Over the past couple of weeks I’ve been doing a lot of CTFs (Capture the Flag) - old and new. And I honestly can’t believe what I’ve been missing out on. I’ve learned so much during this time by just playing the CTFs, reading write-ups, and even watching the solutions on YouTube. This allowed me to realize how much I still don’t know, and allowed me to see where the gaps in my knowledge were.
One of the CTFs that was particularly interesting to me was the Google CTF. The reason why I really liked Google’s CTF was because it allowed for both beginners and experts to take part, and even allowed people new to CTF’s to try their hands at some security challenges.
I opted to go for the beginner challenges to see where my skill level really was at - and although it was “mostly” easy, there were still some challenges that had me banging my head on the desk and Googling like a mad man. Even though the Google CTF was over and solutions were online, I avoided them at all costs because I wanted to learn the “hard way”.
These beginner challenges were presented in a “Quest” style with a scenario similar to a real world penetration test. Such a scenario is awesome for those who want to sharpen their skills, learn something new about CTFs and security, while also allowing them to see a real world value and impact.
Now, some of you might be wondering… “How much do I need to know or learn to be able to do a CTF?” or “How hard are CTFs?
Truth be told, it depends. Some CTFs can be way more complex than other, such as DEFCON’s CTF and even Google’s CTF can be quite complex and complicated - but not impossible! It solely depends on your area of expertise.
There are many CTF teams that have people who specialize in Code Review and Web Apps and can do Web Challenges with their eyes closed, but give them a binary and they won’t know there difference between the EIP and ESP. The same goes for others! Sure, there are people who are the “Jack of All Trades” and can do pretty much anything, but that doesn’t make them an expert in everything.
After reading this, you might be asking me - But I’ve never done a CTF before! How do I know if I’m ready to attempt one?
Honestly, you’ll never be ready! There will always be something new to learn, something new you have never seen before, or something challenging that pushes the limits of your knowledge, even as an expert! That’s the whole point of CTFs.
But, there are resources that can help you get started!

Let’s start by explaining what a CTF really is!
CTF Time does a good job at explaining the basics, so I’m just going to quote them (with some “minor” editing)!
Capture the Flag (CTF) is a special kind of information security competition. There are three common types of CTFs: Jeopardy, Attack-Defense and mixed.
Jeopardy-style CTFs have a couple of questions (tasks) which are organized in categories. For example, Web, Forensic, Crypto, Binary, PWN or something else. Teams compete against each other and gain points for every solved task. The more points for a task, the more complicated the task. Usually certain tasks appear in chains, and can only be opened after someone on the team solves the previous task. Once the competition is over, the team with the highest amount of points, wins!
Attack-defense is another interesting type of competition. Here every team has their own network (or only one host) with vulnerable services. Your team has time for patching and usually has time for developing exploits against these services. Once completed, organizers connects participants of the competition to a single network and the wargame starts! Your goal is to protect your own services for defense points and to hack your opponents for attack points. Some of you might know this CTF if you ever competed in the CCDC.
Mixed competitions may contain many possible formats. They might be a mix of challenges with attack/defense. We usually don’t see much of these.
Such CTF games often touch on many other aspects of security such as cryptography, steganography, binary analysis, reverse engineering, web and mobile security and more. Good teams generally have strong skills and experience in all these issues, or contain players who are well versed in certain areas.
LiveOverflow also has an awesome video explaining CTFs along with examples on each aspect - see below!
Overall, CTFs are time games where hackers compete agasint eachother (either in teams or alone) to find bugs and solve puzzles to find “flags” which count for points. The team with the most points at the end of the CTF is the winner!

