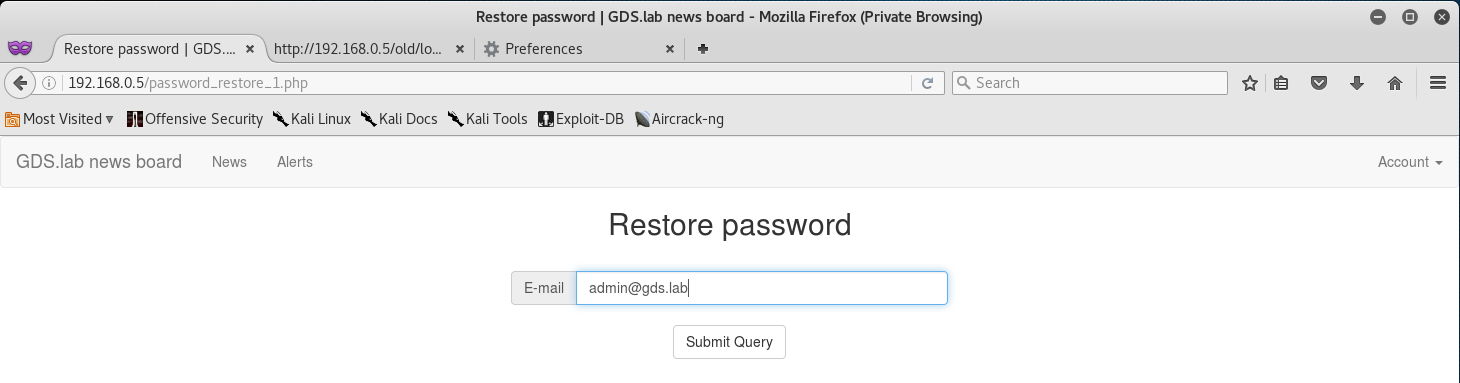
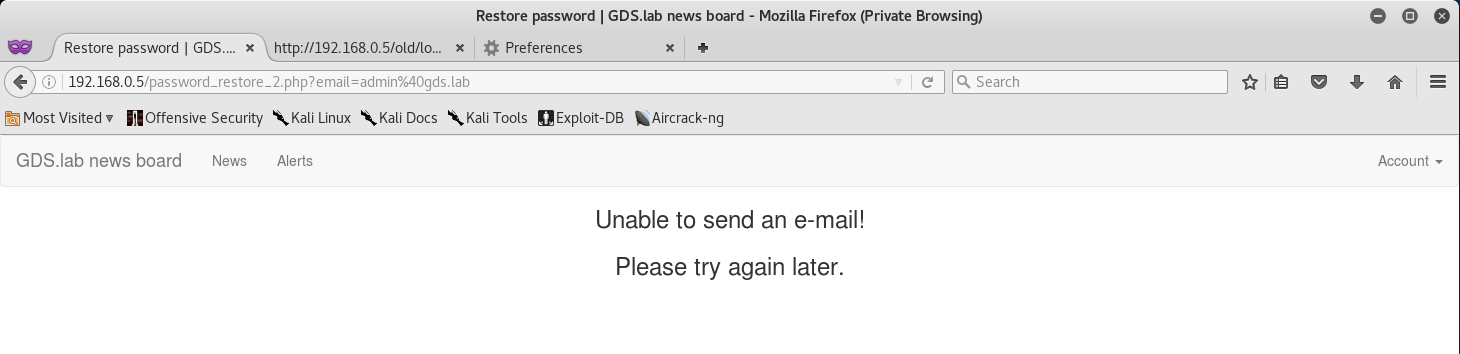
Maybe we can try restoring the password from the drop down menu?
