In my previous post “Pentestit Lab v11 - AD Token (4/12)”, we footprinted the AD server, utilized Pass the Hash by using our newly found hash for SMB Authetntication, and found our fourth token. Today we will continue our attack on the Main Office by attacking the CUPS Server - which will include the following:
- Footprinting the CUPS Server
- Exploiting a SQL Injection Vulnerability
- Finding the CUPS Token
- Finding an SSH Private Key
Footprinting the CUPS Server
From my previous post, after we compromised the AD server via SMB we found a file called network_test.txt.
root@kali:~/pentestit# cat network_test.txt
Hi, mate! Need to test ARP-table in DIR subnet.
I'll install intercepter admin:77_GrantedSuperAdmin_77
At this point we have credentialed access to something in the DIR Subnet, but unfortuantly we don’t have any VPN access to it. Thus, let’s continue attacking the Main Office to see if we can’t find anything that might help us gain access to the 192.168.0.252 router.
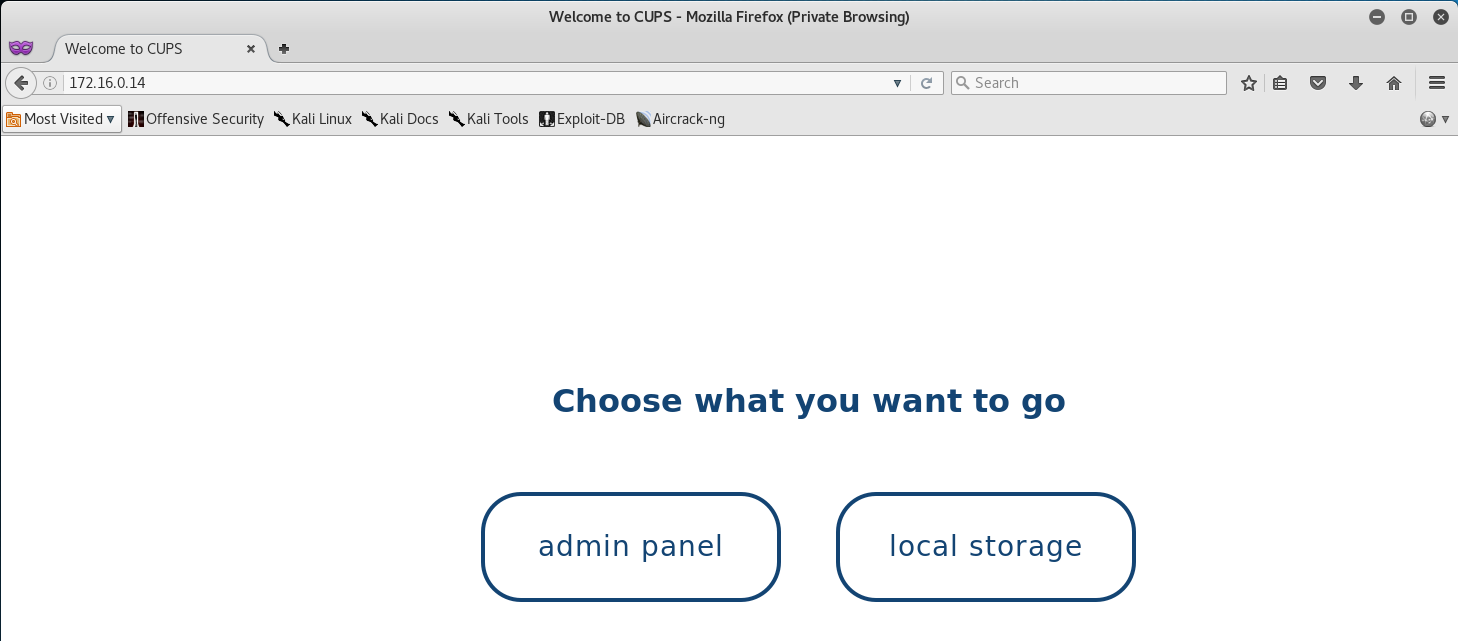
Looking at the Network Map we see that the CUPS Server is located in the Main Office using the IP of 172.16.0.14.
