In my previous post “Pentestit Lab v11 - Access Control Token (10/12)”, we carried out intelligence gathering on the Access Control machine, exploited a Command Injection Vulnerability, and found our tenth token. Today we will continue going back to machines we missed during our exploitation of the Main Office Subnet - which will include the following:
- Footprinting the 192.168.11.3 Machine
- Exploiting “Magic Hashes”
- Find the Help Desk Token
Footprinting the 192.168.11.3 Machine
You might be wondering at this point why we are even going back to the 192.168.11.3 Subnet even though we already compromised a machine there. Reason be is that the lab is full of machines that are either not interesting to us when working toward other tokens, or are either invulnerable.
Either way, we always have to make sure that we cover everything and continue enumerating machines, services, etc.
If you remember back our ClamAV token, we scanned the 192.168.11.x subnet, but we skipped one machine of interest.
Nmap scan report for 192.168.11.3
Host is up (0.0029s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
80/tcp open http nginx
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
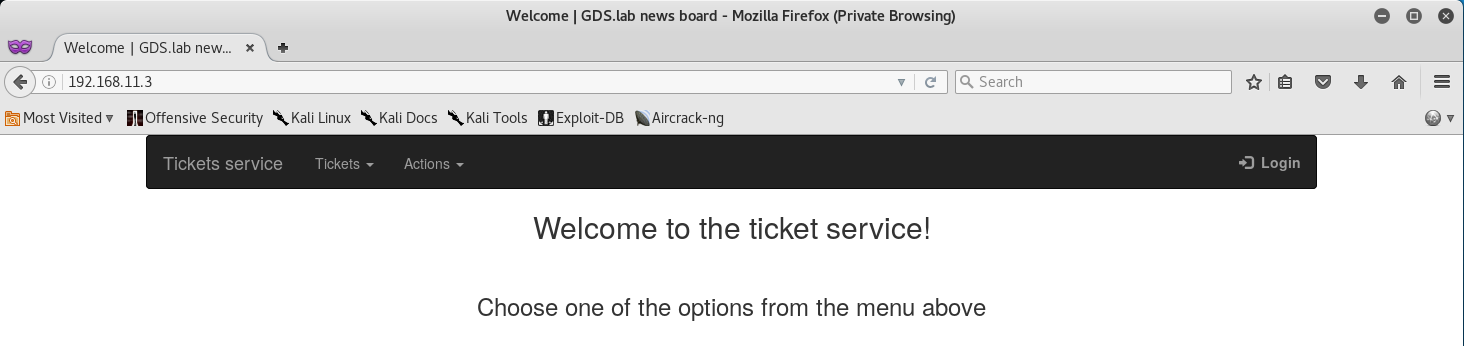
As you can see, 192.168.11.3 is running an Nginx server over TCP/80 - so let’s go back and investigate that machine via our web browser.
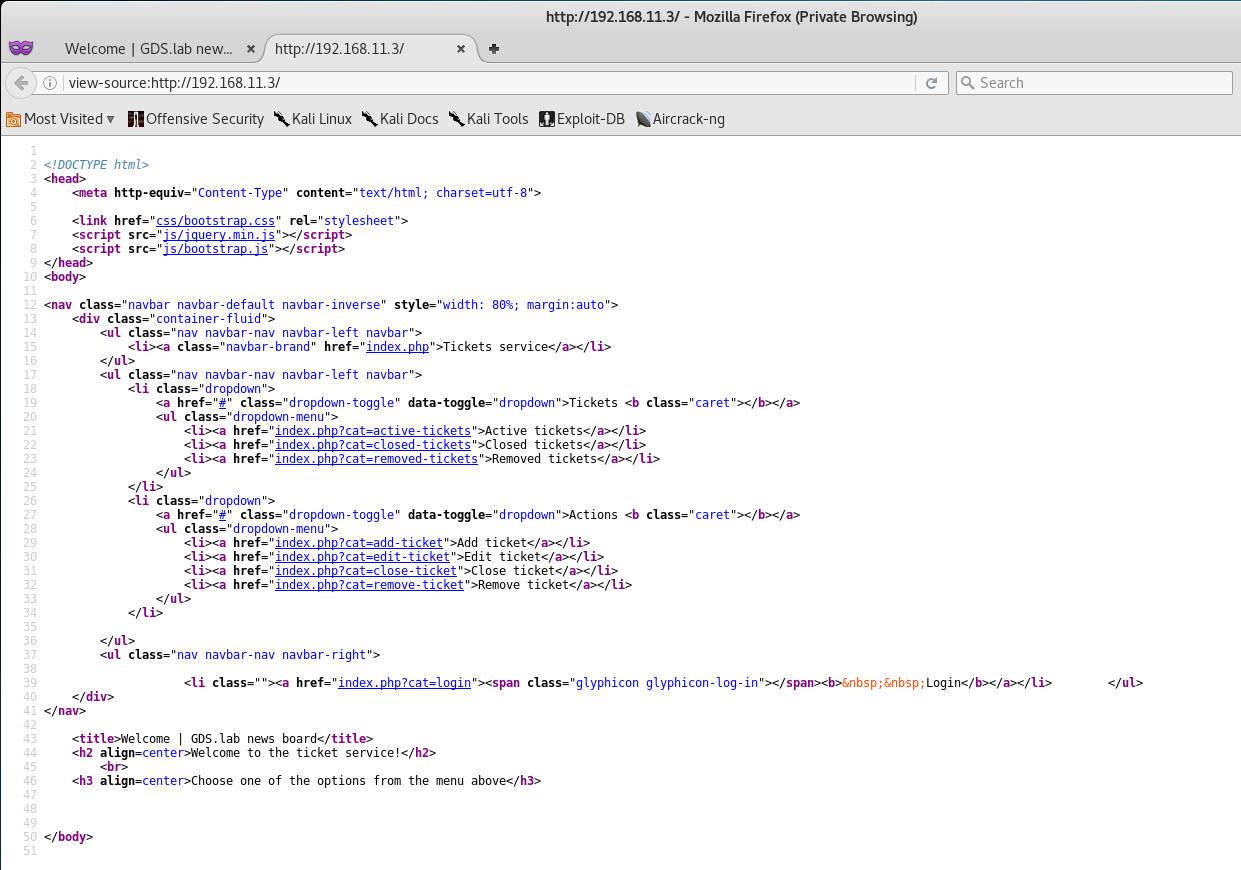
Interesting, this seems to be a ticket service of some kind. We see we have a drop down for Tickets, Actions, and a Login. Let’s start by viewing the source code for “low hanging fruit”.
Okay, so it seems we found a few drop down functions. Active Tickets, Add Ticket, and Close Ticket. Let’s attempt to add a ticket - maybe it will bode us some results.
Hmm, guess that won’t work - but at least we got the name of 4 valid logins we can use for later!
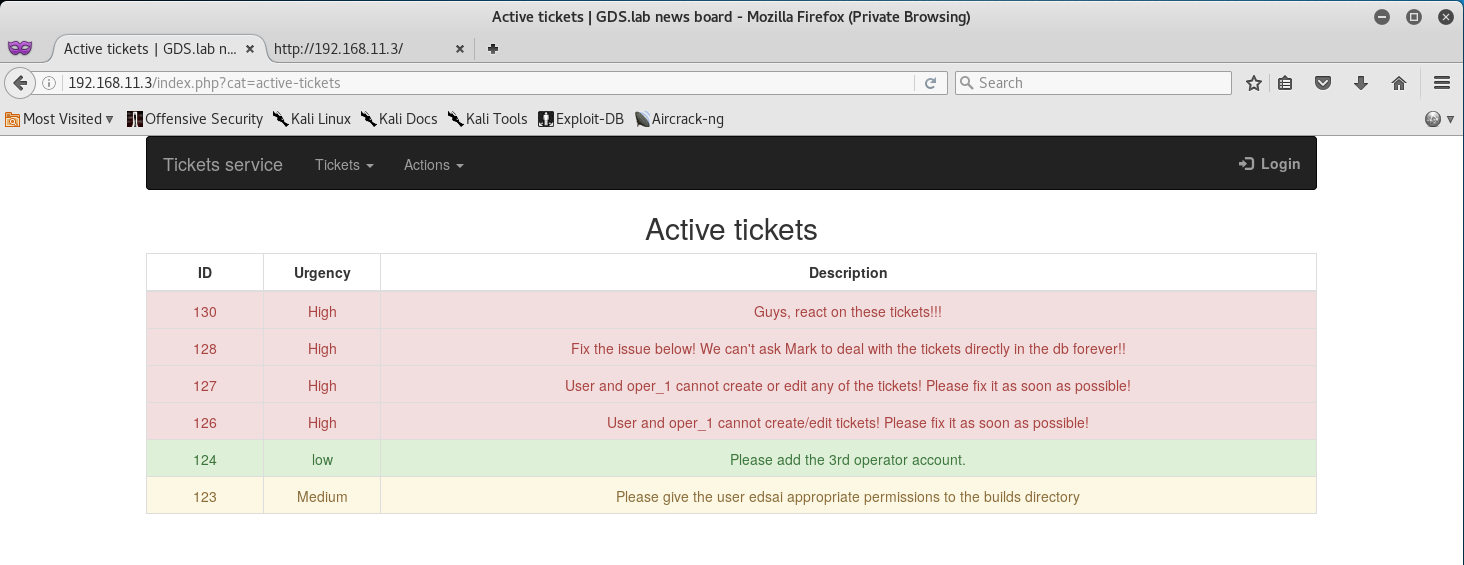
Let’s see what’s in Active Tickets - might find some disclosed information there!