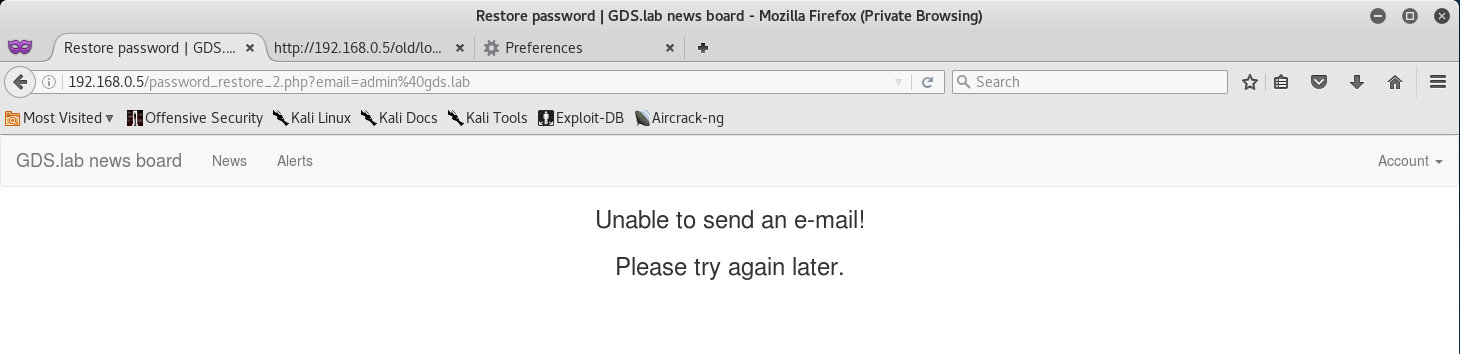
But unfortunately just typing the email leads us to an error.
At this point I decided to run Nikto against the website to find any exploits, misconfigurations, or hidden directories.
Mind you - if you run Nikto you have to route the scan through the SSH tunnel via our proxy!
root@kali:~# nikto -h http://192.168.0.5 -useproxy http://localhost:8080
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.0.5
+ Target Hostname: 192.168.0.5
+ Target Port: 80
+ Proxy: localhost:8080
+ Start Time: 2017-01-25 16:46:07 (GMT-6)
---------------------------------------------------------------------------
+ Server: nginx
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Cookie PHPSESSID created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-3092: /old/: This might be interesting...
+ 7547 requests: 6 error(s) and 5 item(s) reported on remote host
+ End Time: 2017-01-25 17:01:58 (GMT-6) (951 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Exploiting Old Login Functionality:
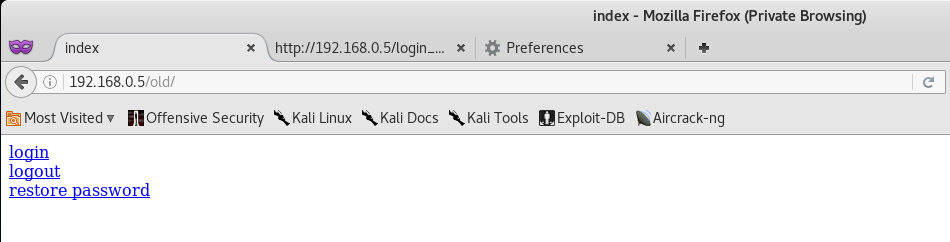
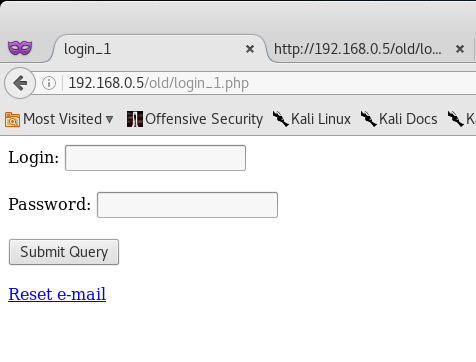
Initial reviews of the scan show that there is a hidden directory called /old/ which might be of interest to us. Let’s go ahead and navigate to it.
Alright, so we have 3 links to login, logout and restore a password. Let’s go ahead and follow the login link.
Okay - so we have to login. I decided to quickly check the source code and see if there isn’t anything interesting that the authors might have left behind.
<!DOCTYPE html>
<head>
<title>login_1</title>
</head>
<body>
<form action="login_2.php" method=GET>
Login: <input type=text name="username" />
<br><br>
Password: <input type=text name="password" />
<br><br>
<input type=submit>
</form>
<!-- remember to add simple user, too -->
<br>
<a href="reset.php">Reset e-mail</a>
</body>
The thing that really caught my eye here was the comment <!-- remember to add simple user, too -->. Huh… is it possible that they created an account with the username of user@gds.lab and password of user?