So, let’s fire up Nmap and scan the CUPS server to see what ports are open.
Nmap scan report for 172.16.0.14
Host is up (0.41s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
80/tcp open http nginx 1.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Alright, so it seems that TCP/80 is open, let’s navigate to 172.16.0.14 in our web browser and see what we got to work with.
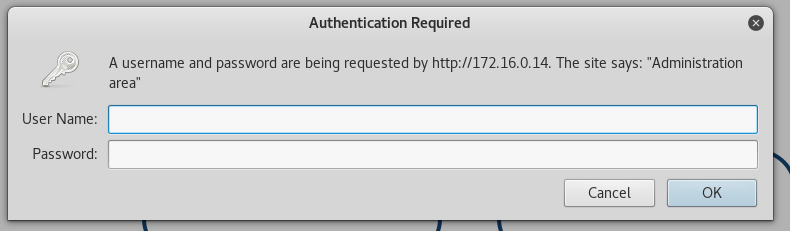
Right, so we have two options apparentlty - an admin panel and local storage. Upon accessing the admin panel we are prompted to enter a username and password.
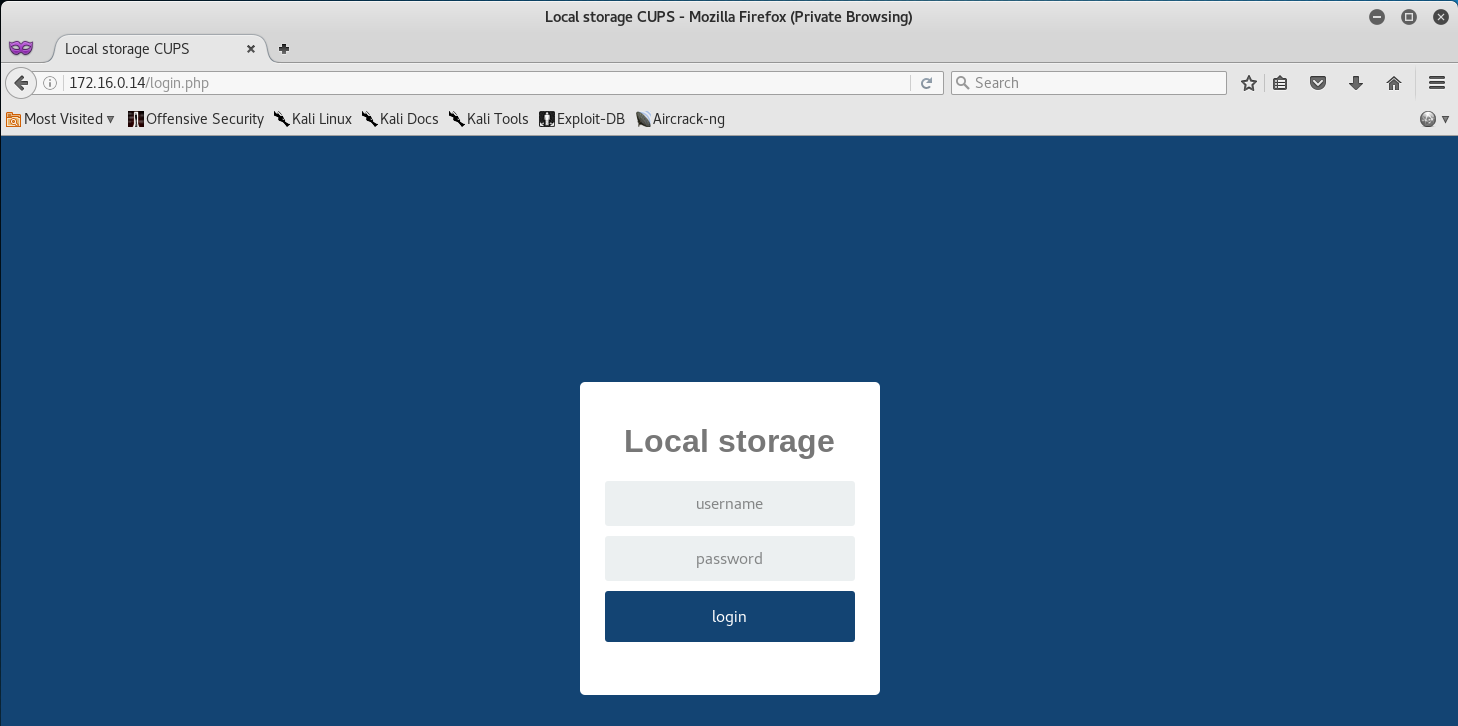
This seesm to be protected via htaccess, so I’ll skip out on trying to exploit this. Let’s move on and see what local storage has.