Now that we have a general idea of what a CTF is and what it contains, let’s learn how we can get started in playing CTFs!
Once again, LiveOverflow has an amazing video explaining why CTF’s are a great way to learn hacking. This video was a live recording of his FSEC 2017 talk that aimed to “motivate you to play CTFs and showcase various example challenge solutions, to show you stuff you hopefully haven’t seen before and get you inspired to find more interesting vulnerabilities”.
There are also a ton of resources online that aim to teach you the basics of Vulnerability Discovery, Binary Exploitation, Forensics, and more, such as the following below:
- CTF Field Guide
- CTF Resources
- Endgame - How To Get Started In CTF
- CONFidence 2014: On the battlefield with the Dragons – G. Coldwind, M. Jurczyk
- If You Can Open The Terminal, You Can Capture The Flag: CTF For Everyone
- So You Want To Be a Pentester? <– Shameless plug because of resources! =)
Out of all these resources, I believe that CTF Series: Vulnerable Machines is honestly the BEST resources for CTFs.
It’s aim is mostly focused on how to approach Vulnerable VM’s like the ones on VulnHub and Hack The Box, but it still gives you a ton of examples and resources on how to find certain vulnerabilities, how to utilize given tools, and how to exploit vulnerabilities.
As I said time and time again, learning the basics will drastically help improve your skills. Once you get enough experience you’ll start to notice “patterns” in certain code, binaries, web apps, etc. which will allow you to know if a particular vulnerability exists and how it can be exploited.
Another thing that can help you prepare for CTFs is to read write-ups on new bugs and vulnerabilities. A ton of Web CTF challenges are based off of these bugs and vulnerabilities or are a variant of them - so if you can keep up with new findings and understand them, then you’re ahead of the curve.
The following links are great places to read about new bugs, and vulnerabilities. They are also a good place to learn how other’s exploited known bugs.
HINT: These links can also help you get into Bug Bounty Hunting!
- Hackerone - Hacktivity
- Researcher Resources - Bounty Bug Write-ups
- Orange Tsai
- Detectify Blog
- InfoSec Writeups
- Pentester Land - Bug Bounty Writeups
- The Daily Swig - Web Security Digest
Once we have a decent understanding of a certain field such as Web, Crypto, Binary, etc. it’s time we start reading and watching other people’s writeups. This will allow us to gain an understanding on how certain challenges are solved, and hopefully it will also teach us a few new things.
The following links are great places to read and watch CTF solutions:
- CTF Time - Writeups
- CTFs Github - Writeups, Resources, and more!
- Mediunm - CTF Writeups
- LiveOverflow
- Gynvael Coldwind
- Murmus CTF
- John Hammond
Now that you have the basics skills and know a little more about certain topics it’s time we find a CTF!
CTF Time is still one of the best resources for looking at upcoming events that you can participate in. You can go through the events and see what interests you! Once you choose something, follow the instruction to register and you’re done!
From there, all you need to do is just wait for the CTF to start, and hack away!
Okay, seems easy enough - but then again for a first time it’s still overwhelming! So what can we do to make our first CTF experience a good one?
Well, that’s where the Google CTF comes in!

As I stated before, the reason why I really liked Google’s CTF was because it allowed for both beginners and experts to take part, and even allowed people new to CTF’s to try their hands at some security challenges without adding too much pressure.
The Beginner Quest starts off with a little back story to “lighten” the mood and let the player know that, this is just a game. We aren’t competing for a million dollars, so take it easy and have fun!
The story is as follows:
Cakes… Throughout history they are long promised, not often delivered. Are they real?
Are they fabrications of an internal system long designed to tease and tempt you with promises of sweet confectionary goodness that will satisfy and delight? Or the realistic truth of the matter. A dark conspiracy involving many clandestine organizations that want to create content and context around the very existence of this delicacy.
Your task, uncover the truth, find the cake and show it to the world. Set the truth free.
You do not have to start this undermining of the Cake-World-Order (cWo) without any information. Our informants deep in the field (some no longer with us), have passed on intel about an operative within the cWo known as Wintermuted. Their home is a mess of old technologies, poor Operational Security (Op-Sec) and Internet of Things (IoT) devices that haven’t seen updates in decades, despite being released last year. Start with their rubbish bin! Surely there is a letter or toothpaste tube there with some information that’ll get you on the inside.
Your goal is to get the cake in the fridge… Where else would you put cake in your smart home?
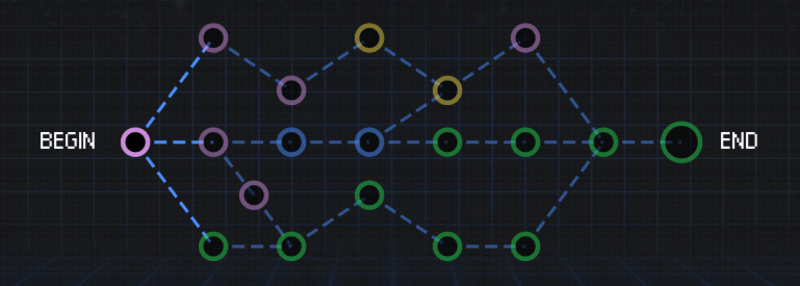
Once we read the story, we can start with the challenges. These beginner challenges were presented in a “Quest” style based off the story scenario. The quest has a total of nineteen (19) challenges as shown below in the quest map - with each color representing a different category as follows:
- Purple: Miscellaneous
- Green: Exploitation/Buffer Overflows & Reverse Engineering
- Yellow: Reverse Engineering
- Blue: Web Exploitation
If you click on one of the circles then you will go to the respective challenge. The challenge will contain some information, along with either an attachment or a link. From there, try to solve the challenge and find the flag, which is in the CTF{} format. Submitting the correct flag will complete the challenge.
Now notice how some of these challenges are “grayed out”. That’s because these challenges are “chained” to one another, meaning that you need to complete the previous one to be able to open the path to the next challenge.
Also notice that Google allows you to make choices on what challenge you want to do. They don’t force you to do all of them to get to the END, but give you the ability to pick and choose another path if something is too hard. Thus, making it easier for you to feel accomplishment and to later come back and learn!

Alright, that’s it for now. Hopefully you learned something new today and I sincerely hope that the resources will allow you to learn and explore new topics!
The posts following this will detail how I solved the 2018 Google CTF - Beginners Quest, so stay tuned and I hope to see you on the CTF battlefield someday!

Leave a Comment