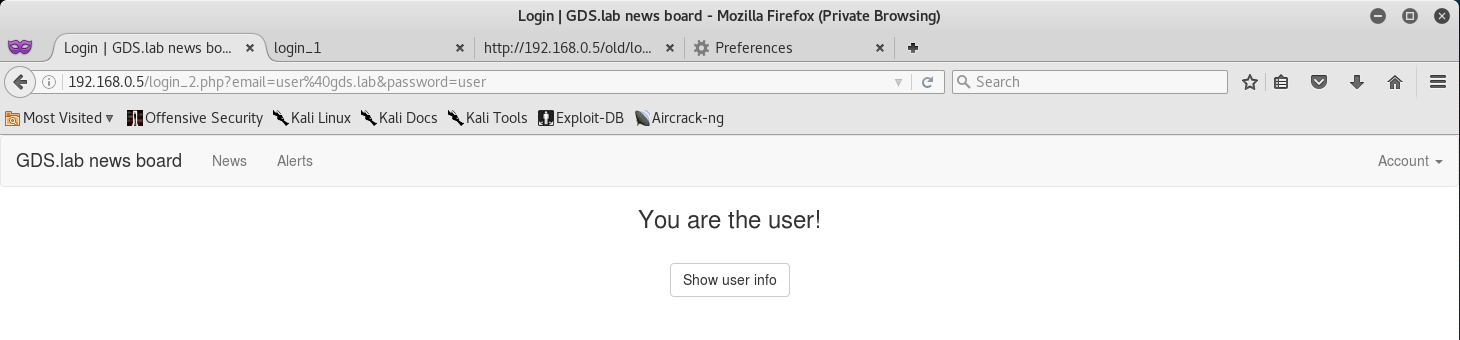
Let’s go back to the main login page and see if we can’t login with user@gds.lab:user.
Awesome! It seems that we have access to the user account with the weak password of user.
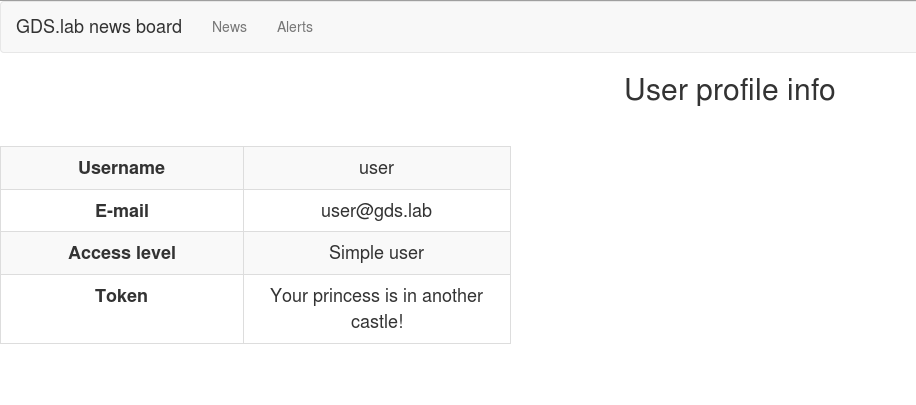
I also noticed that there is a Show user info button - so I clicked that and noticed that the token wasn’t there!
The princess is in another castle? What… what are we playing? Mario?
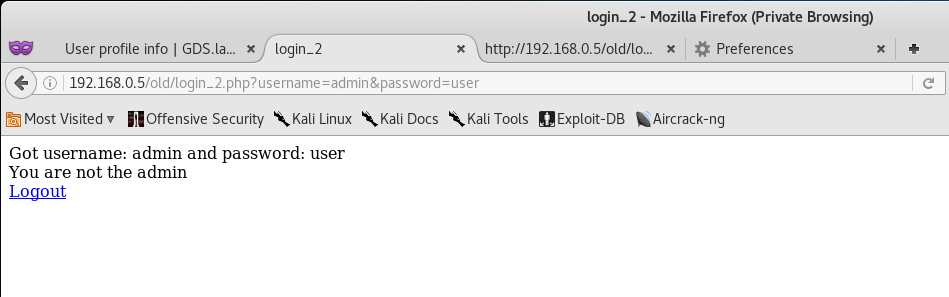
At this point I decided to go back to the /old/ directory and attempt logging in with admin:user.
So it seems the login worked… somehow. Unfortunately this dosen’t help us at all.