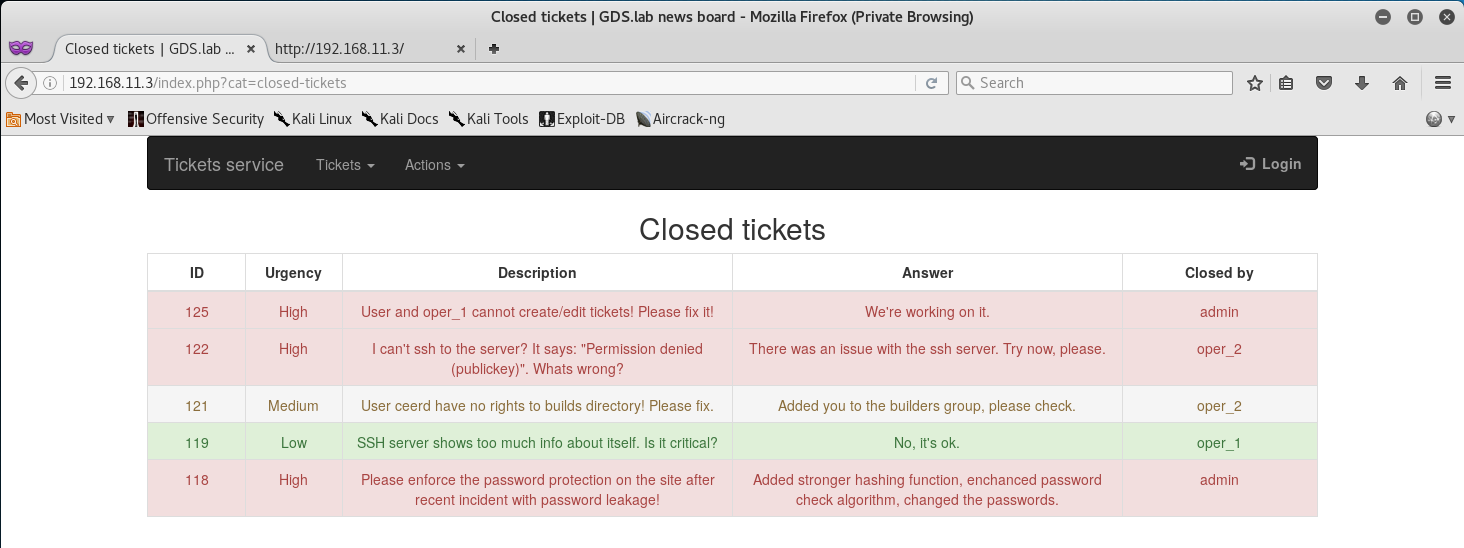
Well that gave us nothing, just some names, information about the accounts… ok, let’s try Closed Tickets!
Well, this gives us something to work with! It seems that the SSH Server is leaking information and is working for logins… but we don’t know for whom.
The one thing that really caught my attention was the last ticket - it’s stating that there was an incident with password leakage, and it also briefs over about adding a stronger hashing function, along with strong password check algorithms.
I decided to put my Google skills to the test and started looking for PHP Hashing Vulnerabilities.
Exploiting “Magic Hashes”
After some time spent Googling I came across a blog post about Magic Hashes.
I won’t get much into detail on this blog about it - so I highly suggest you go read the Blog on Magic Hashes and take the time to understand it.
Put simply, when using the “==” comparison operator in PHP and after hashing a password via PHP’s Base16 encoding, any password hash that starts with “0e…” will appear to match any string, thus allowing you to successfully log in to the admin account.
In the Blog there is a list of multiple Magic Hashes that by simply submitting the hash value in the login, the magic hash may collide with other hashes which both are treated as “0” and therefore compare to be true, which for us equals a valid login.