Intresting, this seems to be another login page being hosted via PHP… maybe there’s a SQL Injection here that we can exploit.
Exploiting a SQL Injection Vulnerability
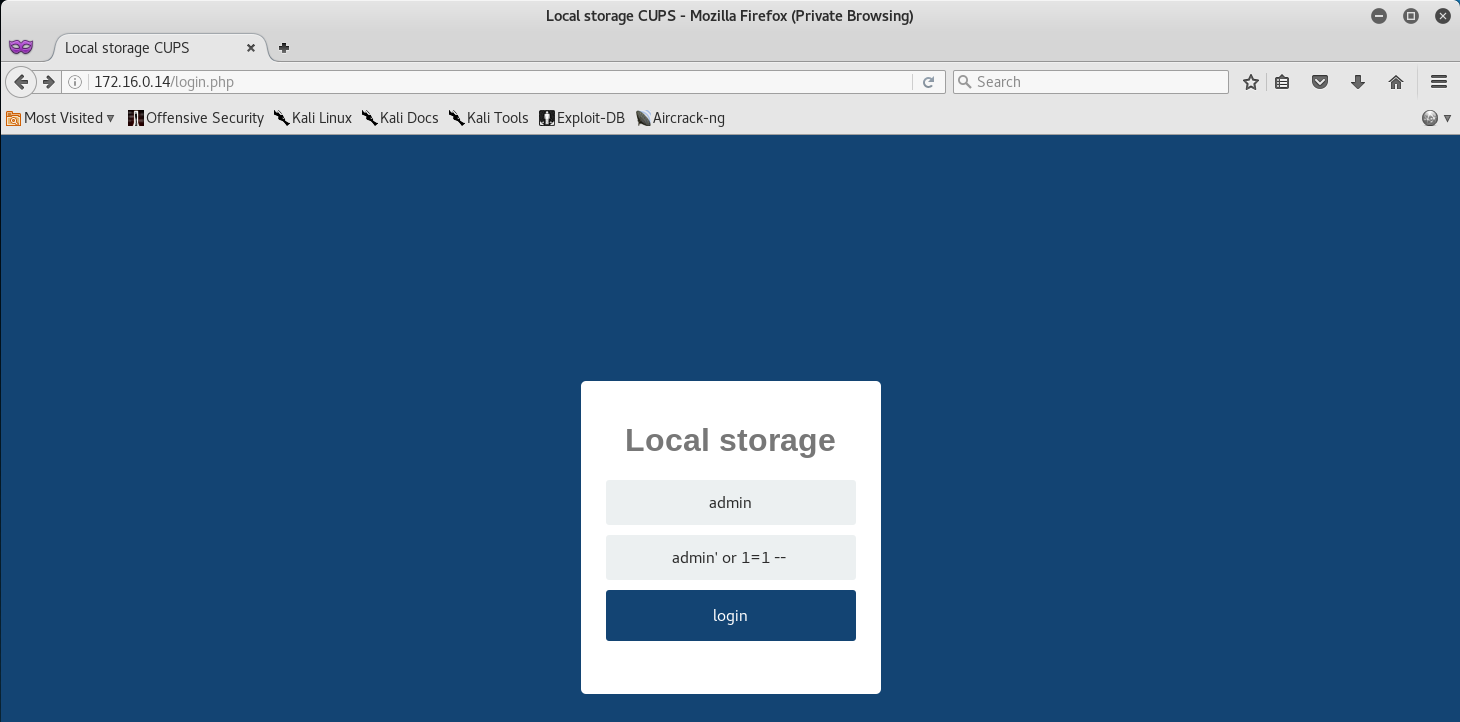
On the login page I attempted to do a simple SQL Injection in the password parameter for the username admin.