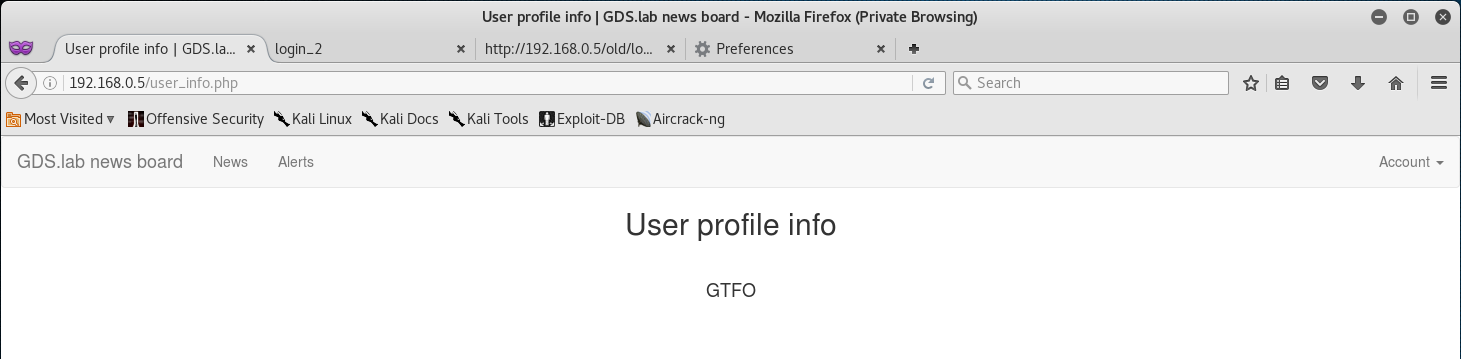
I decided to go back to the user info page and noticed something peculiar.
Finding the News Token:
GTFO? Woah… okay, it seems that by logging in as admin in the /old/ directory caused some sort of change.
This might be due to an issue with Open Sessions and a vulnerability in the Sessions Management of the web application.
I decided to go back and restore the admins password via the restore function.
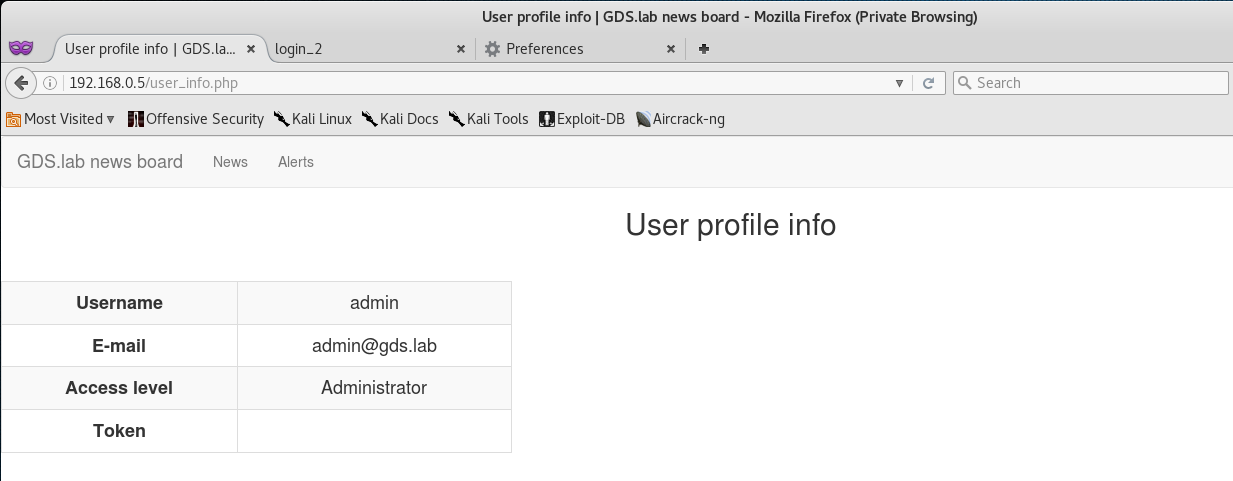
At this point, I went back to Show User Info and I was able to find the token!
Token (8/13):
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to compromise the News site via old login and reset functions to get the token!
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise Token (9/13) - The Hall of Fame Token!

Leave a Comment