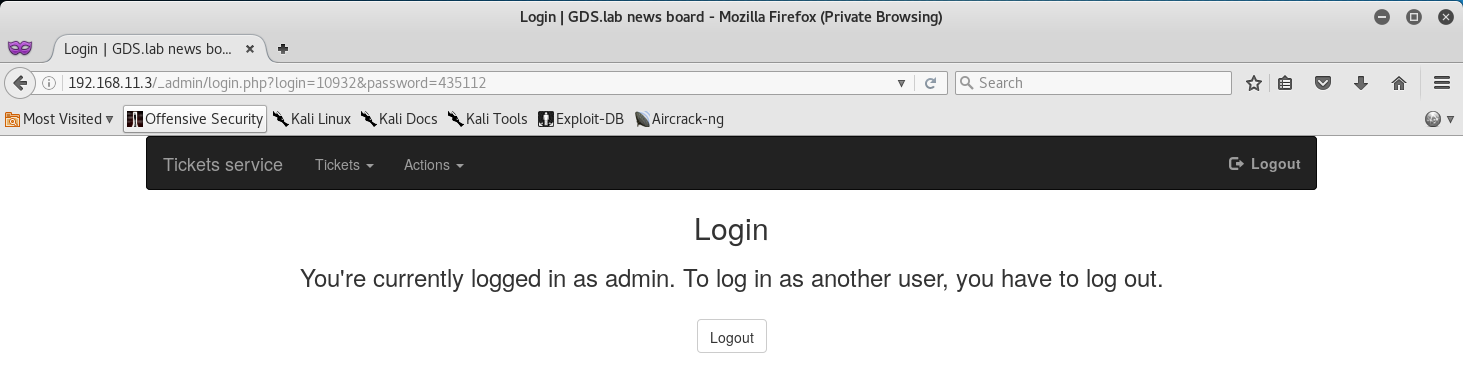
I attempted to try and divulge what hash I should use to login. Unfortunately if we attempted to go to the admin login page (found via Dirb) we would see a URL like so:
192.168.11.3/_admin/login.php?login=&password=
This is bad, because the hashes seem to be for passwords only, or for use as a token. I considered the fact that these hashes might be a combination of username+password and split them in half… well sort of half.
After multiple tries and a few hours spent banging my head against the table and pure dumb luck, I finally found the Magic Hash I needed! By splitting the “Magic” Number 10932435112 into two (10932 and 435112), I was able to login as the admin!
Find the Help Desk Token
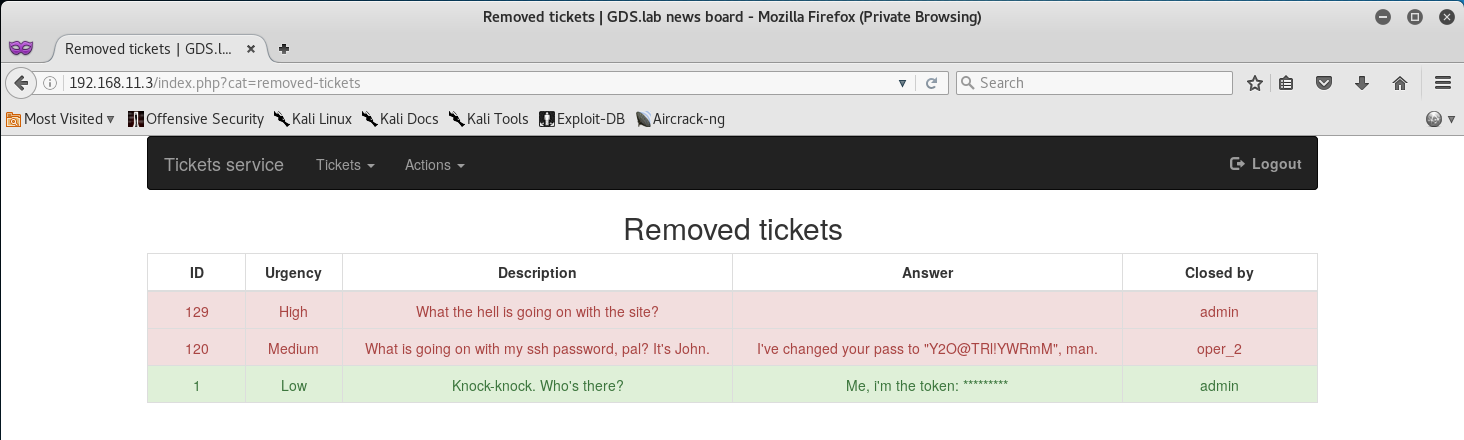
Once logged in, all we had to do was navigate to Removed Tickets from the Tickets drop down and we would find out Token, as well as a new SSH Password!
Token (11/12)
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to get the token via Magic Hashes!
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise our Final Token (12/12) - The Screen Token!

Leave a Comment