Once done, we are able to successfully login and view the local storage page.
Finding the CUPS Token
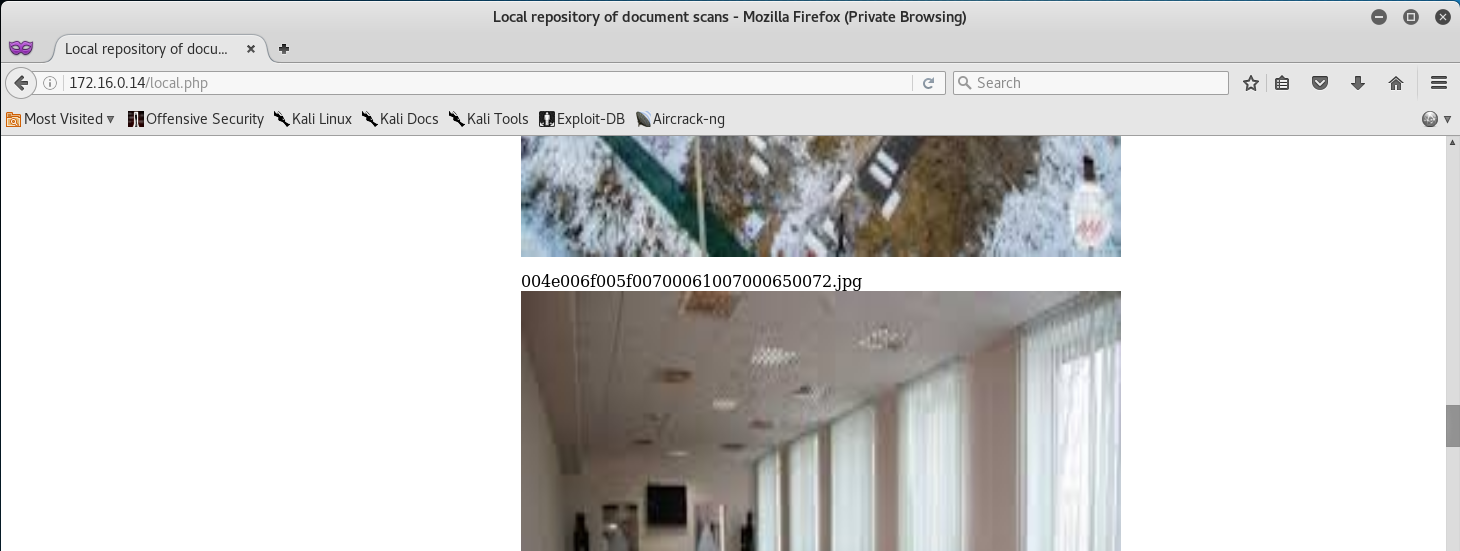
When scrolling through the Local Storage page on the CUPS Server we see that there is an image with a weird name.
I noticed that this seemed to be in Hexadecimal, thus I decided to convert it to ascii in my terminal.
root@kali:~# echo '004e006f005f00700061007000650072' | xxd -r -p
**********
Once done, the output will be our CUPS token!
Finding an SSH Private Key
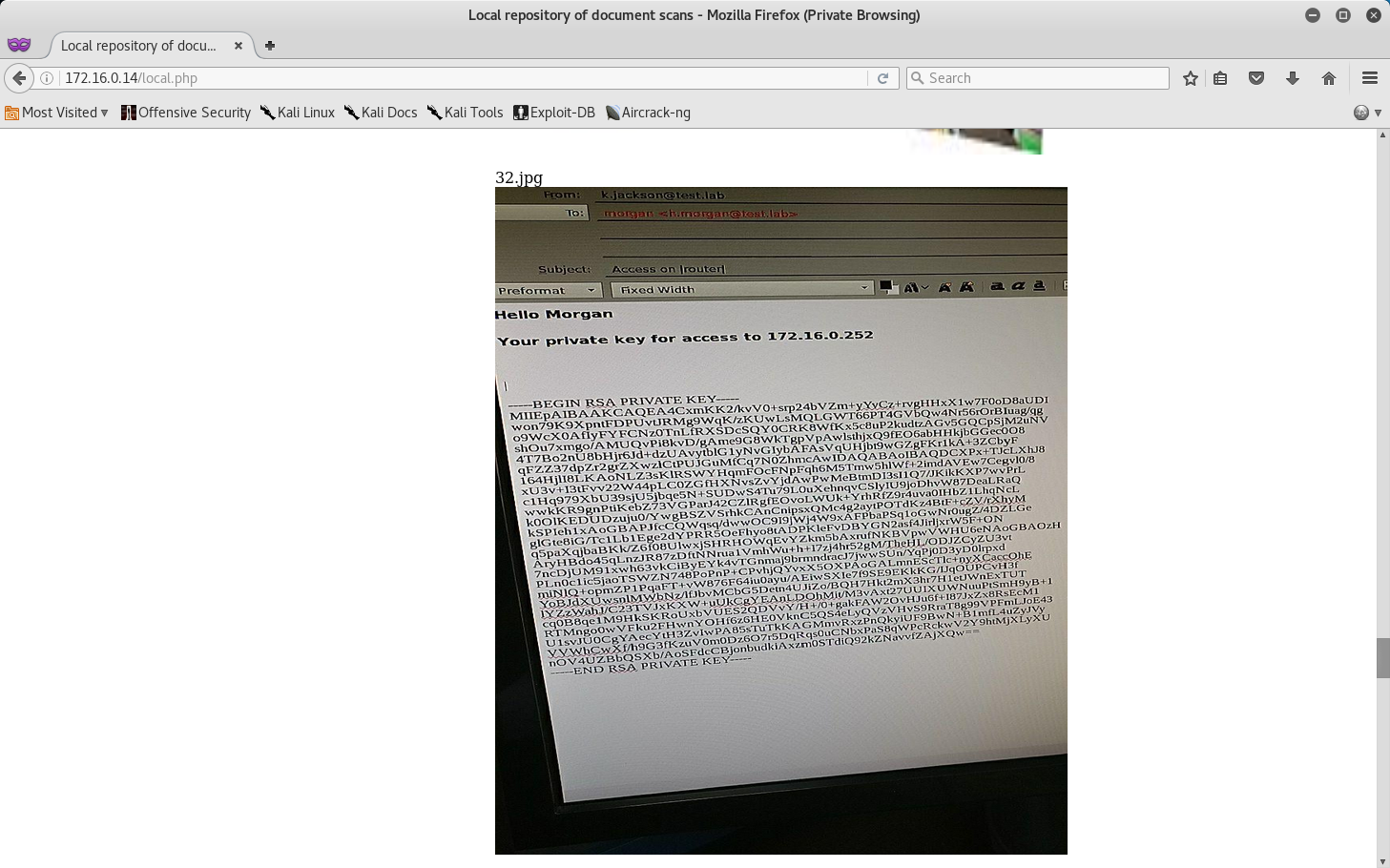
Now that we found our CUPS token, there is also an intresting picture of an SSH Key toward the bottom of the page.
Looking closely at this we see that this picture contains a private SSH Key for Morgan that allows us access to the 172.16.0.252 router, so we can utilize this to get access to the DIR Subnet!
Unfortuantly, there is now way to copy and paste this key straight to a text file… so after what seemed like an eternity, I typed out the whole key by hand!
root@kali:~/pentestit# gedit morgan.key
root@kali:~/pentestit# cat morgan.key
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEA4CxmKK2/kvV0+srp24bVZm+yYvCz+rvgHHxX1w7F0oD8aUDI
won79K9XpntFDPUvtJRMg9WqK/zKUwLsMQLGWT66PT4GVbQw4Nr56rOrBIuag/qg
o9WcX0AfIyFYFCNz0TnLfRXSDcSQY0CRK8WfKx5c8uP2kudtzAGv5GQCpSjM2uNV
shOu7xmgo/AMUQvPi8kvD/gAme9G8WkTgpVpAwlsthjxQ9fEO6abHHkjbGGec0O8
4T7Bo2nU8bHjr6Jd+dzUAvytblG1yNvGIybAFAsVqUHjbt9wGZgFKr1kA+3ZCbyF
qFZZ37dpZr2grZXwzlCtPUJGuMfCq7N0ZhmcAwIDAQABAoIBAQDCXPx+TJcLXhJ8
164HjlI8LKAoNLZ3sKlRSWYHqmFOcFNpFqh6M5Tmw5hlWf+2imdAVEw7Cegvl0/8
xU3v+I3tFvv22W44pLC0ZGfHXNvsZvYjdAwPwMeBtmDI3sI1Q7/JKikKXP7wvPrL
c1Hq979XbU39sjU5jbqe5N+SUDwS4Tu79L0uXehnqvCSlyIU9joDhvW87DeaLRaQ
wwkKR9gnPtiKebZ73VGParJ42CZlRgfEOvoLWUk+YrhRfZ9r4uva0IHbZ1LhqNcL
k0OlKEDUDzuju0/YwgBSZVSrhkCAnCnipsxQMc4g2aytPOTdKz4BtF+cZV/rXhyM
kSPIeh1xAoGBAPJfcCQWqsq/dwwOC9I9jWj4W9xAFPbaPSq1oGwNr0ugZ/4DZLGe
glGte8iG/Tc1Lb1Ege2dYPRR5OeFhyo8tADPKleFvDBYGN2asf4JirljxrW5F+ON
q5paXqjbaBKk/Z6f08UlwxjSHRHOWqEvYZkm5bAxrufNKBVpwVWHU6eNAoGBAOzH
AryHBdo45qLnzJR87zDftNNrualVmhWu+h+I7zj4hr52gM/TheHL/ODJZCyZU3vt
7ncDjUM91xwh63vkCiByEYk4vTGnmaj9brmndracJ7jwwSUn/YqPj0D3yD0lrpxd
PLn0c1ic5jaoTSWZN748PoPnP+CPvhjQYvxX5OXPAoGALmnEScTlc+nyXCaccOhE
miNlQ+opmZP1PqaFT+vw876F64iu0ayu/AEiwSXIe7f9SE9EKkKG/IJqOUPCvH3f
YoBIdXUwsnlMWbNz/lfJbvMCbG5Detn4UJiZo/BQH7Hht2mX3hr7H1etJWnExTUT
lYZzWahI/C23TVJxKXW+uUkCgYEAnLDOhMit/M3vAxt27UUIXUWNuuPtSmH9yB+1
cq0B8qe1M9HkSKRoUxbVUES2QDVvY/H+/0+gakFAW2OvHJu6f+I87JxZx8RsEcM1
RTMngo0wVFku2FHwnYOHf6z6HE0VknC5QS4eLyQVzVHvS9RraT8g99VPFmLKoE43
U1svJU0CgYAecYtH3ZvIwPA85sTuTkKAGMmvRxzPnQkyjUF9BwN+B1mfL4uZyJVy
VVWhCwXf/h9G3fKzuV0m0Dz6O7r5DqRqs0uCNbxPaS8qWPcRckwV2Y9htMjXLtXU
nOV4UZBbQSZb/AoSFdcCBjonbudkiAxzm0STdiQ92kZNavvfZAjXQw==
-----END RSA PRIVATE KEY-----
Go ahead and save this key as morgan.key so we can use this in our next post!
Token (5/12)
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to compromise the CUPS server via SQL Injection!
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise Token (6/12) - The Director Token!

Leave a Comment